Module 5.5 Lab Cross Site Scripting
Summary
TLDRThis video explains the concept of Cross-Site Scripting (XSS) vulnerabilities in websites, focusing on how JavaScript can be executed when malicious scripts are inserted into web pages. It demonstrates how XSS attacks can be tested using different payloads and tools, highlighting the importance of browser security and regular updates. The speaker also discusses how attackers can exploit outdated browsers and social engineering tactics, emphasizing the need for developers to implement proper sanitization and for users to keep their browsers up to date. Ultimately, it warns of the dangers of XSS when combined with tools like Beef or other exploits.
Takeaways
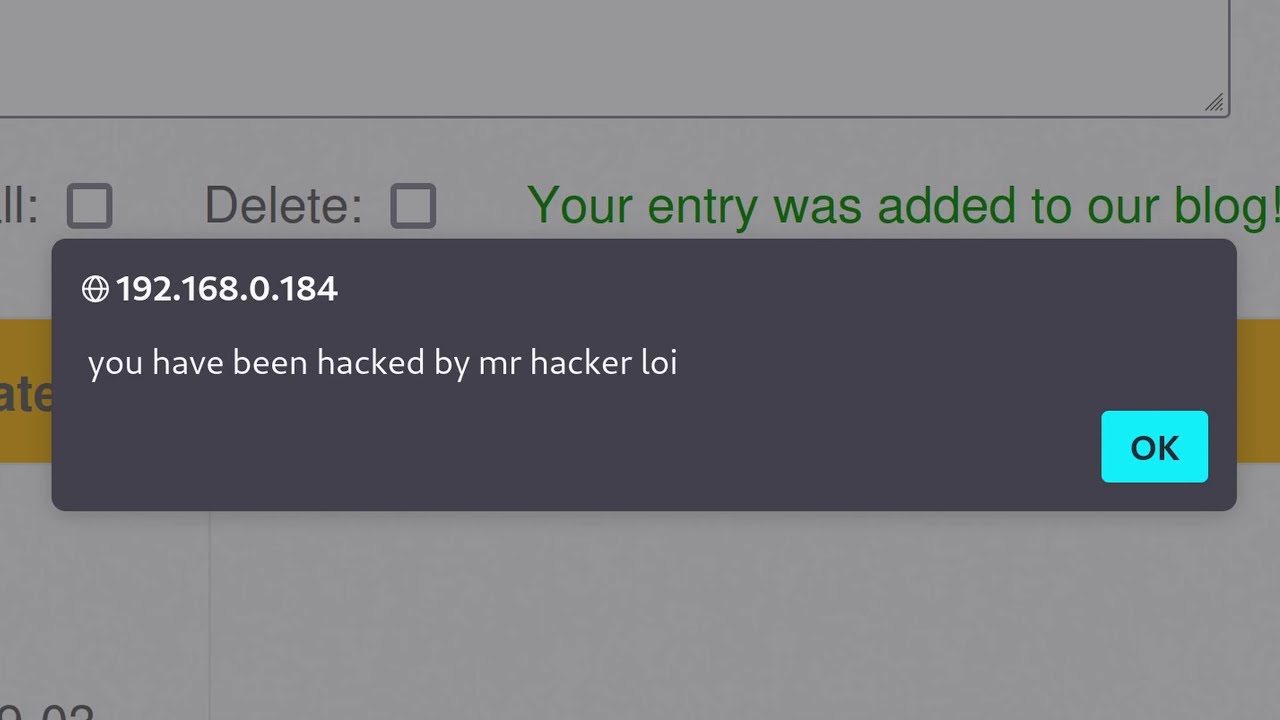
- 😀 XSS (Cross-Site Scripting) occurs when JavaScript code is injected into a website through user inputs, potentially executing malicious scripts in a victim's browser.
- 😀 Input sanitization is critical in preventing harmful scripts from being executed. Websites must filter and sanitize user inputs to protect against XSS attacks.
- 😀 XSS vulnerabilities can be exploited through various payloads. Tools can be used to test different payloads and find vulnerabilities in websites.
- 😀 A simple JavaScript payload that executes an alert can help identify whether the website properly handles inputs and scripts.
- 😀 Attackers can use social engineering tactics, such as fake virus alerts or urgent notifications, to trick users into executing malicious code in their browsers.
- 😀 Tools like BeEF (Browser Exploitation Framework) allow attackers to exploit XSS vulnerabilities by executing JavaScript on victims' browsers remotely.
- 😀 Keeping your browser up to date is essential to protecting against XSS vulnerabilities. Outdated browsers may have security flaws that attackers can exploit.
- 😀 Even if a script doesn’t execute directly, an attacker might still find ways to trigger malicious behavior using different script formats or obfuscation techniques.
- 😀 XSS attacks can be hidden within malicious links. Clicking on such links can trigger harmful scripts on the victim’s browser without their knowledge.
- 😀 Preventing XSS requires a multi-layered approach, including using tools to test vulnerabilities, educating users about security risks, and ensuring secure coding practices.
Q & A
What is the concept of scripting discussed in the video?
-Scripting, specifically in the context of JavaScript, refers to code that executes automatically when a certain action is triggered, such as opening a webpage. The code runs directly within the browser, influencing the webpage's behavior.
What is the initial test mentioned for detecting scripting execution?
-The test involves inputting a string, such as 'Apple,' into a form on a website. If the text 'Apple' is echoed back, it indicates that the script is executing within the browser.
What does it mean when a script is filtered by a website?
-If a script is filtered by a website, it means the website's security mechanisms have prevented the script from executing. For example, inputting a malicious script that doesn't display anything indicates successful filtering by the website.
What is the significance of using different types of payloads in testing?
-Using different payloads allows testers to explore various formats and methods of attack. If one payload works, it suggests a vulnerability in the site's security measures. Tools can automate this testing to save time and effort.
What tools can be used to identify vulnerabilities in a website?
-Various tools, such as automated scanners, can be used to test different payloads and identify vulnerabilities. These tools help in finding weaknesses like Cross-Site Scripting (XSS) without manually testing each script.
How do social engineering tactics relate to Cross-Site Scripting (XSS) attacks?
-Social engineering exploits human psychology to trick users into executing harmful scripts. For example, attackers might display fake alerts about viruses or system performance, luring users into clicking malicious links that trigger XSS attacks.
What is the role of an outdated browser in the effectiveness of XSS attacks?
-An outdated browser might have unpatched security vulnerabilities, making it more susceptible to attacks like XSS. Attackers can exploit these vulnerabilities to gain control over the victim's browser or device.
What happens when an attacker successfully exploits an XSS vulnerability?
-If an attacker successfully exploits an XSS vulnerability, they can execute malicious JavaScript code within the victim's browser, potentially gaining control over the victim's session, stealing data, or performing unauthorized actions.
Why is it important for users to keep their browsers updated?
-Regular browser updates ensure that security patches are applied, making it harder for attackers to exploit known vulnerabilities. Keeping browsers up to date is a key defense against many forms of cyberattacks, including XSS.
What is 'BeEF' and how does it relate to XSS attacks?
-BeEF (Browser Exploitation Framework) is a tool used by attackers to exploit vulnerabilities in browsers. When combined with XSS attacks, BeEF can allow attackers to take control of the victim's browser, leading to further exploitation or data theft.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тариф5.0 / 5 (0 votes)