10. Web Exploit : URL Examitation
Summary
TLDRThis video module focuses on web exploitation, specifically identifying and exploiting vulnerabilities such as BAC (Bypass Authentication Control), SQL Injection, and Cross-Site Scripting (XSS). It explains how understanding URL components—like protocols, subdomains, directories, and query parameters—can reveal potential weaknesses in websites. Viewers will learn how tools like Gobuster can help explore hidden directories, manipulate URL parameters, and test for security flaws. The video aims to provide practical insights into web security for penetration testing and vulnerability assessment.
Takeaways
- 😀 Web exploitation focuses on discovering and exploiting vulnerabilities in websites.
- 😀 The module covers three main weaknesses based on industry standards: BAC (likely XSS), SQL injection, and other common vulnerabilities.
- 😀 The OWASP Top 10 security risks serve as the foundation for this module's content.
- 😀 A penetration tester must understand and recognize various URL components to identify potential vulnerabilities.
- 😀 The primary URL components include protocol, subdomain, domain, directory, file, query, and value.
- 😀 URL components can be exploited, such as testing file extensions, manipulating queries, and injecting malicious code.
- 😀 Penetration testers can bypass file extensions and experiment with queries to identify vulnerabilities like SQL injections.
- 😀 It's essential to understand how to inject payloads into query parameters to test for exploits like SQL injections or XSS.
- 😀 The importance of authentication is highlighted, especially when conducting more advanced attacks like BAC (XSS).
- 😀 The next video will introduce the **SNJ** component, which will likely build on the previous concepts.
Q & A
What is the main focus of this module?
-The main focus of this module is to introduce and explore web exploitation techniques, specifically targeting vulnerabilities like SQL injection, BAC (Buffer Overflow), and XSS (Cross-Site Scripting).
What are the key components of a URL that attackers should be aware of?
-The key components of a URL include the protocol (e.g., HTTP, HTTPS, FTP), subdomain (e.g., www, dev, prod), domain, directory, file, query, and value.
Why is understanding URL components important for penetration testers?
-Penetration testers must understand URL components to identify potential vulnerabilities, such as SQL injection or XSS, by manipulating parameters in the URL to test for weaknesses.
What is SQL Injection and how can it be exploited using URL components?
-SQL Injection is a vulnerability where attackers manipulate query parameters in a URL to inject malicious SQL code, which can then interact with the database and cause unauthorized access or data manipulation.
What is BAC (Buffer Overflow) and how does it relate to web exploitation?
-BAC (Buffer Overflow) is a vulnerability where excessive data overflows into adjacent memory, potentially allowing attackers to gain unauthorized access, crash systems, or execute malicious code. It can be exploited through inputs in web applications, including URL parameters.
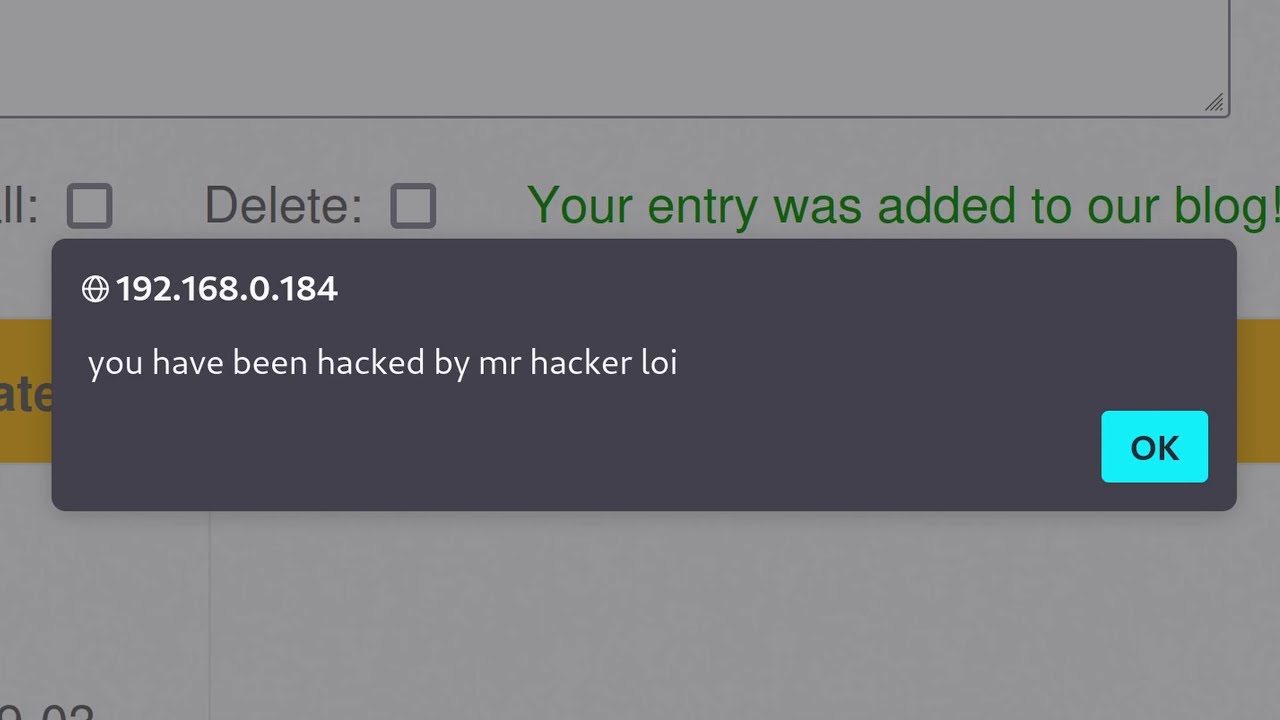
What role does XSS (Cross-Site Scripting) play in web exploitation?
-XSS involves injecting malicious JavaScript into a web page, which can then be executed in the browser of unsuspecting users, leading to data theft, session hijacking, or other malicious activities.
How can a penetration tester use tools like Gobuster to discover vulnerabilities?
-A penetration tester can use tools like Gobuster to discover hidden directories or files on a website by brute-forcing URL paths, allowing them to find unprotected areas that may be vulnerable to exploits like SQL injection.
What is the significance of authentication in exploiting vulnerabilities like BAC?
-Authentication plays a critical role in exploiting vulnerabilities like BAC. Without proper authentication, attackers may bypass security measures and manipulate parameters to execute malicious actions or access unauthorized resources.
What is the importance of understanding query and value parameters in web exploitation?
-Understanding query and value parameters is essential because they can be manipulated by attackers to inject harmful scripts (XSS) or SQL queries, leading to vulnerabilities such as data breaches, site manipulation, or unauthorized access.
How can an attacker exploit a blog website with an ID parameter in the URL?
-An attacker can exploit a blog website with an ID parameter by attempting SQL injection, manipulating the parameter values in the URL to gain unauthorized access to the database or cause unexpected behavior in the site.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Beware of SQL Injection (How it Works) | Security Awareness
Cross Site Scripting (XSS) tutorial for Beginners

Dalfox XSS Automation Scanner for Bug Bounty | Security Awareness

Easy $500 Vulnerabilities! // How To Bug Bounty

Fuzzing XSS Sanitizers for Fun and Profit | Tom Anthony

11. Web Exploit : SQL Injection
5.0 / 5 (0 votes)