Cross-Site Scripting Attacks: What You Need to Know Now
Summary
TLDRIn this 'Coffee with PR' session, the host delves into the world of application security, focusing on Cross-Site Scripting (XSS). The video explains the difference between client-side and server-side scripts, illustrating how XSS exploits client trust in servers. It differentiates between stored and reflected XSS attacks, providing examples and discussing their impacts. The host also covers prevention strategies, such as using HTTP-only and secure flags in cookies, and emphasizes the importance of secure coding practices and regular security assessments. The session ends with a teaser for the next video on Cross-Site Request Forgery (CSRF), inviting viewers to explore the nuanced differences between XSS and CSRF.
Takeaways
- 😀 The session focuses on application security, specifically discussing cross-site scripting (XSS) and its differences from CSRF.
- 🎥 The speaker introduces the series with a focus on subscriber feedback requesting more content on application security.
- 👤 XSS is a client-side vulnerability where an attacker injects malicious scripts into web content that is executed on the user's browser.
- 💻 The script explains the difference between client-side and server-side scripts, emphasizing that XSS is a client-side issue.
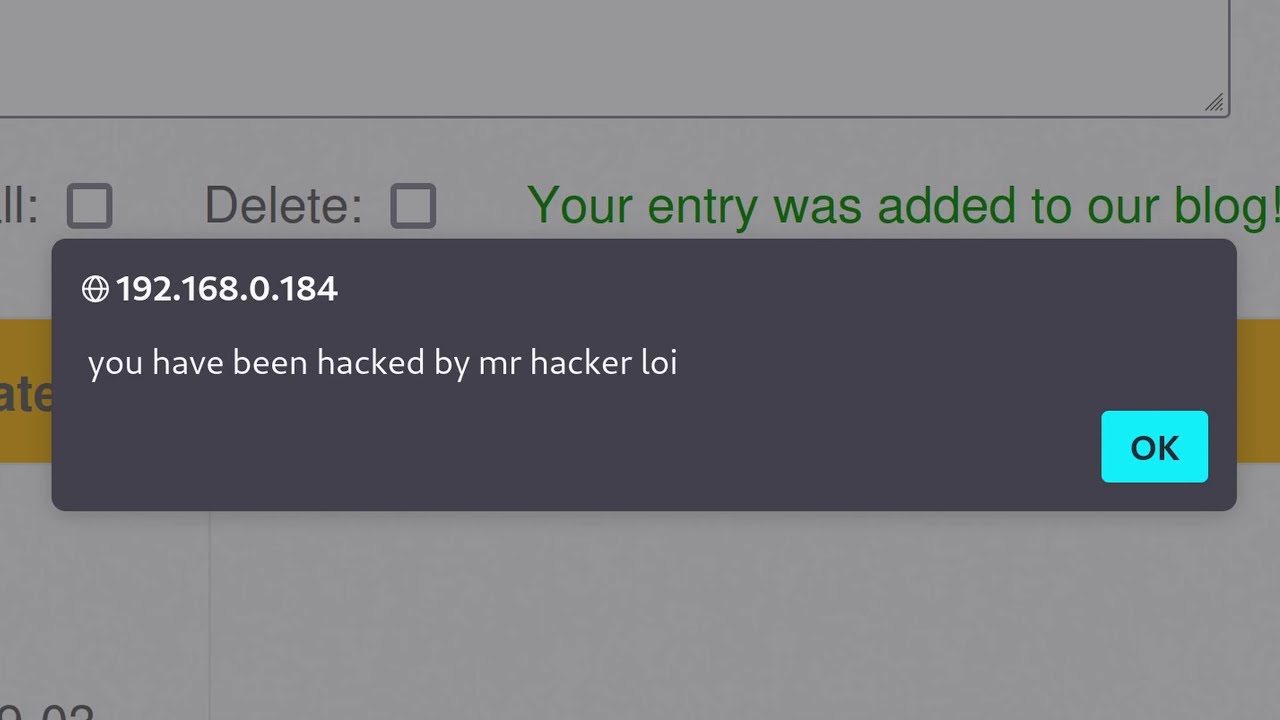
- 🔍 The speaker uses a diagram to illustrate how an attacker might exploit a vulnerability in a forum by injecting a malicious script that gets executed when a user visits the site.
- 📈 The video outlines the two types of XSS: stored and reflected, providing an example of each and explaining how they work.
- 🛡 To mitigate XSS, the speaker recommends using HTTP-only and secure flags in cookies to enhance security.
- 🔒 The HTTP-only flag prevents client-side scripts from accessing cookie data, while the secure flag ensures cookies are sent over HTTPS, protecting against man-in-the-middle attacks.
- 🔎 The script discusses methods for identifying XSS vulnerabilities, including manual testing, code review, and the use of automated scanning tools.
- 🛠 Prevention strategies include output encoding, implementing content security policies, and regular security assessments.
- ❓ The script anticipates common interview questions related to XSS, such as explaining the concept, differentiating between stored and reflected XSS, and demonstrating reflective XSS with a simple script.
Q & A
What is the main focus of the 'Coffee with PR' session discussed in the script?
-The main focus of the 'Coffee with PR' session is discussing cross-site scripting (XSS) as part of the application security series.
What is the difference between client-side and server-side scripts as explained in the script?
-Client-side scripts are executed on the user's browser and are used to improve website performance and user experience, such as form validation, image sliders, and interactive maps. Server-side scripts run on the server, fulfilling user requests, authenticating users, and processing data, with only the results sent to the client browser.
How does cross-site scripting exploit the trust between the client and the server?
-Cross-site scripting exploits the trust a client has in the server by injecting malicious scripts into web content. When the client's browser renders the web page, the malicious script is executed on the client side, potentially leading to data theft or other malicious activities.
What is the stored cross-site scripting attack as described in the script?
-Stored cross-site scripting is an attack where malicious scripts are permanently stored on the server and served to users viewing the content. An example is when an attacker posts a comment containing a malicious script on a blog, and every user who views the comment section has the script executed on their browser.
How does reflected cross-site scripting differ from stored cross-site scripting?
-Reflected cross-site scripting occurs when a malicious script is embedded in a URL and sent directly to the client via a phishing link. The script is not stored on the server but is executed immediately upon clicking the link, making it a non-persistent attack.
What are the two types of cross-site scripting attacks mentioned in the script?
-The two types of cross-site scripting attacks mentioned are stored and reflected. Stored attacks involve scripts permanently stored on the server, while reflected attacks involve scripts embedded in URLs and executed immediately upon user interaction.
How can HTTP only and secure flags in cookies help prevent cross-site scripting attacks?
-HTTP only flags restrict client-side script access to cookie data, preventing it from being stolen by malicious scripts. Secure flags ensure cookies are sent only over secure channels like HTTPS, reducing the risk of cookie theft in man-in-the-middle attacks.
What are some methods to identify if an application is vulnerable to cross-site scripting?
-Methods to identify vulnerabilities include manual testing with malicious payloads, code reviews to find places where user input could be rendered as HTML, and using automated scanning tools to detect potential XSS vulnerabilities.
What are the prevention strategies discussed in the script for cross-site scripting?
-Prevention strategies include output encoding to validate and properly handle user input, implementing content security policies, following secure coding practices, regular patching and updating of servers, conducting regular penetration testing, and using web application firewalls.
What are some common questions asked in application security jobs related to cross-site scripting?
-Common questions include explaining what cross-site scripting is and how it works, differentiating between stored and reflected XSS, identifying vulnerable code, demonstrating reflected XSS with a script, and discussing the implementation of content security policies.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)