Uncovering Cyber Threats: EDR vs SIEM Comparison #cybersecurity #cyber #risk #threats #detective
Summary
TLDRThis video explores the distinctions between Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM). EDR acts as a security guard for individual devices, monitoring and responding to potential cyber threats in real-time. In contrast, SIEM aggregates and analyzes security data from across the network, offering a comprehensive view of network security. Understanding these tools' roles can enhance your cybersecurity strategy.
Takeaways
- 🔒 **EDR Focus**: Endpoint Detection and Response (EDR) is designed to protect individual devices from cyber threats.
- 👀 **EDR Function**: EDR continuously monitors and responds to suspicious activities on each device, acting as a security guard.
- 📊 **CM Overview**: Security Information and Event Management (SIEM), often referred to as CM, aggregates and analyzes security data across the network.
- 🔍 **CM Analysis**: CM pulls in logs and events from multiple sources to provide a comprehensive view of network security.
- 📈 **EDR vs CM**: While EDR is about real-time threat detection at the device level, CM focuses on overall security understanding through data analysis.
- 🛡️ **Security Strategy**: Understanding the differences between EDR and CM can help in building a more robust security strategy.
- 👨💻 **Device-Level Protection**: EDR is crucial for immediate threat detection and response at the device level.
- 🌐 **Network-Wide Perspective**: CM offers a broader perspective by analyzing security data from the entire network.
- 🔎 **Data Collection**: CM's strength lies in its ability to collect and analyze data from various sources to enhance security insights.
- 📚 **Educational Content**: The video serves as an educational resource for understanding complex cybersecurity concepts.
Q & A
What is Endpoint Detection and Response (EDR)?
-EDR is a security tool that focuses on protecting individual endpoints from cyber threats by continuously monitoring and responding to suspicious activities.
How does EDR function in comparison to other security tools?
-EDR functions by acting as a security guard for each device, providing real-time threat detection at the device level.
What is the primary role of Security Information and Event Management (SIEM)?
-SIEM's primary role is to aggregate and analyze security data from across the network, pulling in logs and events from multiple sources.
How does SIEM contribute to network security?
-SIEM contributes to network security by providing a comprehensive, big-picture view of the network's security status through data analysis.
What is the main difference between EDR and SIEM?
-The main difference is that EDR focuses on real-time threat detection at the device level, while SIEM focuses on comprehensive data analysis for overall security understanding.
Why are both EDR and SIEM important for a robust security strategy?
-Both EDR and SIEM are important because they offer different perspectives on security: EDR with real-time device-level threat detection and SIEM with a broader view of network security.
Can EDR and SIEM be used together in a security setup?
-Yes, EDR and SIEM can be used together to create a layered security approach, with EDR providing device-level protection and SIEM offering network-wide insights.
What kind of suspicious activities does EDR monitor?
-EDR monitors a range of suspicious activities, including unauthorized access, malware execution, and abnormal network behavior at the endpoint level.
How does SIEM help in identifying threats across the network?
-SIEM helps identify threats by correlating and analyzing logs and events from various sources, allowing for the detection of patterns or anomalies that may indicate a security breach.
What are some common sources of data that SIEM collects?
-Common sources of data for SIEM include firewall logs, intrusion detection system alerts, server logs, and application logs.
How can a viewer enhance their understanding of EDR and SIEM?
-A viewer can enhance their understanding of EDR and SIEM by exploring additional resources, such as whitepapers, case studies, and tutorials that delve deeper into the functionalities and use cases of these tools.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantVoir Plus de Vidéos Connexes
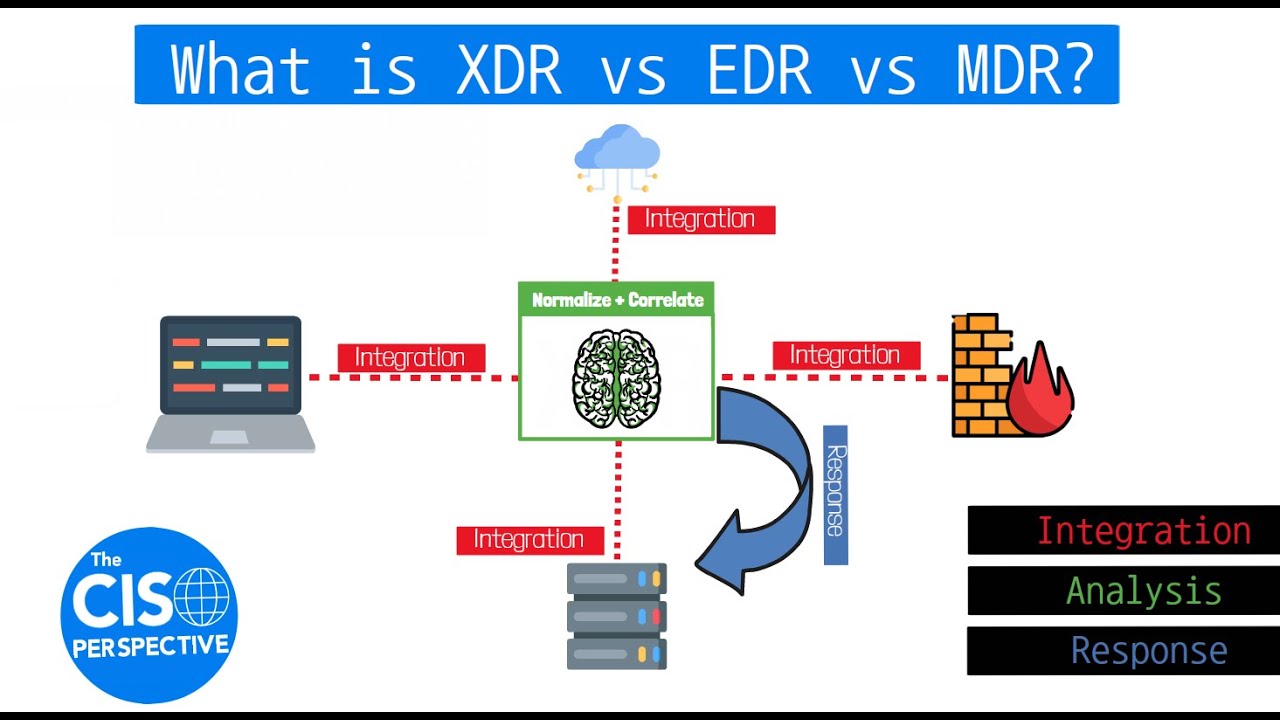
What is XDR vs EDR vs MDR? Breaking down Extended Detection and Response
FortiEDR - Advanced Endpoint Protection with Automated Detection and Response | Endpoint Security

Microsoft 365 Defender for Endpoint? Good Enough for your Business?

Microsoft Defender for Business EDR to XDR Security Upgrade Using Microsoft 365 Business Premium

MDE Tutorial -13 - Endpoint Detection and Response (EDR) in Microsoft Defender for Endpoints

Complete Guide to SentinelOne EDR (Endpoint Detection and Response): Exploring the Console in Part 1
5.0 / 5 (0 votes)
