DOM XSS vs Reflected XSS - What's the Difference?
Summary
TLDRIn this tutorial, the speaker explains the difference between DOM-based XSS (Cross-Site Scripting) and reflected XSS. By using a lab example, they demonstrate how a DOM-based XSS attack occurs through JavaScript manipulating the Document Object Model (DOM), compared to reflected XSS where the attack is reflected directly in the HTTP response. The video highlights how attackers can inject malicious code into the DOM, bypassing security measures, and triggers an alert by exploiting the image tag's attributes. The video offers a clear explanation of the mechanics behind both attack types and how to execute a DOM-based XSS attack.
Takeaways
- 😀 **DOM-based XSS** occurs when malicious code is injected and executed on the client-side through DOM manipulation by JavaScript, without any direct server interaction.
- 😀 **Reflected XSS** happens when the server reflects back user-inputted malicious code in its HTTP response, executing the attack immediately after the user makes a request.
- 😀 DOM manipulation in the browser allows malicious code to be executed, based on inputs such as URL parameters or search terms, after the page has loaded.
- 😀 The **trackSearch** JavaScript function in the demo writes the user-supplied search term to the DOM using `document.write()`, which injects it into an image source tag.
- 😀 **Reflected XSS** is visible in the source code of the page (e.g., in URL query parameters), whereas **DOM-based XSS** changes the DOM dynamically and is not shown in the static HTML source code.
- 😀 The attack vector for DOM-based XSS involves breaking out of HTML attributes (like `src` in an `img` tag) and injecting new attributes (like `onload=alert()`).
- 😀 By using JavaScript's `document.write()` function, the search term is inserted into an image tag, which can then be exploited for XSS attacks.
- 😀 After a DOM-based XSS attack, inspecting the DOM reveals the changes made by JavaScript, but viewing the page source will not reflect these changes.
- 😀 In **DOM-based XSS**, the malicious code is only executed on the client-side once the page has finished loading, which makes it harder to detect during server-side analysis.
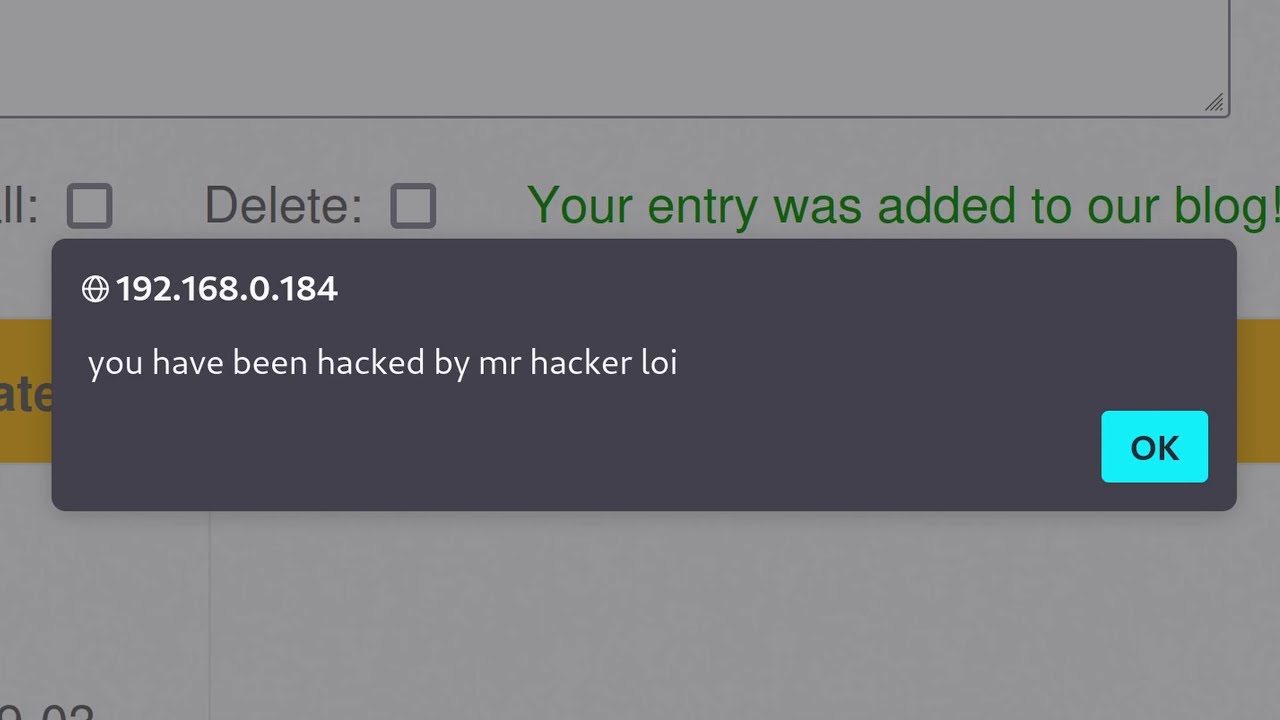
- 😀 The demo concludes with a successful execution of DOM-based XSS, showing how a malicious alert can be triggered through JavaScript manipulation of the DOM.
Q & A
What is DOM-based XSS?
-DOM-based XSS is a type of Cross-Site Scripting vulnerability that occurs when client-side JavaScript dynamically manipulates the Document Object Model (DOM) based on user input, leading to malicious content being executed in the browser.
How does DOM-based XSS differ from reflected XSS?
-In DOM-based XSS, the attack relies on manipulating the DOM through JavaScript after the page has loaded, without involving the server's HTTP response. In reflected XSS, the malicious content is immediately reflected by the server in its response, typically via the URL or HTTP request.
