SCAPHY: Detecting Modern ICS Attacks by Correlating Behaviors in SCADA and PHYsical
Summary
TLDRMoses presents SCaFFY, a method for detecting modern Industrial Control Systems (ICS) attacks by correlating SCADA system behaviors with physical process behaviors. This approach addresses challenges faced by traditional detection techniques, which are often isolated and evaded by advanced attacks using legitimate SCADA tools. SCaFFY monitors SCADA’s distinct operational phases to identify violations, such as system injection or bypassing, which may indicate an attack. The system tracks physical impacts from these violations, providing a robust solution with impressive results from real-world testing, including a 95% accuracy rate in attack detection and minimal response time.
Takeaways
- 😀 Scaffy is an approach for detecting ICS (Industrial Control Systems) attacks by correlating behaviors in SCADA systems and physical systems.
- 😀 The research is a collaboration between Georgia Tech and Sandia National Labs, focusing on improving ICS security.
- 😀 ICS manage critical processes like energy grids and water treatment, making them prime targets for attacks like Stuxnet and industrial malware.
- 😀 Existing ICS attack detection methods include physical anomaly models and host/network anomaly detection, but these techniques have limitations in detecting modern attacks.
- 😀 Modern ICS attacks often use legitimate SCADA tools, making it difficult for existing detection methods to recognize malicious behavior.
- 😀 Scaffy improves detection by analyzing SCADA’s execution phases (initialization, process control, etc.) and identifying anomalies caused by attackers.
- 😀 There are two primary types of attack violations in Scaffy: injection violations (attacker executes operations in incorrect phases) and bypass violations (attacker skips phases altogether).
- 😀 The physical impact of SCADA violations is modeled by analyzing actuator states and comparing them to the expected process trajectory or calibration setpoints.
- 😀 Scaffy uses dynamic analysis of OPC events (SCADA responses) to trigger and monitor process control execution phases for potential anomalies.
- 😀 In real-world testing, Scaffy achieved 95% accuracy with an average detection time of 9-10 seconds, successfully detecting industrial malware behaviors.
- 😀 One key challenge in ICS attack detection is the delay between the physical attack and observable changes in SCADA, requiring precise timing in the detection process.
Q & A
What is the main focus of the talk?
-The talk focuses on a method called Scaffy, which detects modern attacks on Industrial Control Systems (ICS) by correlating behaviors in SCADA systems with physical systems. It addresses the challenges of detecting ICS attacks and presents a new approach to improving detection accuracy.
What are Industrial Control Systems (ICS) and why are they important?
-ICS are systems that manage essential industrial processes, such as energy grids and water treatment plants. These systems use SCADA software to monitor and control physical processes, making them crucial for the functioning of critical infrastructure.
What are some examples of modern ICS attacks mentioned in the talk?
-Examples include the Stuxnet attack on Iranian nuclear facilities, the 2016 Ukrainian power grid attack, and the 2021 Florida water plant attack. These attacks demonstrated how cyber intruders can manipulate SCADA systems to cause physical harm.
What are the limitations of current ICS attack detection techniques?
-Current techniques are often grouped into physical anomaly models and host/network anomaly detection. While physical models can detect sensor anomalies, they often produce false alarms. Host and network models detect noisy attacks but fail against modern, sophisticated attacks that use legitimate SCADA tools.
What is Scaffy, and how does it detect ICS attacks?
-Scaffy is a detection approach that correlates behaviors in the SCADA system with those in the physical side of ICS. It analyzes SCADA execution phases (like initialization, process monitoring, and process authoring) to detect deviations from expected behaviors, signaling potential attacks.
What are SCADA execution phases, and why are they important in detecting attacks?
-SCADA execution phases are stages in the SCADA system's operation, such as initialization, process monitoring, and process authoring. Each phase has unique behaviors, and by monitoring these phases, Scaffy can detect when attackers disrupt the system’s normal operation by violating these phases.
How do attackers exploit SCADA systems in modern attacks?
-Attackers exploit SCADA systems by using legitimate SCADA tools to blend in with normal operations. For example, in the 2021 Florida attack, the intruder manipulated SCADA software to alter water treatment parameters. This allows attackers to avoid detection while causing physical damage.
What is the difference between 'injection' and 'bypass' violations in SCADA?
-Injection violations occur when an attacker executes unauthorized system operations within the SCADA phases. Bypass violations happen when an attacker skips these phases and sends commands directly to the physical system, bypassing the intended process flow.
How does Scaffy model the physical impact of violations in SCADA execution phases?
-Scaffy models the physical impact by correlating SCADA activities with physical process changes. It tracks how actuator states influence physical processes, assigns impact scores to each actuator, and identifies when changes in the physical process are inconsistent with normal operation.
What results were obtained from the experiments conducted with Scaffy?
-In experiments conducted using a diverse physical process infrastructure, Scaffy achieved a 95% detection accuracy rate with an average detection time of 9-10 seconds. These results were consistent with real-world attack scenarios, including injection and execution phase bypass attacks.
How does Scaffy account for delays between SCADA system actions and physical process responses?
-Scaffy accounts for delays by using a steady-state analysis. It checks whether the process is stable or still changing, and adjusts its detection accordingly. If the process has stabilized, the attack is considered to no longer affect the system; if not, Scaffy continues monitoring for anomalies.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифПосмотреть больше похожих видео

