Service accounts, IAM roles, and API scopes
Summary
TLDRThis video script discusses service accounts in Google Cloud, focusing on their use for API requests by VM instances. It highlights the importance of assigning minimal necessary permissions using IAM roles and access scopes. The default service account, with Project Editor role, is automatically created but can be limited using access scopes. The script advises against granting full API access, recommending instead the selection of specific API scopes needed by applications, adhering to the principle of least privilege.
Takeaways
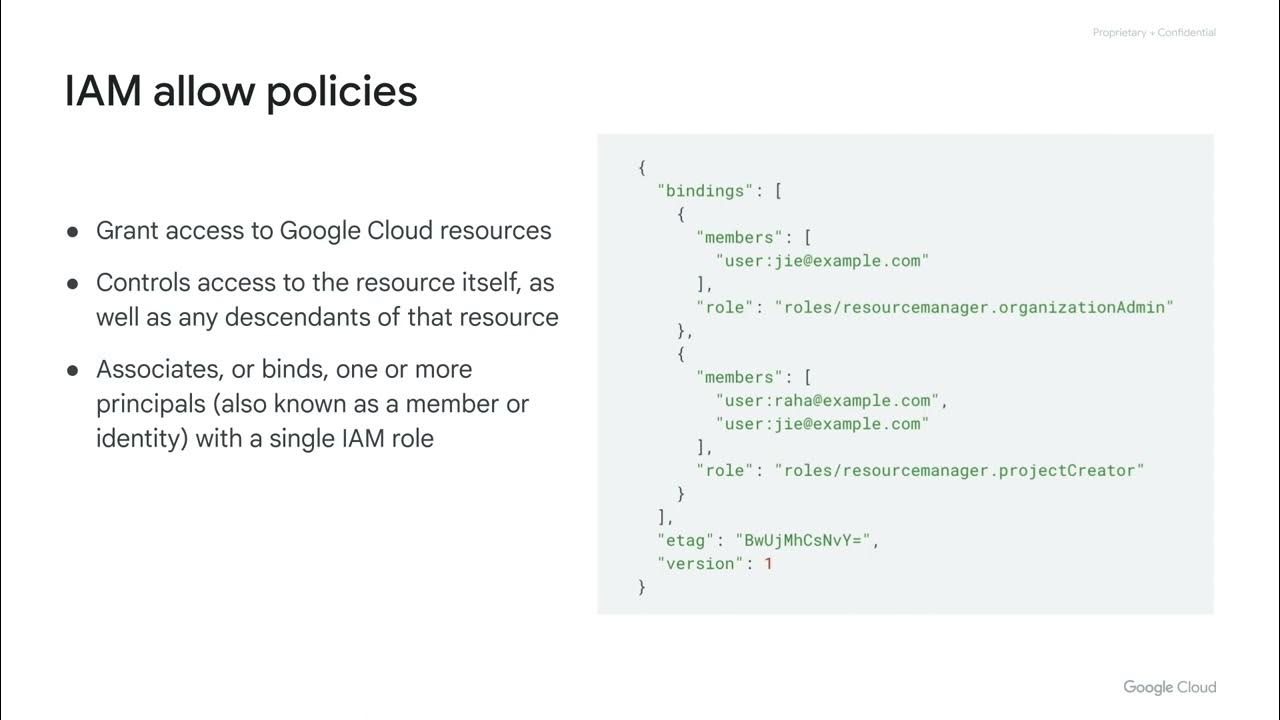
- 🔑 **Service Accounts**: A service account is an identity that resources like VM instances can use to authenticate API requests on behalf of the user.
