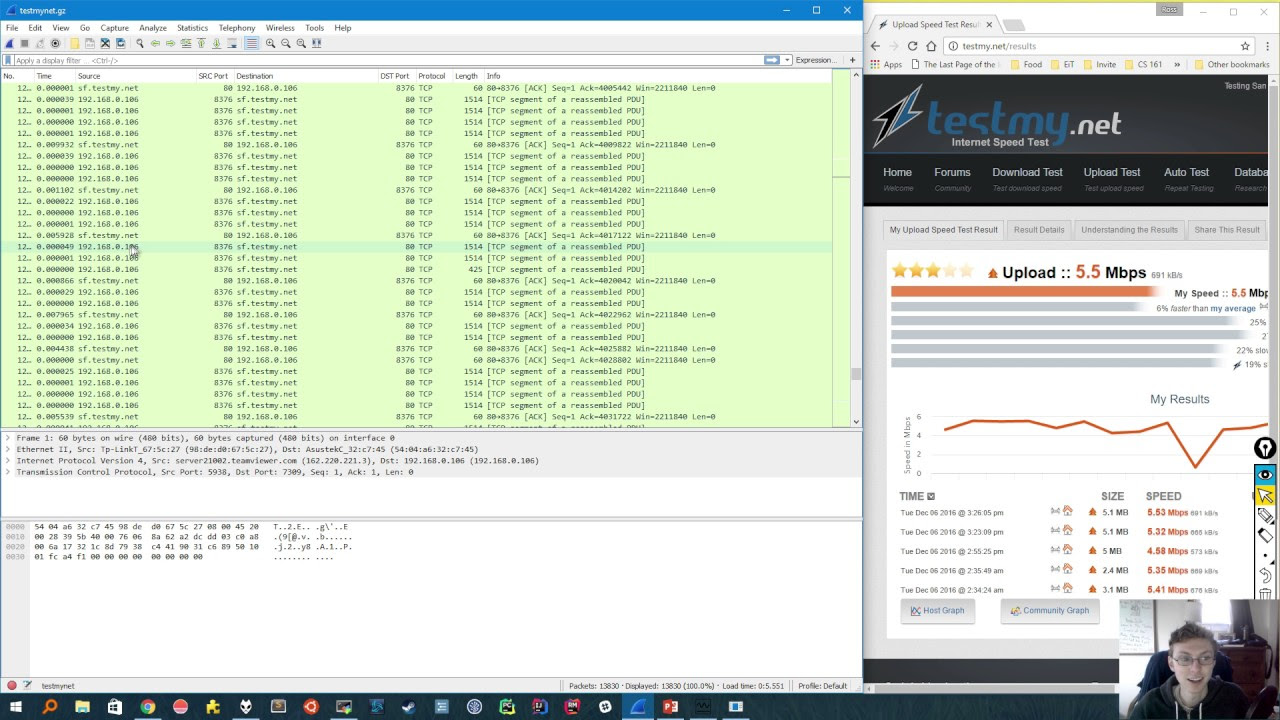
How to Smuggle Data out of the Network with Ping
Summary
TLDRThis video demonstrates how ICMP echo requests (ping) can be abused to exfiltrate data by embedding arbitrary payloads in the ICMP data field. Using a simple two-script toolkit — a generator that chunks a text file into ICMP packets and a parser that reconstructs the file from a pcap — the presenter shows a live Wireshark capture revealing readable text carried in ping packets. The walkthrough covers packet structure, demo requirements (Python, TShark/pyshark, root access), and practical mitigation advice, recommending blocking or tightly restricting ICMP at the perimeter. A clear ethical reminder urges testing only with authorization and non-sensitive data.
Takeaways
- 😀 ICMP ping requests can be used to exfiltrate data from enterprise networks, bypassing security measures like firewalls.
- 😀 Many corporate firewalls use Application Layer Gateways (ALGs) that inspect traffic at the application layer to prevent unauthorized access and data leaks.
- 😀 ICMP ping packets have an optional data field, which can be exploited to carry and send sensitive information without detection.
