How hackers are breaking into MFA enabled Microsoft 365 accounts
Summary
TLDRHackers are increasingly using a tool called 'Evil Jinx' to bypass Multi-Factor Authentication (MFA) by stealing authenticated session cookies from users through phishing emails. Despite MFA's effectiveness, this method has led to successful breaches of Microsoft 365 accounts. The script discusses the attacker's process and introduces 'Clarion,' an open-source tool designed to warn users of fake login pages. It also outlines additional security measures, including 24/7 monitoring, improved phishing protection, stricter authentication for VPNs, and security awareness training to combat these sophisticated attacks.
Takeaways
- 🔒 Multi-factor authentication (MFA) is being bypassed by hackers using sophisticated phishing techniques to breach accounts.
- 🎯 Microsoft 365 accounts, even with MFA enabled, are vulnerable to these attacks, which are becoming increasingly common.
- 🐟 Traditional phishing methods have evolved to include fake login screens that mimic legitimate services, tricking users into providing credentials.
- 🛠️ A tool called Evil Jinx is used by attackers to steal authenticated session cookies from users, bypassing MFA.
- 🔗 Attackers generate fake login URLs for services like Office 365 and use them in phishing emails to deceive users.
- 🕵️♂️ Users are often unaware that their credentials have been compromised, as the phishing screens closely resemble the real ones.
- 📢 Microsoft previously stated that 99.9% of identity-based attacks are thwarted by MFA, but new tactics have rendered this less effective.
- 🚫 The script introduces Clarion, an open-source tool designed to warn users when they are on an incorrect login page, potentially preventing credential theft.
- 🌐 Enhanced security measures are being implemented, including 24/7 security monitoring, improved phishing protection, and stricter authentication for VPN users.
- 📚 Security awareness training and phishing simulations are being conducted to educate users on identifying and avoiding malicious emails.
- 🔑 Additional security methods such as hardware keys and a zero-trust security model are being considered for even stricter security protocols.
Q & A
How are hackers bypassing multi-factor authentication (MFA) to breach Microsoft 365 accounts?
-Hackers use a tool called Evil Jinx to create fake login URLs that look identical to legitimate Microsoft 365 login pages. When users enter their credentials and complete MFA, the tool steals the authenticated session cookies, allowing hackers to log in as the user without needing the second form of authentication.
What was the traditional method of phishing attacks before the introduction of tools like Evil Jinx?
-Traditional phishing methods involved creating fake login screens to trick users into providing their username and password. If the account had MFA enabled, the attacker couldn't log in because they didn't have the second form of authentication.