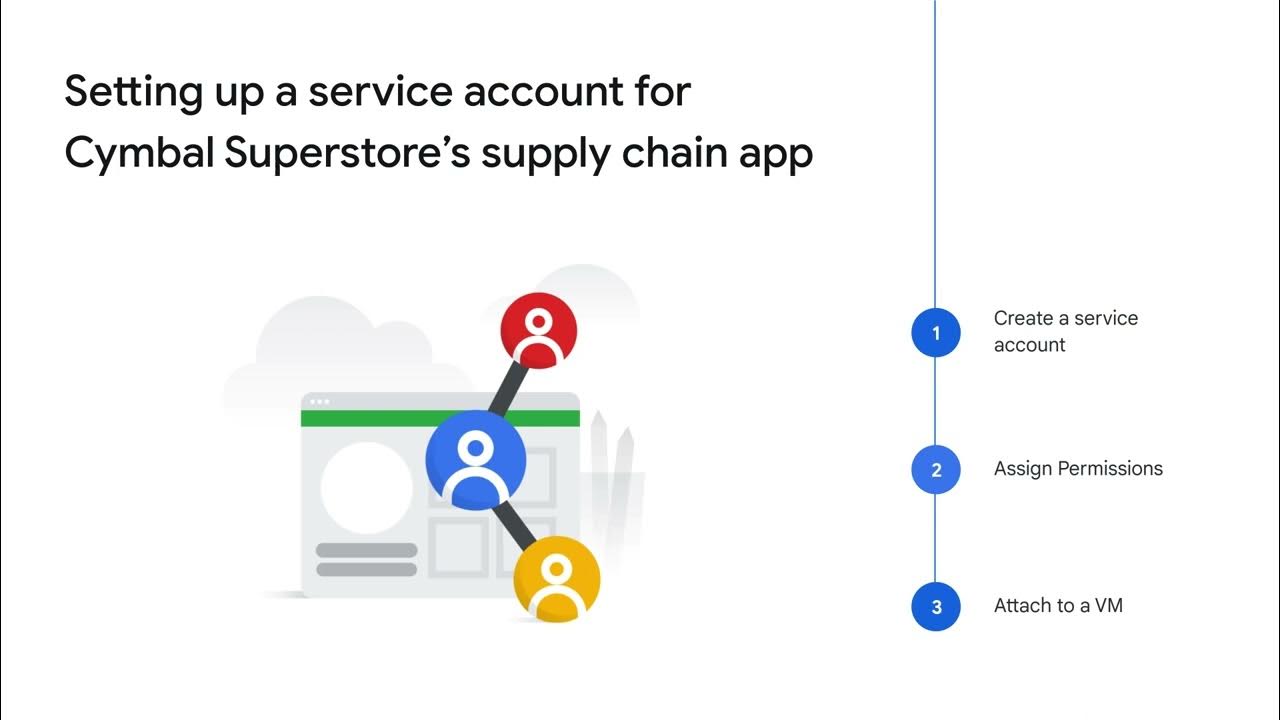
- 💻 **VM Association**: When launching a VM in Compute Engine, a service account can be directly associated with it to authenticate API calls.
- 🚫 **No Service Account Association**: Specifying no service account means that API requests on the VM will not have a default identity and must be manually configured.
- 🛡️ **Principle of Least Privilege**: It's crucial to assign roles and permissions to service accounts with minimal necessary access to safeguard resource management.
- 🆓 **Default Service Account**: Every project has a default service account created when Compute Engine is enabled, initially assigned the Project Editor role.
- 👤 **User-Managed Service Accounts**: Users can create and manage service accounts with specific permissions through IAM roles, providing granular access control.
- 🚫 **No Role, No Access**: Service accounts without assigned roles have no access to services, emphasizing the need for explicit permission granting.
- 🔗 **IAM Roles vs. Access Scopes**: While IAM roles control permissions for user-managed service accounts, access scopes are used for the default service account to limit API access.
- 📋 **Access Scopes**: Access scopes apply on a per-instance basis and must be configured when launching an instance under the default service account.
- ❌ **Avoid Full Access**: Granting full access to all Cloud APIs violates the Principle of Least Privilege and is not recommended.
- ✅ **Selective API Access**: Best practice is to grant access to only the APIs required by the application running on the VM, enhancing security and adherence to best practices.
Q & A
What is a service account in the context of Google Cloud?
-A service account is an identity that a resource, such as a VM instance, can use to run API requests on your behalf.
How is a service account associated with a VM instance in Google Compute Engine?
-A service account can be associated directly with a VM instance when launching it in Compute Engine.
What happens if no service account is specified for a VM instance?
-If no service account is specified, API requests running on the VM will not assume a service account identity by default and would need to be manually configured.
Why is it important to assign roles and permissions to service accounts using the principle of least privilege?
-Service accounts control how resources are managed and used, so assigning them roles and permissions with the principle of least privilege ensures that they only have the necessary access to perform their intended functions, minimizing security risks.
What is the role assigned to the default service account in a Google Cloud project?
-The default service account is assigned the role of Project Editor when Compute Engine is first enabled for the project.
How can you create and manage your own service accounts in Google Cloud?
-You can create and manage your own service accounts using Identity and Access Management (IAM), where you can assign necessary permissions by granting roles.
What is the difference between user-managed service accounts and the default service account in terms of access control?
-User-managed service accounts do not use the 'access scope' concept and instead have permissions controlled through IAM roles assigned to the account, whereas the default service account uses access scopes to control permissions.
What are access scopes and why are they still important even with IAM roles?
-Access scopes are a mechanism for granting permissions to service accounts, and they are still important because they apply on a per-instance basis and must be configured when initiating an instance to run under the default service account.
What does 'Allow default access' provide in terms of permissions for a VM instance?
-The 'Allow default access' scope provides read-only access to Cloud Storage, as well as access to Cloud Logging and Cloud Monitoring, but restricts access to other APIs.
What are the drawbacks of choosing 'allow full access' for a VM instance's service account?
-Choosing 'allow full access' grants full access to all Cloud APIs, which violates the Principle of Least Privilege and is not a best practice due to the potential security risks.
What is the recommended practice when setting access scopes for a VM instance that requires access to specific APIs?
-The recommended practice is to set each API access required individually, granting access only to the APIs necessary for the programs running on the VM, which adheres to the Principle of Least Privilege.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード5.0 / 5 (0 votes)