How to use AWS WAF (Web application firewall)/Web ACL? - Step By Step Tutorial (Part-11)#aws #devops
Summary
TLDRThis video provides a comprehensive tutorial on setting up AWS Web Application Firewall (WAF) with an application load balancer. It walks through the process of blocking requests from a specific IP (e.g., the user’s laptop), configuring IP sets, and applying rules to control access. The tutorial also demonstrates testing the firewall by blocking and allowing requests, as well as enabling CAPTCHA for additional security. By the end, viewers will understand how to configure and manage WAF rules in AWS to protect applications behind a load balancer.
Takeaways
- 😀 Set up an AWS Web Application Firewall (WAF) by associating it with an Application Load Balancer (ALB) to protect your web applications.
- 😀 The WAF enables you to create custom rules to block or allow traffic based on IP addresses, user agents, or other parameters.
- 😀 In this demo, the primary goal is to block requests originating from a specific laptop's IP address using an IP set in WAF.
- 😀 To block specific IPs, create an IP set in the WAF configuration and use the CIDR notation to specify ranges or individual IPs.
- 😀 After creating the IP set, create a custom rule that links the IP set to a blocking action for the specific IP addresses.
- 😀 Test the blocking rule by accessing the application through the Load Balancer's DNS URL to see the 403 Forbidden response when blocked.
- 😀 The WAF allows you to further refine security by using more granular validation options, such as inspecting request headers or using Rule Builders.
- 😀 After implementing the rule, you can also modify the action to 'allow' to permit previously blocked traffic, testing changes in real-time.
- 😀 The Web Application Firewall integrates with AWS CloudWatch to monitor blocked requests and logs for visibility into security actions.
- 😀 Additional security features in WAF include enabling CAPTCHA, which requires users to verify they are human before accessing the application.
Q & A
What is the purpose of setting up an AWS Web Application Firewall (WAF) in this tutorial?
-The purpose of setting up an AWS Web Application Firewall (WAF) in this tutorial is to demonstrate how to block access from specific IP addresses, in this case, blocking the user's laptop IP to prevent unauthorized access to the application running behind the load balancer.
What is an IP set in the context of AWS WAF, and how is it used in this tutorial?
-An IP set in AWS WAF is a logical grouping of IP addresses that you can use to block or allow traffic based on the source IP. In this tutorial, an IP set is created to store the user's laptop IP address, which is then used in a rule to block access from that IP.
How did the user find their laptop's IP address for use in the AWS WAF setup?
-The user found their laptop's IP address by Googling 'What is my IP?' and copying the address that was displayed.
Why is it important to set the IP range correctly when creating an IP set in AWS WAF?
-It is important to set the IP range correctly to ensure that the correct network addresses are blocked. In the tutorial, the user added a '/32' suffix to the IP address, which denotes a single IP address in the block, ensuring that only requests from that specific IP are affected.
What are the steps to associate a Web Application Firewall with an AWS resource like a load balancer?
-To associate the AWS Web Application Firewall with a resource like a load balancer, the user must navigate to the WAF console, select the load balancer, and attach the WAF by choosing the correct rule set. This ensures that the WAF rules are enforced for the traffic passing through the load balancer.
How can a user test if the Web Application Firewall rules are working as expected?
-To test the WAF rules, the user can attempt to access the application behind the load balancer from a blocked IP address. In the tutorial, the user receives a '403 Forbidden' error when trying to access the site with the laptop's blocked IP, confirming that the rule is working.
What happens when the user changes the rule action from 'Block' to 'Allow' in AWS WAF?
-When the user changes the rule action from 'Block' to 'Allow', the WAF will allow requests from the previously blocked IP address to access the application. This was demonstrated by the user being able to access the application again after modifying the rule.
What is the significance of CloudWatch in the context of AWS WAF?
-CloudWatch is used for monitoring and logging the requests handled by the AWS WAF. In this tutorial, the user chose to enable CloudWatch metrics for their WAF setup, allowing them to track and review logs of blocked or allowed requests.
What additional security feature does the user enable in the WAF to further verify users?
-The user enables CAPTCHA as an additional security feature in the AWS WAF. This ensures that only human users can pass through the firewall, adding an extra layer of protection by presenting a challenge (like solving a puzzle) for visitors.
What is the next topic the user plans to cover in the following session?
-In the next session, the user plans to cover VPC peering. They will demonstrate how to create two VPCs and establish a connection between them, allowing the VPCs to communicate with each other.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

