Understanding the STUN Protocol
Summary
TLDRThe video from the Asian Tech Forum explains how smart IoT devices, like smart cameras and plugs, communicate instantly despite being behind NAT (Network Address Translation) firewalls. The solution lies in the STUN (Session Traversal Utilities for NAT) protocol, which helps devices discover their public IP addresses by interacting with STUN servers. The video covers the problem of device-to-device communication in home networks, how STUN works, its implementation in VoIP and peer-to-peer communication, and concludes with a Wireshark demo illustrating its functionality.
Takeaways
- 🔌 Smart IoT devices quickly connect to apps by solving NAT traversal challenges using specific protocols.
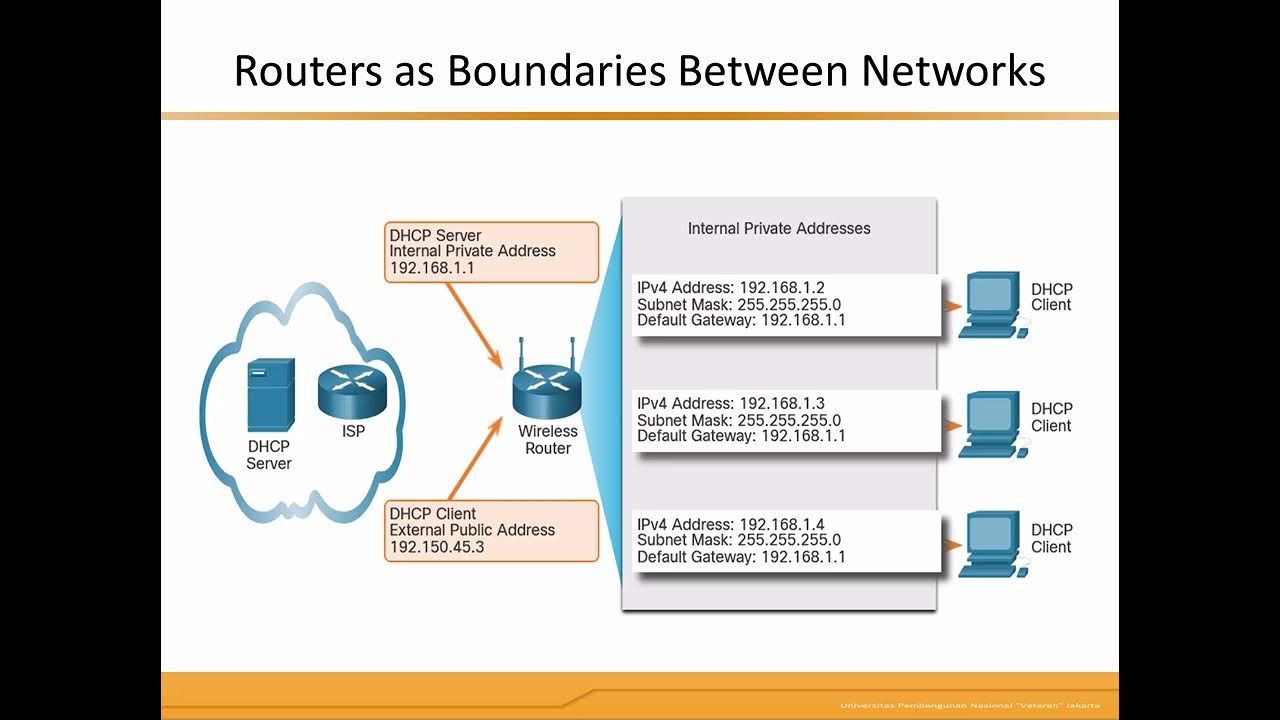
- 🌐 The NAT (Network Address Translation) complicates device-to-device communication, requiring specialized protocols for IoT home automation.
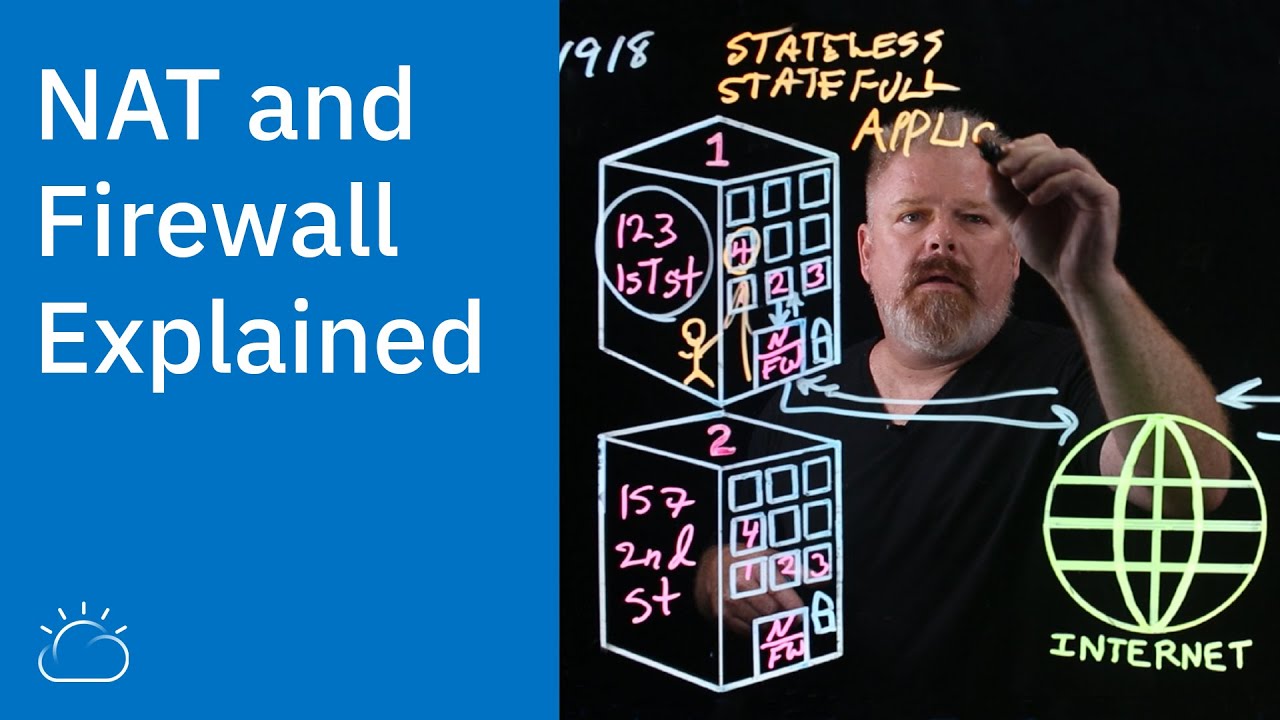
- 🔍 The STUN (Session Traversal Utilities for NAT) protocol is used to help devices behind NAT communicate by discovering their public IP address and port.
- 📜 STUN works by sending a request to a STUN server, which responds with the public IP address and port number of the requesting device.
- 📞 STUN plays a crucial role in enabling VoIP and peer-to-peer (P2P) communications, including applications like WebEx and Skype.
- 🖥️ STUN clients compare their private IP and port with the public IP and port in the STUN server response to detect if they are behind a NAT device.
- 🔐 One of STUN's disadvantages is that it isn't very secure, as data sent through it is unencrypted and primarily uses UDP, which is less reliable.
- 📝 The RFC 8489 defines the latest version of the STUN protocol, enhancing its use cases beyond just UDP.
- ⚙️ STUN operates using request-response transactions, where a binding request is sent, and the STUN server responds with the public-facing IP and port.
- 🧪 A Wireshark demo can be used to inspect STUN messages, showing how a device discovers its public IP address and communicates with others behind NAT.
Q & A
What problem does the STUN protocol aim to solve?
-The STUN protocol helps devices behind a NAT (Network Address Translation) firewall communicate with each other by discovering their public IP addresses and port numbers, thus enabling device-to-device communication even in home networks where NAT can disrupt such connections.
What does STUN stand for and what is its primary function?
-STUN stands for Session Traversal Utilities for NAT. Its primary function is to allow a computer behind a NAT firewall to discover its public IP address and port, enabling communication with another computer over the internet.
