I Stole a Microsoft 365 Account. Here's How.
Summary
TLDRThe video demonstrates how a hacker uses Evil Jinx, a reverse proxy phishing tool, to steal credentials from Microsoft 365 users. It explains how the attacker sets up a fishing domain, crafts a phishing email, and uses Evil Jinx to intercept user credentials and session tokens. By using social engineering tactics and a carefully crafted fishing setup, the hacker bypasses multi-factor authentication, ultimately gaining full access to the victim's account. The video also highlights the tools and strategies behind reverse proxy phishing, and encourages viewers to learn more about Evil Jinx's capabilities for penetration testing and red team engagements.
Takeaways
- 😀 Evil Jinx is a reverse proxy phishing framework used to bypass multi-factor authentication and steal credentials.
- 😀 The tool acts as a man-in-the-middle, capturing login information from real websites like Microsoft 365, Google, and others.
- 😀 Evil Jinx enables attackers to intercept authentication tokens, cookies, and session data from users during the login process.
- 😀 A fishing domain is required for an attack, and attackers typically use subdomains for legitimacy (e.g., Microsoft OneDrive update link).
- 😀 To set up Evil Jinx, attackers deploy it on cloud instances (like DigitalOcean), configure subdomains, and use them for social engineering.
- 😀 Crafting a phishing email involves convincing users to click on malicious links, such as a fake software update request.
- 😀 Evil Jinx allows the attacker to capture login credentials, including usernames, passwords, and session tokens, after the victim logs in.
- 😀 Attackers can use session cookies to impersonate the victim and access their accounts, such as Microsoft 365, without needing to re-enter credentials.
- 😀 Fishing lures are created with Evil Jinx to trick victims into entering their credentials, and these lures are shared in phishing emails.
- 😀 Attackers can easily configure Evil Jinx for any website, making it a versatile tool for phishing and credential theft across the internet.
- 😀 The video demonstrates how social engineering and fishing, combined with Evil Jinx, can lead to compromised accounts, even bypassing strong security measures like two-factor authentication.
Q & A
What is Evil Jinx and how does it work?
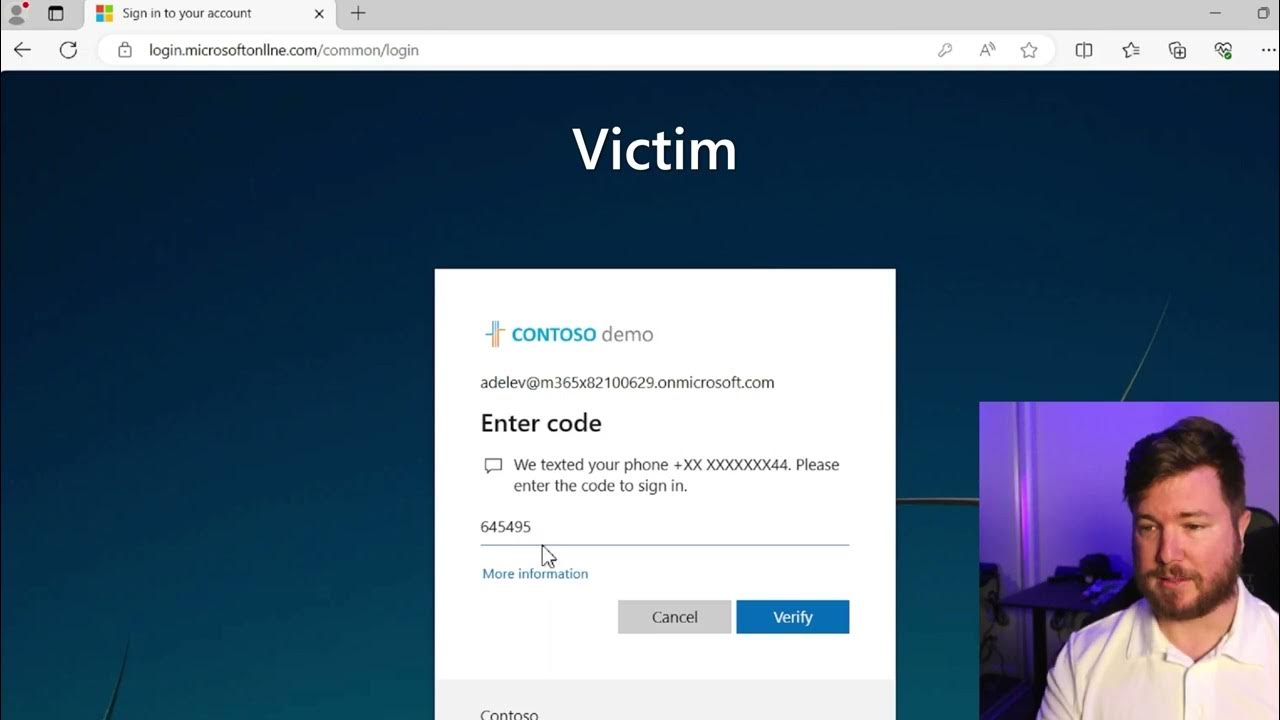
-Evil Jinx is a reverse proxy phishing framework that acts as a man-in-the-middle to capture user credentials and session tokens by intercepting communication between the victim and a legitimate website, such as Microsoft 365.
What makes Evil Jinx particularly effective in phishing attacks?
-Evil Jinx is effective because it can bypass multi-factor authentication (MFA) and proxy traffic from the victim's browser to the actual website, making it appear that the victim is directly interacting with the legitimate service while their credentials and session information are stolen.