AWS ALB (Application Load Balancer) - Step By Step Tutorial (Part -9)
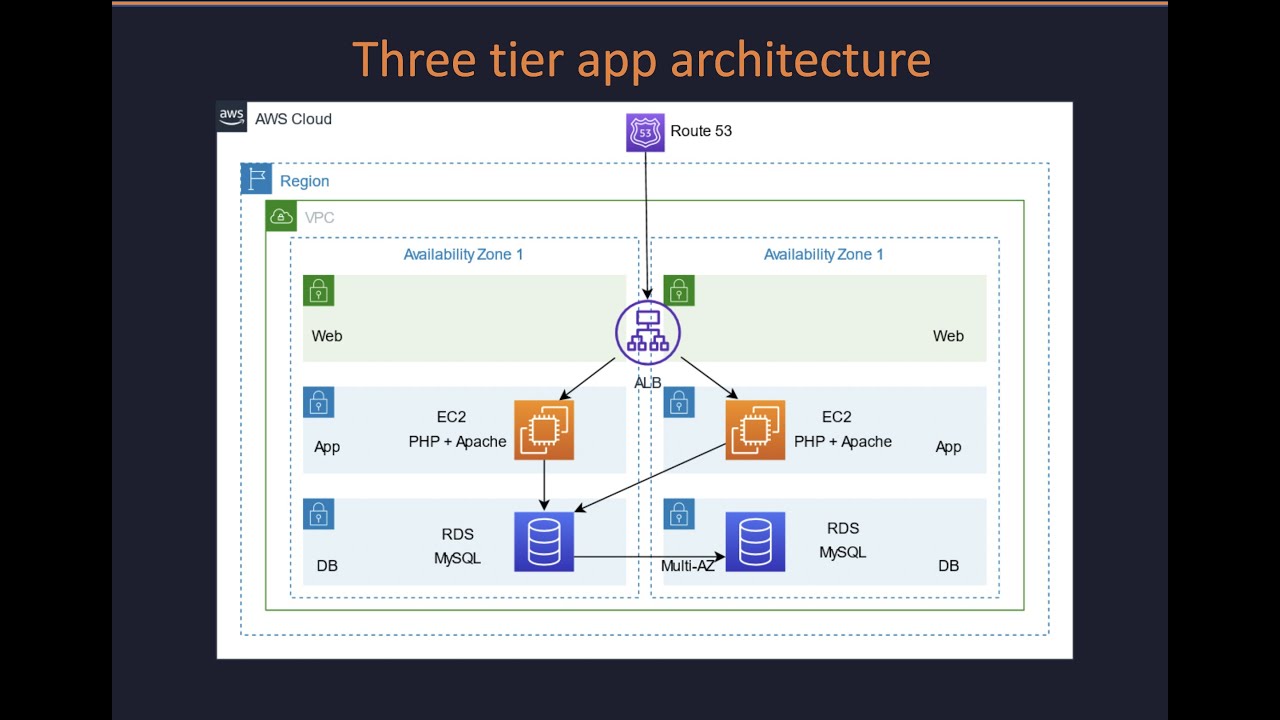
Demo | Three-tier web app in AWS with VPC, ALB, EC2 & RDS
How to create an Application Load Balancer on AWS

How to use AWS Application Load Balancer (ALB) for Jenkins Server | By M. Sharma

2.Netscaler Features

AWS Tutorials - 48 - Auto Scaling With Load Balancer - Load Balancer with Auto Scaling - AWS (Hindi)
5.0 / 5 (0 votes)