7. DVWA | XSS (Stored) | Low-Medium-High-Impossible
Summary
TLDRThis tutorial explains Cross-Site Scripting (XSS) vulnerabilities in web applications and demonstrates how these attacks evolve across different security levels: low, medium, high, and impossible. The video covers how malicious scripts can be injected into input fields like guestbooks, leading to the theft of sensitive user data. By showcasing practical examples, it emphasizes the importance of properly sanitizing and validating user input to prevent XSS attacks. The tutorial highlights various defense strategies, from basic input filtering to advanced methods such as HTML encoding, offering valuable insights into securing web applications.
Takeaways
- 😀 XSS (Cross-Site Scripting) is a security vulnerability where malicious scripts are injected into a website, affecting the users who visit it.
- 😀 Reflected XSS occurs when a script is immediately reflected back to the user's browser without proper validation, leading to the execution of malicious JavaScript.
- 😀 At low security levels, websites often fail to filter or sanitize user inputs, making them vulnerable to XSS attacks.
- 😀 Medium security measures can sanitize inputs by removing special characters, but attackers can still bypass these filters using techniques like case variation and input length manipulation.
- 😀 High security measures provide better protection against XSS by sanitizing inputs more rigorously and using additional security measures such as Content Security Policy (CSP).
- 😀 At impossible security levels, input sanitization is fully enforced, ensuring that all user inputs are processed safely and are immune to XSS exploitation.
- 😀 Malicious JavaScript injections can take the form of pop-ups, session hijacking, or data theft, which can be triggered when the user interacts with a compromised webpage.
- 😀 To protect against XSS, websites must sanitize all user inputs by escaping special characters like `<`, `>`, and `&` to prevent them from being executed as code.
- 😀 Bypassing input sanitization can often be done by manipulating the input (e.g., using case sensitivity or changing input length), which still allows the script to be executed.
- 😀 The best practices to prevent XSS include using input sanitization, output escaping, security headers, and Content Security Policies to mitigate the risk of script execution on the client-side.
Q & A
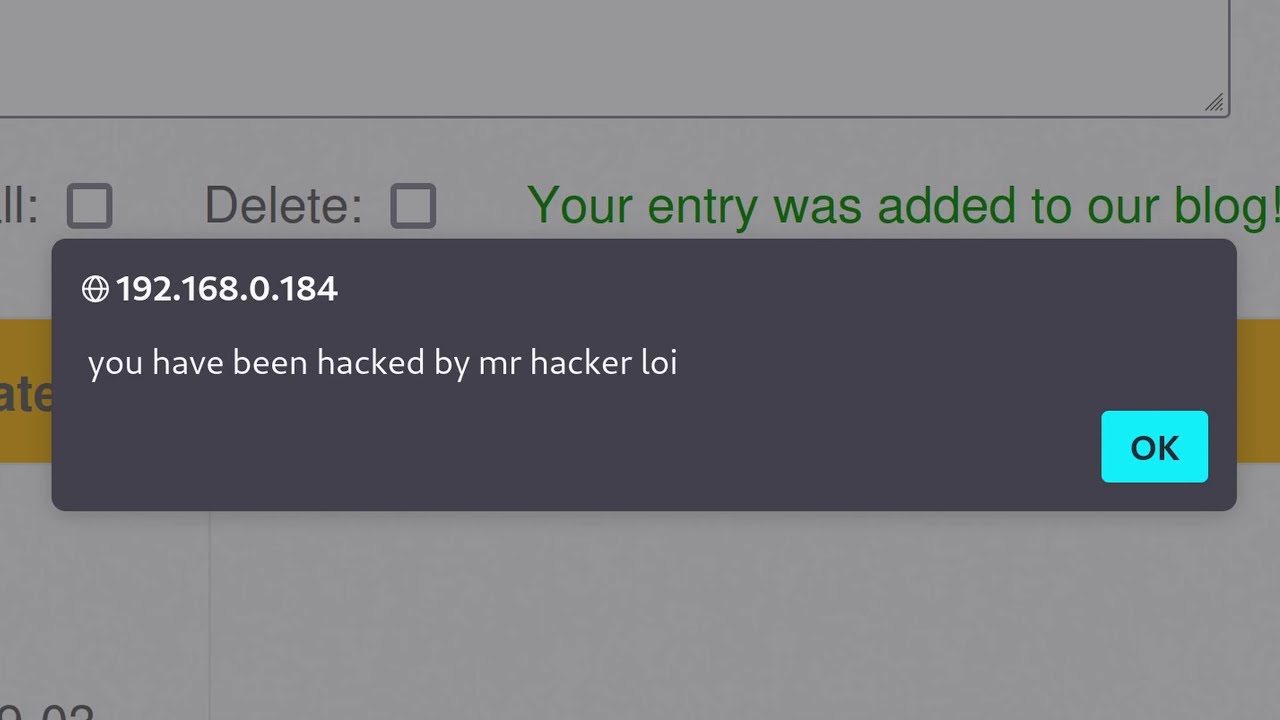
What is an XSS (Cross-Site Scripting) attack?
-An XSS attack occurs when a hacker injects malicious scripts, usually JavaScript, into a website's input fields, which are then executed in a user's browser. This can lead to data theft, session hijacking, and unauthorized access to sensitive information.
How does an XSS attack affect the user?
-An XSS attack can steal user data, hijack user sessions, and execute harmful actions on behalf of the user, such as redirecting them to malicious websites or performing unauthorized actions on their behalf.
What is the role of input sanitization in preventing XSS attacks?
-Input sanitization involves filtering out harmful input data, such as JavaScript code, before it is processed or stored by a website. This helps prevent attackers from injecting malicious scripts into a website's input fields.
How does input sanitization differ across various security levels?
-At lower security levels, input sanitization might be minimal or absent, allowing XSS attacks to be successful. At higher security levels, more rigorous sanitization and output encoding methods are applied to block harmful scripts. For instance, at the 'high' security level, both HTML special character handling and regex-based validation are used to filter inputs.
What is the significance of 'special character handling' in XSS protection?
-Special character handling ensures that any potentially dangerous characters (like `<`, `>`, or `&`) are properly encoded or replaced with their safe HTML equivalents. This prevents malicious scripts from being interpreted by the browser.
What security flaws are present at the 'medium' security level?
-At the 'medium' security level, some input fields are sanitized, but flaws remain, such as the case sensitivity in input validation. Attackers can bypass these protections by manipulating input sizes or using different character cases to circumvent filters.
How do hackers bypass XSS protections at the 'medium' security level?
-Hackers can bypass protections at the 'medium' security level by manipulating input length restrictions or using case-insensitive input. For example, changing the case of characters in a JavaScript function name or increasing the length of input beyond the system's default limits.
What happens at the 'high' security level in terms of XSS protection?
-At the 'high' security level, more advanced techniques are used, such as HTML entity encoding and regex-based input validation. This significantly reduces the chances of successful XSS attacks, though some vulnerabilities may still exist if special characters are not fully handled.
What is the 'impossible' security level, and how does it protect against XSS attacks?
-The 'impossible' security level represents the most robust protection against XSS attacks. It combines thorough input sanitization with output encoding before data is stored in the database. This ensures that even if attackers attempt to inject scripts, the system will prevent execution by encoding any potentially dangerous characters.
What is the purpose of using a guestbook form in the demonstration?
-The guestbook form is used to demonstrate how input fields on websites can be vulnerable to XSS attacks. By entering user input into the form, the presenter shows how malicious scripts can be injected and executed if proper security measures are not in place.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)