How effective was MFA in preventing identity-based attacks according to Microsoft?
-Microsoft stated that 99.9% of identity-based attacks were thwarted by MFA, leading to a big push for its implementation with security defaults.
What role does the session cookie play in the attack described in the transcript?
-The session cookie, once stolen by the attacker, allows them to log in as the victim without needing to go through the MFA process again. This cookie essentially grants full access to the victim's account.
What does the fake login URL created by Evil Jinx look like?
-The fake login URL looks very similar to the legitimate one, with only minor differences such as 'login.microsoftonline.com' having an extra 'l' in 'online'.
How can users detect that they are on a phishing site using Evil Jinx?
-Users may not easily detect it because the phishing site looks identical to the legitimate login page, including company branding. However, small details like the URL might give it away.
What initial step does the tool 'Clarion' take to prevent users from falling for phishing attacks?
-Clarion recognizes when a user is on a fake login page and displays a big warning, advising them not to enter their password.
What additional measures are being taken to address the problem of phishing attacks bypassing MFA?
-Measures include 24x7 Security Operation Center monitoring, improved phishing protection using AI tooling, switching to an allow list model for country-based access, implementing stricter authentication for VPN logins, and monthly security awareness training and phishing simulations for staff.
Why is there a switch from a block list to an allow list model for country-based access?
-The switch is because MFA can no longer be trusted as it once was. By default, only certain countries will be allowed, and all others will be blocked, making it harder for attackers to log in from high-risk countries.
How is the authenticity of users using a VPN ensured?
-Stricter authentication methods are implemented for VPN logins, requiring stronger authentication to ensure the user logging in is who they claim to be.
What are some additional security measures mentioned in the transcript?
-Additional measures include the use of hardware keys and a zero-trust security model for enhanced security.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video
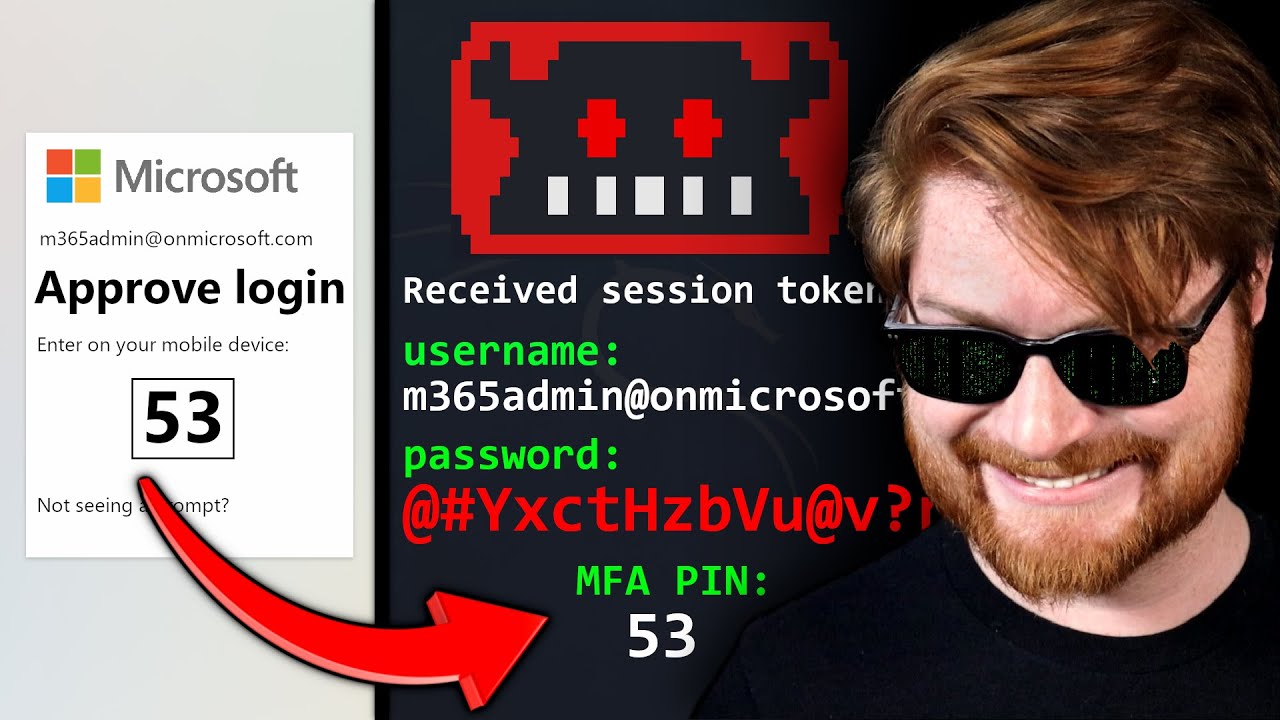
I Stole a Microsoft 365 Account. Here's How.
[TERBARU] Cara Aktivasi dan Login MFA ASN Digital & Solusi Invalid Authentication Code Hingga SUKSES

Crypto Security 🚨How to Avoid Hacks and Scams | Blum Academy
What is Social Engineering in Cyber Security? Explained

How to configure and enforce multi-factor authentication in your tenant

Your webcam could be recording you right now! (This malware is creepy)
5.0 / 5 (0 votes)