Computer Networks: Crash Course Computer Science #28
Summary
TLDRThis CrashCourse Computer Science episode explores the evolution and principles of computer networks, from the early days of Local Area Networks (LANs) and Ethernet to the development of the Internet. It delves into concepts like Carrier Sense Multiple Access (CSMA), Exponential Backoff, and the distinction between Circuit Switching and Packet Switching. The episode explains how these technologies enable efficient data transmission, reduce collisions, and contribute to the Internet's robustness and scalability.
Takeaways
- 🌐 The Internet has revolutionized global communication, reducing the time to send information from weeks to fractions of a second.
- 📧 Before computer networks, sharing data involved physical media like punch cards or magnetic tapes, which was inefficient compared to today's instant digital sharing.
- 💡 The first computer networks emerged in the 1950s and 60s, primarily within organizations to facilitate information exchange and resource sharing.
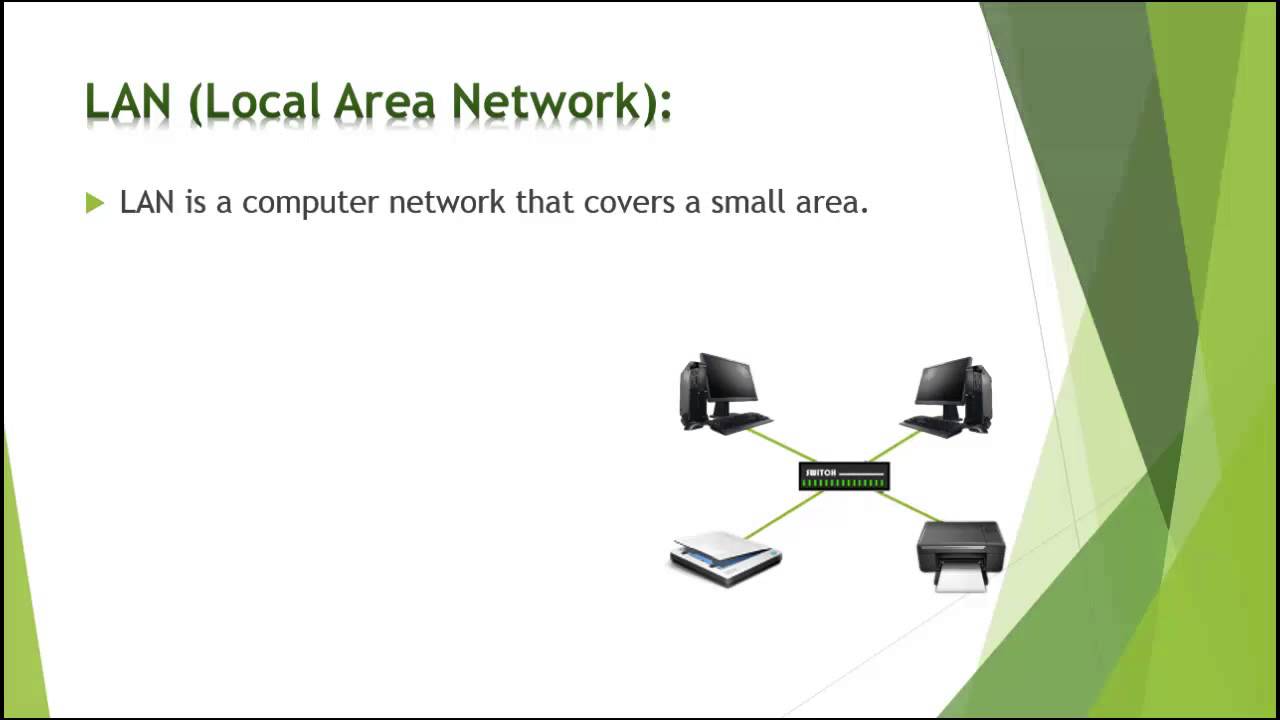
- 🔌 Local Area Networks (LANs) are networks of computers in close proximity, ranging from two machines to thousands across a university campus.
- 🔄 Ethernet, developed in the 1970s, is the most successful LAN technology, allowing multiple computers to share a single cable with unique MAC addresses to avoid confusion.
- 🚫 A drawback of shared transmission mediums is the potential for collisions when multiple devices transmit simultaneously, garbling the data.
- 🤖 Computers can detect collisions and employ strategies like Exponential Backoff to reduce the likelihood of re-collision by waiting random periods before retransmitting.
- 🌉 Network Switches help reduce collisions by creating separate collision domains and only forwarding data necessary between networks, improving efficiency.
- 🔄 Routing is a fundamental networking concept, with multiple paths available for data to travel from one point to another in large networks like the Internet.
- 📦 Packet Switching is a method of dividing data into small packets, each with a destination address, allowing for flexible and efficient routing through the network.
- 🛡️ Packet Switching was developed with fault tolerance in mind, especially during the Cold War, to ensure communication could continue despite potential disruptions.
- 🚀 The ARPANET, funded by the US Advanced Research Projects Agency, was the world's first packet-switched network and a precursor to the modern Internet.
Q & A
What is the main topic discussed in the CrashCourse Computer Science video script?
-The main topic discussed is the history and fundamental principles of computer networks, including their development, the concept of Local Area Networks (LANs), Ethernet, and various networking techniques such as Exponential Backoff and Packet Switching.
How has the internet impacted the speed of global communication compared to 150 years ago?
-The internet has drastically reduced the time it takes to send information globally. While sending a letter from London to California took two to three weeks 150 years ago, today an email takes a fraction of a second.
What were the two main benefits of early computer networks?
-The two main benefits were the facilitation of faster and more reliable exchange of information between different people and computers within an organization, and the ability to share physical resources like printers and storage drives.
