hping3 Tutorial - TCP SYN Flood Attacks - DoS and DDoS Attacks using Kali Linux 2022 and Windows XP
Summary
TLDRThis educational tutorial demonstrates the use of hping3 in Kali Linux to conduct SYN flood and other attack simulations against a Windows XP virtual machine. The instructor explains how to set up a controlled environment, scan for open ports, and execute various types of attacks while monitoring network and CPU utilization. Emphasizing the importance of understanding these concepts for security professionals, the video cautions against unethical use of these techniques and stresses that this knowledge is intended solely for educational purposes.
Takeaways
- 😀 The course focuses on network security and penetration testing using hping3 in Kali Linux.
- 😀 The training is purely educational, aiming to inform about SYN attacks and flood attacks without promoting hacking.
- 😀 Setting up a virtual environment is crucial for safe testing, isolating the machines from external networks.
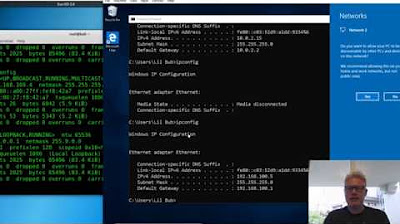
- 😀 Using 'ipconfig' and 'ifconfig' helps identify IP addresses for both the Windows XP and Kali Linux machines.
- 😀 Nmap can be employed to discover open ports on target machines, critical for understanding potential vulnerabilities.
- 😀 Hping3 can replace Nmap for port scanning and can be used to craft specific attack packets.
- 😀 The 'rand source' flag in hping3 helps mask the attacker's identity during penetration testing.
- 😀 SYN flood attacks can significantly increase CPU and network utilization on the target machine.
- 😀 A LAN attack using hping3 can freeze a target machine by flooding it with packets that disrupt normal operations.
- 😀 It's important to use these techniques responsibly and ethically, as unauthorized attacks can lead to serious legal consequences.
Q & A
What is the primary purpose of the tutorial on hping3?
-The tutorial aims to educate students about network security, specifically on understanding SYN and flood attacks using hping3 in a controlled environment.
How are the virtual machines configured for this demonstration?
-The virtual machines (Kali Linux and Windows XP) are configured using host-only adapters to ensure they only communicate with each other and not with external networks.
What commands are used to find the IP addresses of the machines?
-The command 'ipconfig' is used on Windows XP, and 'ifconfig' is used on Kali Linux to retrieve their respective IP addresses.
What is the purpose of using nmap in this tutorial?
-Nmap is used to scan the target machine (Windows XP) for open ports, helping to identify potential vulnerabilities.
What does a SYN flood attack involve?
-A SYN flood attack involves sending a large number of SYN packets to a target machine to overwhelm its resources and disrupt normal operations.
What effect does the flood attack have on the target machine's performance?
-The flood attack significantly increases CPU and network utilization, potentially causing the machine to slow down or become unresponsive.
How does the 'rand source' flag function in hping3?
-The 'rand source' flag generates random source IP addresses for the packets sent, helping to obscure the identity of the attacker.
What is a LAND attack, and how is it executed?
-A LAND attack, or Local Area Network Denial attack, is executed by sending packets where the source and destination IP addresses are the same, effectively freezing the target machine.
What precautions are highlighted regarding the use of hping3?
-The tutorial emphasizes that the information should only be used for educational purposes and warns against launching real attacks due to legal consequences.
What monitoring tools are suggested to observe the effects of the attacks?
-The performance monitor and task manager on Windows XP are suggested to monitor CPU and network activity during the attack simulations.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード関連動画をさらに表示

Cara install Kali Linux di virtualbox terbaru 2024!

Active Directory Project (Home Lab) | Part 5

DDoS Attack Explained | How to Perform DOS Attack | Ethical Hacking and Penetration Testing

Belajar Ethical Hacking Lengkap (Part 2) || Virtualization & Virtual Machine
How to Make Virtual Machines Talk to Each Other in VirtualBox

Get Usernames and Passwords with Ettercap, ARP Poisoning (Cybersecurity)
5.0 / 5 (0 votes)