How do you set up Evil Jinx for phishing?
-To set up Evil Jinx, you need a cloud instance, such as from Digital Ocean, where you can host your phishing domains. You must clone the Evil Jinx repository, install necessary dependencies like Go and Git, configure the phishing domain, and create a fishing script (fishlit) for the target website.
What are fish lits and why are they important in Evil Jinx?
-Fish lits are configuration files used by Evil Jinx to specify the target website and how to capture credentials. These files define parameters such as proxy hosts, authentication tokens, and session cookies, making them essential for targeting specific websites.
Can Evil Jinx be used for phishing any website, not just Microsoft 365?
-Yes, Evil Jinx can be configured to fish credentials from any website, not just Microsoft 365. You can create fish lits for various websites and services, making Evil Jinx versatile in phishing attacks.
What is the role of social engineering in this phishing attack?
-Social engineering in this context involves tricking the victim into believing they are interacting with a legitimate website, like Microsoft 365, by sending them convincing phishing emails or messages with fake updates or alerts.
How does Evil Jinx handle the victim's multi-factor authentication (MFA)?
-Evil Jinx can intercept the MFA process by capturing the tokens sent during authentication. Once the victim approves the MFA request, Evil Jinx captures the session cookies and tokens, allowing the attacker to bypass MFA and access the victim's account.
What is the 'lure' in a phishing attack with Evil Jinx?
-The 'lure' is a phishing link that the attacker sends to the victim. When the victim clicks on this link, they are redirected to a fake login page created by Evil Jinx, where they unknowingly provide their credentials.
How does the attacker gain access to the victim's account after the phishing attack?
-After the victim enters their credentials and successfully completes MFA, Evil Jinx captures the session cookies and tokens. The attacker can then use these to log into the victim's account directly, bypassing the need for further authentication.
What are some possible defenses against Evil Jinx phishing attacks?
-Defenses include implementing stronger MFA methods (such as hardware tokens or biometrics), using web security protocols like HTTP Strict Transport Security (HSTS), and educating users about phishing risks and how to spot fake login pages.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video
How hackers are breaking into MFA enabled Microsoft 365 accounts

Phishing, Vishing, and SMiShing |Phishing attacks |Cyber security awareness video |Security Quotient

How to Automate Regular Emails in Microsoft Outlook

Cyberto's Social Media Sabotage! - Social Media Security Awareness Training Video

How To Install And Run ZPhisher on Kali Linux Phishing Tool - Video 2023 with InfoSec Pat

Configure NGINX as a Reverse Proxy
5.0 / 5 (0 votes)