AWS IAM Core Concepts You NEED to Know
Summary
TLDRThis video offers a comprehensive guide to AWS Identity and Access Management (IAM), ideal for beginners and those needing a refresher. It covers core concepts like IAM's role in controlling resource access, the significance of policies and permissions, and the difference between users and roles. The script simplifies complex ideas, providing practical examples, such as creating a policy for Lambda functions and discussing trust relationships for cross-account access. It also shares valuable tips, like the importance of protecting the root account and adhering to the least privilege model, ensuring users gain a solid understanding of effectively utilizing IAM in AWS.
Takeaways
- 🔐 IAM stands for Identity and Access Management, a core AWS service that controls access to AWS resources.
- 👥 Users perform actions on resources, and authorization for these actions is determined by policies.
- 📜 A policy is a JSON document that specifies permissions for users or roles regarding AWS actions.
- 🚫 An 'Access Denied' error in AWS typically means the user does not have the required permissions specified in their policy.
- 🔑 Access keys and secret access keys are used for programmatic access to AWS and are crucial for CLI and SDK interactions.
- 👷 Roles in AWS are used to grant temporary access or permissions to users or applications, which can be assumed across account boundaries.
- 🔗 Trust relationships allow one AWS account to trust another, enabling cross-account access to resources.
- 🛡️ It's critical to protect the root account, as it has full access to all resources and should not be used for daily tasks.
- ❌ Explicit 'Deny' statements in policies will override 'Allow' statements, which is important for understanding access control.
- ⚖️ The least privilege model should be followed, granting only the necessary permissions to perform specific tasks.
Q & A
What does IAM stand for in AWS and what is its primary function?
-IAM stands for Identity and Access Management. Its primary function is to help control access to resources within AWS.
What are resources in the context of AWS IAM?
-Resources in AWS IAM are entities that you create in AWS, such as an S3 bucket, an S3 object, Lambda functions, or DynamoDB tables.
What is an action in AWS IAM and how does it relate to user permissions?
-An action in AWS IAM refers to specific operations that a user can perform, such as 's3:createBucket'. Authorization to perform an action depends on the policies attached to the user.
Can you explain what a policy in AWS IAM is and its significance?
-A policy in AWS IAM is a JSON document that specifies what a user or role can and cannot do within AWS. It is significant as it defines the permissions and access control for AWS resources.
What is the difference between an implicit deny and an explicit deny in AWS IAM?
-An implicit deny in AWS IAM is when no permissions are specified for an action, resulting in access being denied by default. An explicit deny is when a 'Deny' effect is explicitly set in a policy statement, preventing access to a specific action.
How can a user be granted permission to perform an action in AWS?
-A user can be granted permission to perform an action in AWS by associating a policy document with the user that includes an 'Allow' effect for the desired action.
What are the three common ways to interact with AWS and how do they relate to IAM policies?
-The three common ways to interact with AWS are through the AWS console, the AWS CLI, and programmatically using the AWS SDK. In all cases, permissions to perform actions are evaluated against the IAM policy documents associated with the user.
What are access keys and secret access keys in AWS, and why are they important?
-Access keys and secret access keys are alphanumeric strings used to interact with AWS programmatically. They are important as they serve as the credentials for API calls, and their security is crucial for protecting access to AWS resources.
Can you describe the structure of a policy document in AWS IAM?
-A policy document in AWS IAM consists of a version, one or more statements, each with a unique SID, an effect (Allow or Deny), an action, and a resource. It may also include conditions that further refine the policy's applicability.
What is the purpose of groups in AWS IAM and how do they simplify user management?
-Groups in AWS IAM are used to organize users and assign a default set of policies to all members of the group. This simplifies user management by allowing administrators to assign permissions to groups rather than individual users.
How do roles in AWS IAM differ from users and what is their primary use case?
-Roles in AWS IAM are similar to users in that they have associated policies, but they are designed to be assumed by entities, either users or applications, to grant temporary, scoped access to resources. Their primary use case is for cross-account access or granting permissions to applications.
What are trust relationships in AWS IAM and why are they necessary?
-Trust relationships in AWS IAM are necessary when you need to grant access to resources across different AWS accounts. They establish a relationship where one account trusts another account's users or roles to assume roles with specific permissions.
What are some best practices when working with AWS IAM that were mentioned in the script?
-Some best practices mentioned include protecting the root account, ensuring that explicit deny effects override allow effects in policies, following the least privilege model by specifying the least amount of access needed, and using the policy simulator for debugging access issues.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

CLF C02 - Module 07 : AWS Identity and Access Management

Create AWS EKS Cluster using Terraform: AWS EKS Kubernetes Tutorial - Part 2

Use AWS Command Line Interface CLI for creating, copying, retrieving and deleting files from AWS S3

CompTIA Security+ SY0-701 Course - 4.6 Implement and Maintain Identity & Access Management - PART A
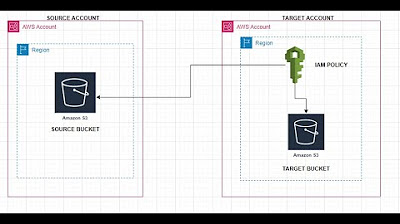
How to copy my s3 objects from one aws account to different aws account?
Chapter #8 - Cloud IAM Basics | identity & access management on google cloud platform (gcp)
5.0 / 5 (0 votes)