What is a Local Area Network (LAN) and what is its size range?
-A Local Area Network (LAN) is a computer network that spans a small geographical area such as a room, a building, or a campus. It allows computers to communicate with each other and share resources.
What is Ethernet and why is it significant?
-Ethernet is a family of computer networking technologies commonly used in LANs, developed in the early 1970s at Xerox PARC. It is significant because it is the most famous and successful LAN technology and is still widely used today.
What is the purpose of a Media Access Control (MAC) address in Ethernet?
-The MAC address is a unique identifier assigned to each network interface controller for use as a network address in communications within a network segment. It ensures that data is sent to the correct device on a shared network cable.
What is Carrier Sense Multiple Access (CSMA) and how does it work?
-Carrier Sense Multiple Access (CSMA) is a protocol used in local area network (LAN) technologies where multiple devices share the same transmission medium. It allows devices to sense when the channel is in use and wait before transmitting their data to avoid collisions.
What is a collision in the context of Ethernet networks?
-A collision occurs when two or more devices attempt to transmit data on the same network segment simultaneously, causing the data to be garbled and requiring retransmission.
What is Exponential Backoff and how does it help in reducing network collisions?
-Exponential Backoff is a technique used to avoid collisions on a network by having devices that detect a collision wait for an exponentially increasing amount of time before attempting to retransmit. This reduces the likelihood of repeated collisions.
What is the difference between Circuit Switching and Packet Switching?
-Circuit Switching is a method of dedicating a communication line for exclusive use between two devices for the duration of a transmission, similar to a telephone call. Packet Switching, on the other hand, involves breaking down data into small packets that are sent individually over the network and can take different routes to the destination, making it more efficient and fault-tolerant.
What is the role of a Network Switch in reducing collisions?
-A Network Switch helps reduce collisions by creating separate collision domains. It only forwards data between networks when necessary and keeps a list of MAC addresses to determine where data should be sent, thus allowing multiple transmissions to occur simultaneously without colliding.
What is the significance of the ARPANET in the history of the internet?
-The ARPANET was the first packet-switched network and is considered the ancestor of the modern internet. It was funded by the US Advanced Research Projects Agency and laid the groundwork for the development of internet technologies.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Computer Networking Explained | Cisco CCNA 200-301
What is Ethernet?

BAB 5 JARINGAN KOMPUTER DAN INTERNET | JARINGAN LOKAL, INTERNET, KONEKTIVITAS INTERNET | INFORMATIKA

23. OCR GCSE (J277) 1.3 Types of networks
Types of computer network | Difference between LAN CAN MAN and WAN | Basics of computer Network 2024

Histórico e cenário atual das redes de computadores
5.0 / 5 (0 votes)