What is SCADA, How SCADA Works, Components, Architecture & Applications. SCADA Tutorial

What is SCADA?

What is SCADA? Supervisory Control and Data Acquisition
DISTRIBUTE CONTROL SYSTEM (DCS) SISTEM KONTROL TERDISTRIBUSI - DALAM OTOMASI INDUSTRI
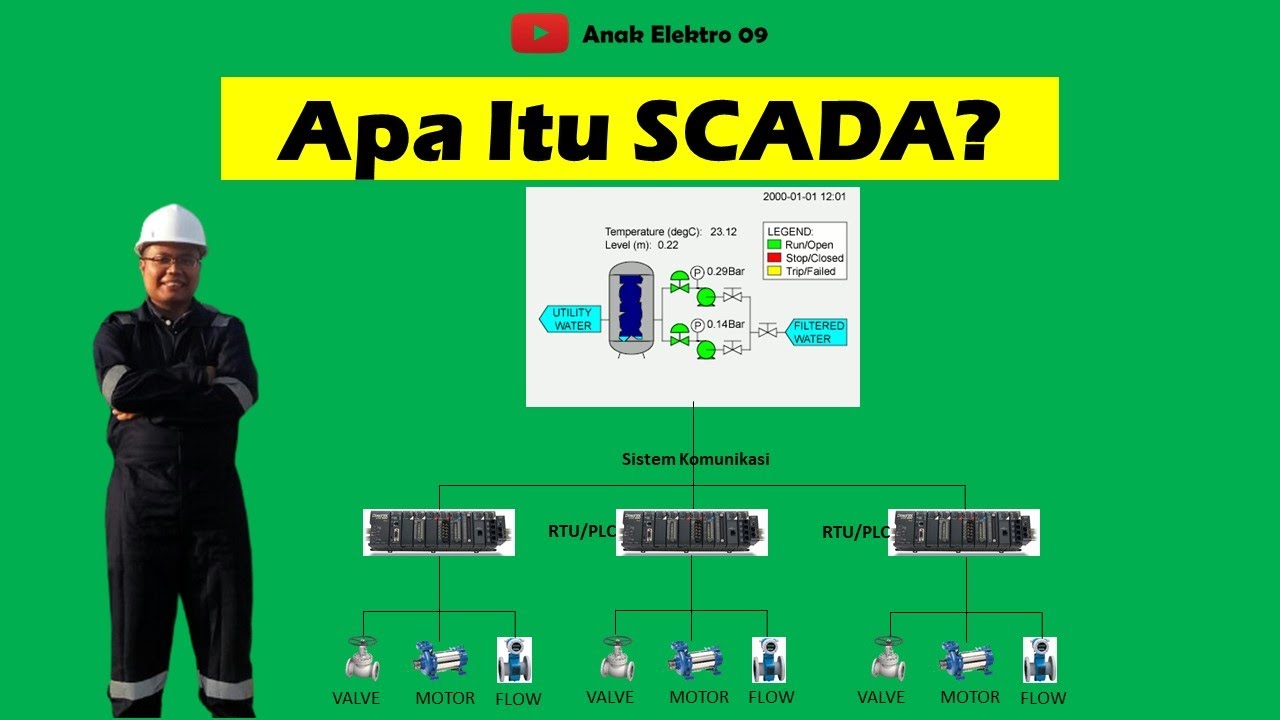
Pengenalan SCADA (Supervisory Control And Data Acquisition)

How Threat Modeling can Influence ICS Security Posture
5.0 / 5 (0 votes)
