GDPR and Data Mapping
Summary
TLDRGrant Fritchie from Reggae Software discusses the challenges of GDPR compliance, emphasizing the importance of data mapping and understanding the types of data an organization holds. He highlights the risks of data breaches caused by employee error and negligence, and stresses the necessity of classifying data, reducing the attack surface area, and managing data in compliance with GDPR. Fritchie advocates for automating data management processes to maintain control and ensure GDPR compliance.
Takeaways
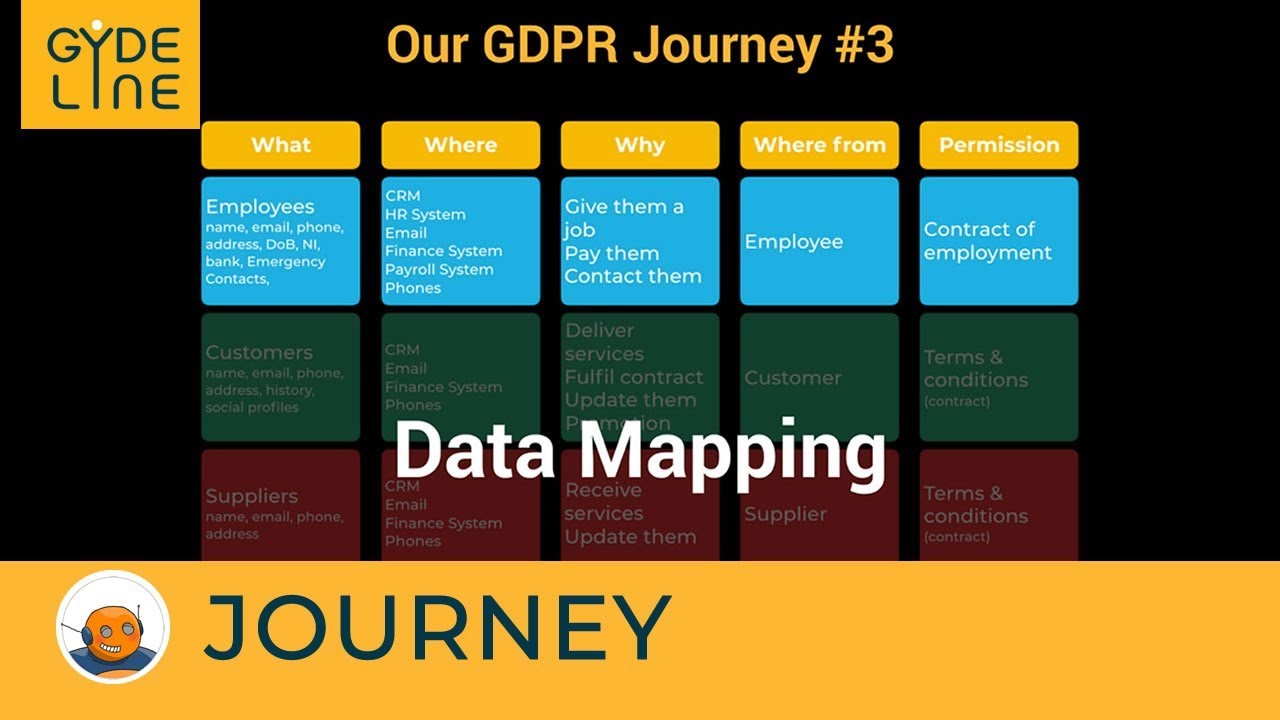
- 📚 The primary challenge in GDPR compliance is understanding and mapping all the data an organization holds, and knowing where it resides.
- 🔍 It's crucial to classify data under GDPR to determine the level of protection required for different types of data.
- 🚨 A significant portion of data breaches are due to employee error and negligence, highlighting the importance of proper data handling.
- 🔑 The 'right to be forgotten' under GDPR necessitates knowing where all data is stored to ensure it can be deleted upon request.
- 🔍 Step 1 involves finding all data storage locations, including databases, servers, and cloud services like AWS.
- 📋 Step 2 is about classifying the data to understand which data is private and should not be shared, and implementing controls accordingly.
- 🛡️ Step 3 focuses on reducing the attack surface area by removing unnecessary mechanisms that could lead to accidental data leaks.
- 💾 Step 4 is about managing the data in compliance with GDPR, which includes documenting and adhering to the regulations.
- 🤖 Automation is key to managing data effectively, ensuring that data movement between environments is controlled and traceable.
- 🚫 Manual processes can lead to data being moved without proper oversight, which is a risk for GDPR compliance.
- 📈 Knowledge of the data and its location is fundamental to meeting all GDPR requirements, including the ability to remove data as needed.
Q & A
What is the primary challenge mentioned in the script regarding GDPR compliance?
-The primary challenge is mapping and understanding the data an organization has, knowing where it resides, and classifying it according to GDPR requirements for appropriate protection levels.
What percentage of data breaches were caused by employee error according to the script?
-10% of data breaches were caused by employee error.
What percentage of data breaches were due to employee negligence as mentioned in the script?
-7% of data breaches were due to employee negligence.
What does the 'right to be forgotten' under GDPR entail?
-The 'right to be forgotten' requires organizations to know where all personal data is stored so that it can be removed upon request, demonstrating compliance with GDPR.
Why is it crucial to know where data is stored in the context of GDPR compliance?
-Knowing where data is stored is crucial for GDPR compliance because it enables organizations to protect data appropriately, manage it effectively, and fulfill requests like the 'right to be forgotten'.
What is the importance of classifying data under GDPR?
-Classifying data is important to determine which data is private and should not be shared, and to implement the necessary controls to protect it as required by GDPR.
What is the suggested approach for managing data to ensure GDPR compliance?
-The suggested approach includes finding all data, classifying it, reducing the attack surface area, and managing the data in compliance with GDPR, including automating data management processes.
What is the role of automation in achieving GDPR compliance according to the script?
-Automation is critical for getting data management under control, ensuring that data does not get moved or processed inappropriately, and maintaining compliance with GDPR requirements.
What are some of the consequences of not managing data properly as per GDPR?
-Consequences include potential data breaches, non-compliance with GDPR regulations, and the inability to fulfill requests like the 'right to be forgotten'.
What does reducing the attack surface area mean in the context of data protection?
-Reducing the attack surface area means minimizing the opportunities for data leaks by removing unnecessary mechanisms and ensuring that only authorized processes and accesses are in place.
Why is it important to document compliance with GDPR?
-Documenting compliance with GDPR is important for demonstrating to regulators and affected individuals that an organization is adhering to the regulation's requirements and protecting personal data as mandated.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Using Open Source Tools to Build Privacy-Conscious Data Systems

Data Inventories and Data Maps: The Cornerstone to GDPR Compliance
GDPR Compliance Journey - 03 Data Mapping

GDPR Compliance Journey - 09 Retention

Your Personal Data Inventory Top Tips & Brexit Impact 161220

The Data Flow Mapping Tool – the quick and easy way to document personal data processing
5.0 / 5 (0 votes)