Ethernet Transmitter Algorithm
Summary
TLDRThis tutorial covers the Ethernet transmitter algorithm, explaining how it functions with CSMA/CD to manage data transmission on Ethernet networks. It introduces the concept of Manchester encoding for signal conversion and addresses runt frames, which occur due to collisions or network issues. The video also highlights the importance of collision detection and the use of exponential back-off to minimize collision probability, providing a comprehensive understanding of Ethernet communication protocols.
Takeaways
- 😀 The Ethernet transmitter algorithm is a method used by network adapters to manage data transmission over Ethernet cables.
- 🔍 Outcomes of the session include understanding the Ethernet transmitter algorithm, recognizing runt frames, and knowing about exponential back-off.
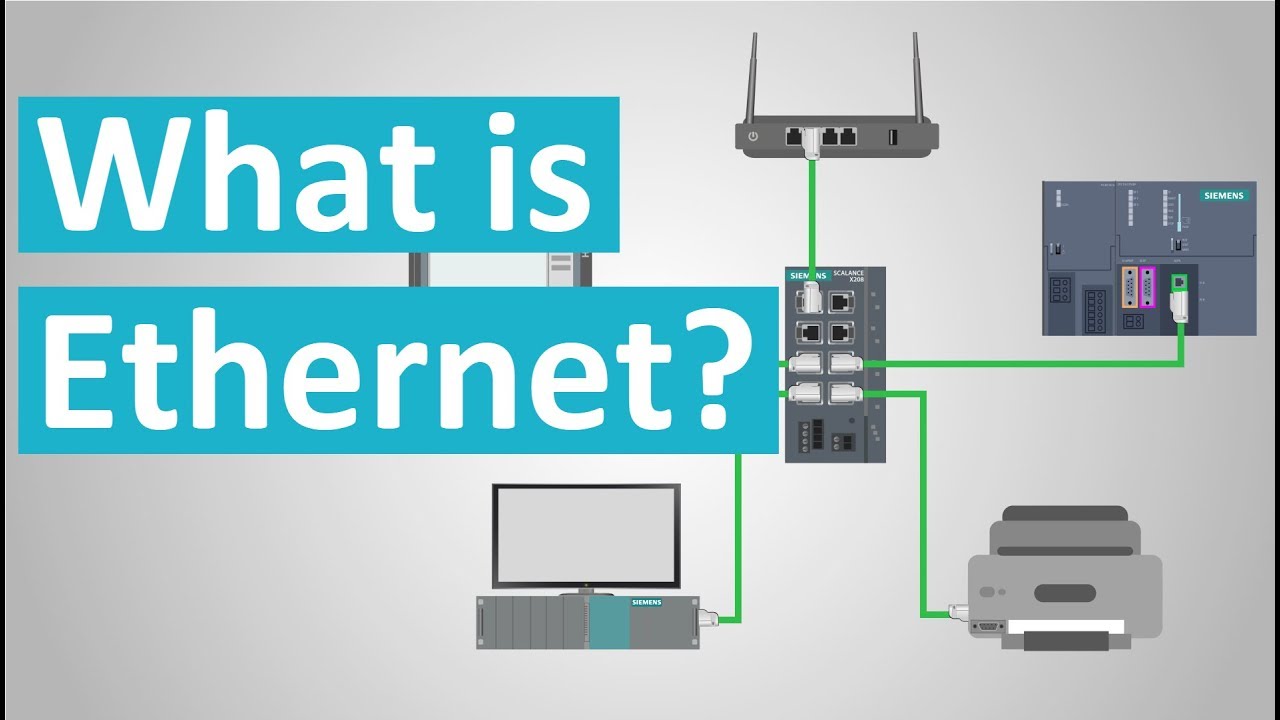
- 💡 The Ethernet adapter, also known as the Network Interface Card (NIC), is a crucial component that connects a host computer to an Ethernet cable via an RJ45 socket.
- 🌐 The Ethernet Media Access Control (MAC) algorithm is implemented in the hardware of the network adapter and uses CSMA/CD (Carrier Sense Multiple Access with Collision Detection) as its access method.
- 📶 Manchester encoding is the technique used by Ethernet to convert data bits into electrical signals for transmission over copper cables.
- 🚀 The Ethernet transmitter algorithm transmits a frame immediately if the adapter has a frame to send and the channel is idle.
- 🚫 If the line is busy, the algorithm waits until it becomes idle before transmitting, reflecting the CSMA/CD protocol's behavior.
- 💥 Collisions occur when two or more hosts transmit at the same time, leading to a runt frame, which is an Ethernet frame less than 64 bytes.
- 🔁 Exponential back-off is a technique used to reduce collision probability by doubling the waiting time after each failed transmission attempt.
- ⏱️ A runt frame is created when a collision occurs, or due to issues like malfunctioning network cards, buffer under-runs, or duplex mismatches.
Q & A
What are the three outcomes of the session on the Ethernet transmitter algorithm?
-The three outcomes of the session are: 1) Understanding the Ethernet transmitter algorithm, 2) Understanding runt frames, and 3) Knowing about exponential back-off.
What is the function of an Ethernet adapter in a host computer?
-An Ethernet adapter in a host computer is used to connect an Ethernet cable, allowing the computer to communicate over a network.
What is the access protocol for Ethernet?
-The access protocol for Ethernet is Ethernet Media Access Control (MAC) algorithm, which is implemented in the hardware of the network adapter.
What access method does Ethernet use?
-Ethernet uses the CSMA/CD (Carrier Sense Multiple Access with Collision Detection) access method.
Why is Manchester encoding technique used by Ethernet?
-Ethernet uses the Manchester encoding technique to convert data bits into electrical signals that can be transmitted over copper cables, such as Ethernet cables.
How does the Ethernet transmitter algorithm handle a frame transmission when the channel is idle?
-When the adapter has a frame to send and the channel is idle, it transmits the frame immediately.
What is the maximum payload size of an Ethernet frame?
-The maximum payload size of an Ethernet frame is 1500 bytes.
Why is Ethernet referred to as a CSMA/CD protocol?
-Ethernet is referred to as a CSMA/CD protocol because it uses Carrier Sense Multiple Access with Collision Detection, allowing hosts to detect collisions when they occur during transmission.
What is a runt frame in Ethernet?
-A runt frame is an Ethernet frame that is less than 64 bytes in length, typically caused by collisions, malfunctioning network cards, buffer under-runs, or duplex mismatches.
What is the purpose of transmitting a 32-bit jamming sequence in case of a collision?
-A 32-bit jamming sequence is transmitted to indicate a collision has occurred, allowing all involved host computers to recognize the collision and stop their transmission.
What is the role of exponential back-off in the Ethernet transmitter algorithm?
-Exponential back-off is a technique used by the Ethernet algorithm to reduce the probability of collisions by doubling the waiting time between retransmission attempts after a collision is detected.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)