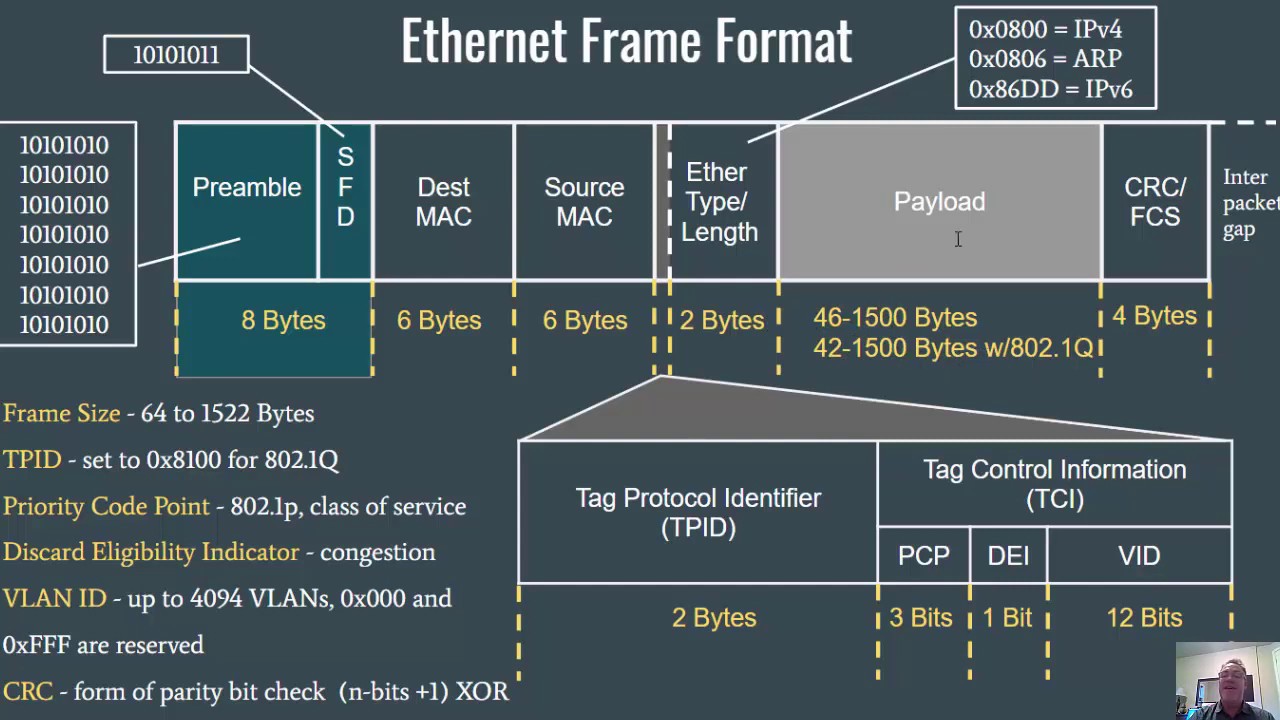
Cyclic Redundancy Check (CRC) - Part 1
Summary
TLDRIn this lecture on Cyclic Redundancy Check (CRC), we explored its role as an error detection technique in computer networks. The session outlined the steps for CRC generation, including appending bits to the original message and performing binary division with XOR operations. A practical example illustrated the process, showing how a data block and divisor can yield a CRC that is appended to the message for transmission. The lecture concluded with a homework assignment involving a polynomial divisor, encouraging further exploration of CRC's applications in error detection.
Takeaways
- 😀 Understanding CRC: Cyclic Redundancy Check (CRC) is a crucial error detection technique in computer networks.
- 😀 Four Methods: There are four primary error detection methods: VRC, LRC, checksum, and CRC.
- 😀 Role of Redundant Bits: CRC generates redundant bits that help the receiver identify errors in transmitted messages.
- 😀 Divisor Agreement: The sender and receiver must mutually agree on the divisor used for CRC calculations.
- 😀 Steps for CRC Generation: CRC generation involves four main steps: finding the divisor length, appending bits, performing binary division, and obtaining the remainder.
- 😀 Importance of XOR: The exclusive OR (XOR) operation is essential during binary division, influencing the calculation of the CRC.
- 😀 Example Walkthrough: A practical example demonstrated the CRC calculation using the data block 100100 and divisor 1101.
- 😀 Appending the CRC: The final CRC is appended to the original message, forming the complete transmitted data.
- 😀 Homework Assignment: Students are encouraged to find the CRC for a new data block with a polynomial divisor as a practice exercise.
- 😀 Polynomial Representation: When using polynomial expressions as divisors, converting them to binary form is necessary for CRC calculations.
Q & A
What is the main focus of this lecture?
-The lecture focuses on the cyclic redundancy check (CRC), specifically the generation of CRC on the sender's side.
What are the four error detection methods discussed in the previous lectures?
-The four error detection methods are Vertical Redundancy Check (VRC), Longitudinal Redundancy Check (LRC), checksum, and Cyclic Redundancy Check (CRC).
What are redundant bits in the context of CRC?
-Redundant bits in CRC are additional bits generated during error detection to help the receiver determine if an error occurred during data transmission.
What is the first step in generating CRC?
-The first step in generating CRC is to find the length of the divisor and denote it as L.
How many bits are appended to the original message during CRC generation?
-L minus one bits are appended to the original message, where L is the length of the divisor.
What operation is primarily used in the binary division for CRC generation?
-The exclusive OR (XOR) operation is primarily used in the binary division for CRC generation.
What does the remainder represent in the CRC generation process?
-The remainder obtained from the binary division represents the CRC code, which is appended to the original message.
In the example problem, what was the divisor used to find the CRC for the data block 100100?
-The divisor used in the example problem was 1101.
What is the final transmitted data after appending the CRC to the original message in the example?
-The final transmitted data after appending the CRC is 100100001.
What hint is given for solving the homework problem involving polynomial representation?
-The hint is to convert the polynomial expression into binary by identifying coefficients for each power of x, filling in zeros where necessary.
Outlines

此内容仅限付费用户访问。 请升级后访问。
立即升级Mindmap

此内容仅限付费用户访问。 请升级后访问。
立即升级Keywords

此内容仅限付费用户访问。 请升级后访问。
立即升级Highlights

此内容仅限付费用户访问。 请升级后访问。
立即升级Transcripts

此内容仅限付费用户访问。 请升级后访问。
立即升级浏览更多相关视频
5.0 / 5 (0 votes)