What role does JavaScript play in a DOM-based XSS attack?
-JavaScript is responsible for dynamically manipulating the DOM using user input, such as through functions like `document.write()`, which can be exploited by attackers to inject malicious content into the page.
What was the goal of the lab in the video?
-The goal of the lab was to perform a DOM-based XSS attack that triggers an alert function by exploiting the way user input is handled in the DOM using JavaScript.
What happens when the `document.write()` function is used in this context?
-The `document.write()` function writes content to the DOM based on the input passed to it. In the case of the lab, it writes an image tag with the search term embedded in the `src` attribute, which can later be manipulated for XSS.
What is the significance of the `window.location.search` property in the attack?
-The `window.location.search` property retrieves the query string from the URL (i.e., everything after the `?`), which is then parsed by JavaScript to extract the search term and display it in the DOM, making it a potential target for manipulation in a DOM-based XSS attack.
How does the injected malicious payload work in the lab example?
-The malicious payload injected in the search box breaks out of the `src` attribute of the image tag and adds an `onload` attribute, which triggers the `alert()` function once the image is loaded, executing JavaScript inside the browser.
Why is it important that the malicious content isn't visible in the page source?
-The fact that the injected script isn't visible in the page source emphasizes the difference between what is initially sent by the server and what gets dynamically manipulated by JavaScript in the DOM. This highlights the nature of DOM-based XSS, which can alter the page without leaving traces in the server response.
What security risks are posed by DOM-based XSS?
-DOM-based XSS poses security risks such as session hijacking, data theft, and the execution of malicious scripts in the user's browser, which can lead to further attacks like credential theft or malicious redirection.
What are some methods to prevent DOM-based XSS?
-Preventing DOM-based XSS involves practices like properly sanitizing user input, using Content Security Policy (CSP) headers, avoiding `document.write()` for dynamic content generation, and using JavaScript frameworks that provide built-in protection mechanisms against XSS.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Cross-Site Scripting (XSS) Explained

Cross-Site Scripting Attacks: What You Need to Know Now
Cross Site Scripting (XSS) tutorial for Beginners

7. DVWA | XSS (Stored) | Low-Medium-High-Impossible

Module 5.5 Lab Cross Site Scripting

How The Self-Retweeting Tweet Worked: Cross-Site Scripting (XSS) and Twitter
5.0 / 5 (0 votes)