How does the STUN protocol work?
-The STUN protocol works by sending a binding request from a client to a STUN server. The STUN server responds with the public IP address and port of the client. The client can then compare the original private IP and port with the response to determine if it's behind a NAT and establish communication with other devices.
What is a binding request and how is it used in the STUN protocol?
-A binding request is sent from a STUN client to the STUN server to learn the client’s public IP address and port. This information is sent back in the binding response, allowing the client to establish a connection with other devices.
What is the significance of the 'mapped address' in the STUN protocol?
-The 'mapped address' is the public IP address and port received by the STUN server in the binding request. It is used by the client to understand its public network identity, enabling it to communicate across the NAT.
What role does the transaction ID play in the STUN protocol?
-The transaction ID in the STUN protocol is a randomly generated 96-bit number that helps correlate a request with its corresponding response, especially since STUN often uses UDP, which does not have built-in sequence numbers like TCP.
What are the main use cases of the STUN protocol?
-STUN is widely used in VoIP (Voice over IP), peer-to-peer communication, and real-time applications such as WebEx and Skype, where NAT traversal is essential for maintaining connections between devices.
What are the disadvantages of the STUN protocol?
-The main disadvantages of STUN are that the data sent through it is often unencrypted, making it less secure, and it relies on UDP, which doesn't guarantee reliability since UDP does not have built-in retransmission.
How is STUN different from TURN (Traversal Using Relays around NAT)?
-While STUN helps clients discover their public IP address and port, TURN goes a step further by relaying data through an external server, ensuring that communication can occur even when direct peer-to-peer connections are blocked by strict NAT or firewall settings.
How does the STUN protocol handle security vulnerabilities?
-STUN uses mechanisms such as HMAC (Hashed Message Authentication Code), transaction IDs, and optional username/password authentication to address certain security vulnerabilities, such as man-in-the-middle attacks and DNS spoofing.
Outlines

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraMindmap

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraKeywords

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraHighlights

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraTranscripts

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahora5.0 / 5 (0 votes)