How Online Copy-Paste Could Expose Your Data #cybersecurity
Summary
TLDRThis educational video script discusses the potential security risks of using copy-paste websites to transfer code between machines. The speaker demonstrates how easily data can be intercepted and brute-forced on such websites, especially when sensitive information like API keys is involved. They also showcase a Python script that could be used to exploit these vulnerabilities, emphasizing the importance of using more secure methods for transferring sensitive data.
Takeaways
- 😀 The video is for educational purposes, discussing the risks of using copy and paste websites for transferring code.
- 🔒 The speaker demonstrates a method to transfer code from one machine to another without using email or other common methods.
- 📝 The process involves inputting data into a website which generates a four-digit code, which is then used to retrieve the data on another machine.
- 🚨 The speaker warns that such services can be insecure, especially if they lack proper authentication and authorization mechanisms.
- 🔑 There's a risk of sensitive information, such as API keys or database credentials, being exposed when using these services.
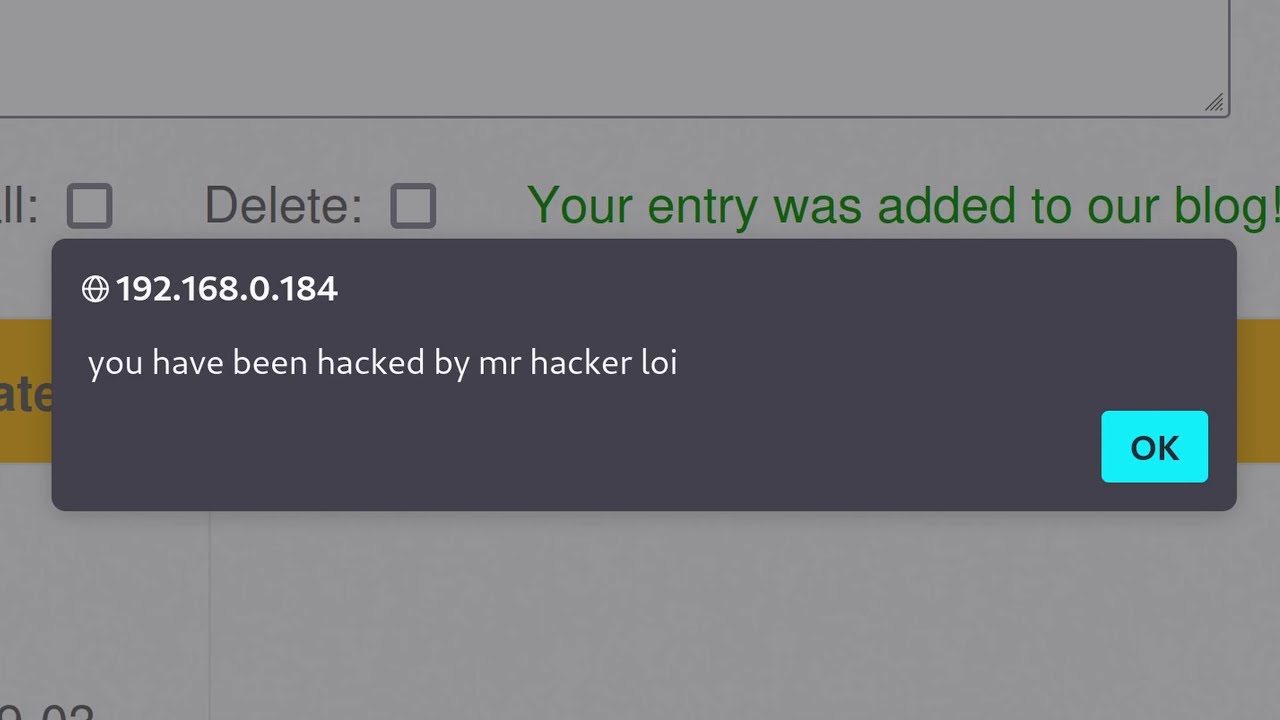
- 🕵️♂️ The video suggests that these services might be vulnerable to brute force attacks due to the short, guessable codes.
- 💻 The speaker shares a personal experience of brute forcing a copy and paste website and finding interesting, yet sensitive, data.
- 🛑 The video includes a demonstration of how to use a tool like Burp Suite to intercept and repeat requests to such a service.
- 🐍 A simple Python script is shown that can be used to automate the process of brute forcing these services to extract data.
- 🚫 The video advises against using such services for transferring sensitive information and suggests looking for more secure alternatives.
- 🔄 The speaker notes that even if a service claims to delete data after a valid code is entered, it might not be reliable.
Q & A
What is the main purpose of the video?
-The main purpose of the video is to demonstrate the potential risks associated with using copy and paste websites for transferring code or sensitive information between machines.
Why might someone use a copy and paste website to transfer code?
-A copy and paste website might be used when a person has a local machine without certain software installed, and they need to quickly transfer a piece of code from one machine to another without using email or other communication tools.
What is the vulnerability discussed in the video related to copy and paste websites?
-The vulnerability discussed is that these websites often use a simple four-digit code system that is easy to brute force, potentially exposing sensitive information such as API keys or database credentials.
What is brute forcing, and how does it relate to copy and paste websites?
-Brute forcing is a method of trying all possible combinations of a code to gain access to a system. In the context of copy and paste websites, it refers to the ease with which someone could try all 10,000 combinations of a four-digit code to access other users' data.
What is the potential risk of using such copy and paste services for developers?
-The potential risk is that developers might unknowingly expose sensitive information by pasting code that includes API keys, database credentials, or other sensitive data onto these services, which could then be accessed by malicious actors.
What demonstration does the video provide to show the vulnerability?
-The video demonstrates the ease of brute forcing a copy and paste website by showing how the presenter was able to access data from other users by simply trying different four-digit codes.
What is the presenter's recommendation for developers to avoid such risks?
-The presenter recommends that developers avoid using such services for sensitive information, and instead use more secure methods that require login and provide longer, harder-to-guess codes.
What is the role of the 'Intruder' tool in the demonstration?
-The 'Intruder' tool is used to automate the brute forcing process, showing how quickly and easily it can access data from the copy and paste website by trying multiple four-digit codes.
What is the presenter's stance on the security measures of the copy and paste website demonstrated in the video?
-The presenter's stance is that the security measures of the demonstrated copy and paste website are insufficient, as they lack proper authentication, authorization, and rate limiting to prevent brute forcing.
What additional insight does the video provide about the copy and paste website's behavior after a valid code is entered?
-The video suggests that the website's claim of automatically clearing data after a valid code is entered may not be reliable, as the presenter was able to access the same data multiple times after entering the code.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тариф5.0 / 5 (0 votes)