VLANs and VPNs - CompTIA A+ 220-1101 - 2.6
Summary
TLDRThe video script explores the concept of Local Area Networks (LANs) and introduces VLANs as a method to segregate networks for security and efficiency without the need for multiple physical switches. It also delves into Virtual Private Networks (VPNs), explaining how they provide a secure and encrypted means of communication over public networks, with a focus on the role of VPN concentrators in facilitating this secure data transfer.
Takeaways
- 🌐 A LAN is a Local Area Network that connects devices within the same broadcast domain.
- 🔒 Separation of networks like red and blue switches can be for security or to limit broadcast traffic.
- 🛠️ Network segmentation helps manage the network by assigning devices to specific switches based on their needs.
- 🚫 Inefficiencies arise from using separate switches, which increases costs and management efforts.
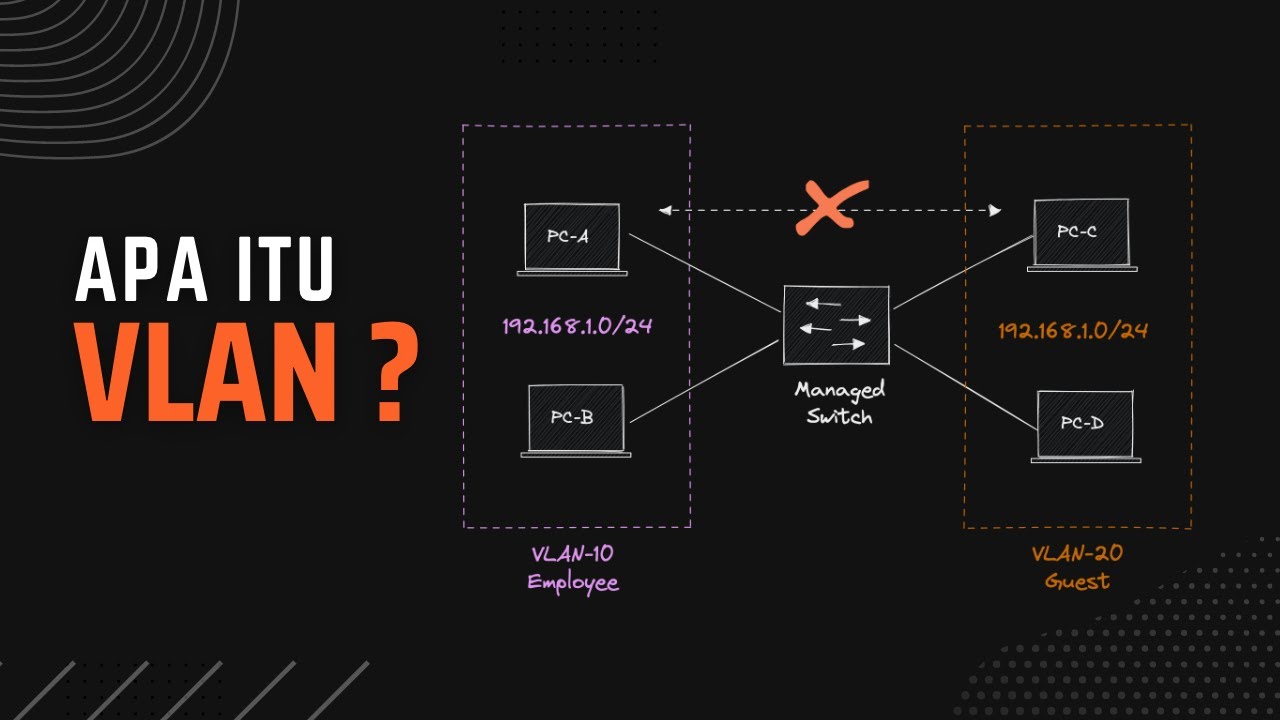
- 💡 VLANs (Virtual Local Area Networks) allow for logical separation of networks on a single physical switch.
- 🔄 VLANs improve efficiency and cost-effectiveness by reducing the need for multiple switches and simplifying management.
- 📈 The script introduces the concept of adding a third network (green) to demonstrate VLAN configuration.
- 🔢 VLANs are identified by numbers, such as VLAN 1 for red, VLAN 2 for blue, and VLAN 3 for green.
- 🔒 VPNs (Virtual Private Networks) provide secure communication over public networks like the internet by encrypting data.
- 🌐 VPNs typically involve a combination of software and hardware, including a concentrator that handles encryption and decryption.
- 💻 Modern operating systems often include VPN clients, allowing secure connectivity even on public Wi-Fi networks.
Q & A
What is a Local Area Network (LAN)?
-A Local Area Network (LAN) is a group of devices that are connected within the same broadcast domain, typically within a small geographic area such as a home, school, or office building.
Why might we want to separate devices into different broadcast domains?
-Separating devices into different broadcast domains can be done for security reasons, to limit the number of broadcasts on a network, or to manage the network more effectively by segmenting it into smaller pieces.
What inefficiencies can be observed in the scenario with two separate switches?
-Inefficiencies include the need to purchase and power two separate switches, manage configurations on both, and the underutilization of switch interfaces, leading to unnecessary costs and effort.
What is the solution to the inefficiencies mentioned in the script?
-The solution is to use a single switch and logically associate certain interfaces to different networks, which is more efficient and cost-effective.
What is the term for the virtualization of a local area network?
-The virtualization of a local area network is referred to as a VLAN (Virtual Local Area Network).
How does a VLAN provide separation between different networks on the same physical device?
-A VLAN groups devices in the same broadcast domain across the same physical device, providing network separation without the need for separate physical switches.
What is the purpose of assigning numbers to VLANs?
-Assigning numbers to VLANs helps in identifying and managing different networks more easily, instead of using colors or other non-numeric identifiers.
How does a VPN (Virtual Private Network) secure information sent over a public network?
-A VPN secures information by encrypting all data sent over the connection, ensuring that even if the data is intercepted, it cannot be understood by unauthorized parties.
What is a VPN concentrator, and what is its role in a VPN setup?
-A VPN concentrator is a device that may be standalone or integrated into a firewall, which receives encrypted data from a VPN client, decrypts it, and forwards it into the corporate network, and vice versa.
How does a VPN client on a laptop work when connected to an open wireless network?
-When enabled, a VPN client on a laptop creates an encrypted tunnel back to the VPN concentrator, ensuring that all data sent and received is encrypted, even when using an open and unencrypted wireless network.
What are some common deployment methods for VPNs?
-VPNs can be deployed using a combination of hardware and software, with specialized encryption hardware in a standalone device or integrated into a multi-use device like a firewall, and software configurations running on servers or installed as applications in operating systems.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тариф5.0 / 5 (0 votes)