- 😀 The 'Ping Smuggler' Python script can break up a file into chunks and embed it in multiple ping packets, sending the data across the network to a receiver.
- 😀 Simple network tools like ping, despite their apparent simplicity, can be misused to send data covertly if not properly monitored or blocked.
- 😀 A firewall may block typical malicious traffic, but common protocols like ICMP ping may still be allowed, creating an exploitable vulnerability.
- 😀 In a corporate setting, blocking ICMP ping requests to the internet entirely is one of the most effective ways to prevent data exfiltration.
- 😀 **Wireshark** can be used to inspect ping packets in real-time, allowing an attacker to capture and read the data transmitted in the optional field.
- 😀 The tutorial demonstrated using Wireshark and a Python parser script to extract text data embedded within ping packets.
- 😀 Blocking ping requests entirely or configuring advanced firewalls to inspect ICMP payloads are practical measures to mitigate data exfiltration risks.
- 😀 Many organizations are not prepared for the risk of ping-based data exfiltration, which can easily be performed with simple scripts and tools.
Q & A
What is the main objective of the video on network troubleshooting using Wireshark?
-The main objective is to demonstrate how ICMP ping packets can be misused to exfiltrate data from an enterprise network and to explain why many organizations block ping traffic at their firewalls for security reasons.
Why do many enterprises block ICMP ping requests at their perimeter firewalls?
-Enterprises block ping requests because ICMP packets include an optional data field that can carry arbitrary data, which attackers can exploit to secretly transfer sensitive information outside the network.
What is an Application Layer Gateway (ALG) firewall and how does it differ from a traditional firewall?
-An ALG firewall inspects network traffic up to the application layer, not just source and destination IPs and ports. It enables deeper inspection and controls for protocols like HTTP, HTTPS, and TLS, making it more capable than traditional stateful firewalls.
What is data exfiltration and why is it a concern for organizations?
-Data exfiltration refers to the unauthorized transfer of data from an internal network to an external destination. It is a major security concern because sensitive corporate or personal data can be leaked or stolen without detection.
How can ICMP ping packets be used for data exfiltration?
-Attackers can insert pieces of data into the optional data field of ICMP ping packets. These packets can traverse firewalls if ping is allowed, and the data can be captured and reassembled by a receiver outside the network.
What is the 'Ping Smuggler' project mentioned in the video?
-Ping Smuggler is a simple proof-of-concept tool consisting of two Python scripts: a generator that embeds text data into ICMP ping packets, and a parser that extracts and reconstructs the data from captured network traffic.
What tools and software are required to replicate the Ping Smuggler demonstration?
-The demonstration requires Python (preferably on Linux), Wireshark or TShark for capturing packets, the PyShark Python module, and administrative privileges on the sending system to allow raw socket access.
How does the Ping Smuggler generator and parser work together?
-The generator script splits a text file into chunks and embeds each piece in an ICMP ping packet. The packets are sent to a receiver that captures the traffic. The parser script then processes the capture file to reconstruct the original message.
What mitigation strategies are recommended to prevent ICMP-based data exfiltration?
-Recommended mitigations include blocking outbound ICMP traffic at firewalls, restricting which systems can send ping requests, implementing DLP and egress monitoring, and inspecting ICMP payloads where feasible.
Why is inspecting or decrypting ICMP payloads not always a practical mitigation method?
-Inspecting ICMP payloads is challenging because attackers can easily encrypt or obfuscate data, making detection difficult. Unlike standardized encrypted protocols like TLS, custom encryption within ICMP packets is unpredictable and hard to manage at scale.
What is the broader security lesson from this demonstration?
-The key takeaway is that even simple network tools like ping can be exploited for data exfiltration. Security teams should not overlook basic protocols when designing network defenses and should enforce least-privilege and egress control principles.
How can organizations test whether ICMP ping is allowed in their environment?
-Users can attempt to ping a public address such as Google’s 8.8.8.8 from within the network. If the ping succeeds, outbound ICMP is likely permitted, and the security team should review whether that configuration is necessary.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantVoir Plus de Vidéos Connexes
5.0 / 5 (0 votes)