Microsoft Entra ID Beginner's Tutorial (Azure Active Directory)
Summary
TLDRMicrosoft Entra ID offers a unified identity and access management solution, simplifying secure access to work applications across clouds with a single sign-in. It enhances security through multifactor authentication, risk assessment, and passwordless login. The script guides users and admins through setup, user and group management, and device integration, emphasizing Entra ID's role in protecting identity and information.
Takeaways
- 🔒 Microsoft Entra ID allows for secure, unified access to various online services using a single sign-on with your work email address.
- 🆔 It serves as an identity and access management solution, handling both authentication (verifying identity) and authorization (granting access to services).
- 🔄 Microsoft Entra ID replaces Azure Active Directory and comes with new updates while retaining a familiar interface for those already acquainted with Azure AD.
- 🧑💻 The solution simplifies the management of multiple app and service logins, reducing the risk of credential reuse and potential security breaches.
- 👥 It provides a centralized location for IT and help desk to manage user accounts, including creation, changes, password resets, and more.
- 🌐 Entra ID supports multi-cloud identity management, extending its services to non-Microsoft cloud apps like Google, Salesforce, and AWS.
- 🔑 It promotes stronger security measures with support for multi-factor authentication and passwordless login options.
- 📊 Entra ID includes real-time sign-in risk assessment through Conditional Access, enhancing security by considering user risk levels and device compliance.
- 🛠️ The Microsoft Entra Admin Center is the hub for managing identities, including users, groups, and enterprise applications, with a focus on simplicity and shared backend service.
- 🔄 Hybrid management allows Entra ID to work with on-premises directory services like Active Directory, synchronizing services for a seamless experience.
- 📝 Entra ID offers detailed audit logs and sign-in reports, giving administrators insight into user activities and access patterns.
Q & A
What is Microsoft Entra ID and what does it enable users to do?
-Microsoft Entra ID is an identity and access management solution that allows users to securely access all their online services for work using their work email address, without needing to remember multiple passwords. It consolidates identity services and enables passwordless login, multi-factor authentication, and real-time sign-in risk assessment.
Why is it beneficial to consolidate identity services with Microsoft Entra ID?
-Consolidating identity services with Microsoft Entra ID simplifies the process of remembering multiple login credentials, enhances security with features like multi-factor authentication, and allows for centralized management of user identities and access permissions across various services, including non-Microsoft ones.
How does Microsoft Entra ID help with the security of user credentials?
-Microsoft Entra ID helps secure user credentials by offering multi-factor authentication and passwordless login options. It also assesses sign-in risk in real-time, blocking unauthorized access attempts from unfamiliar locations or devices.
What is the relationship between Microsoft Entra ID and Azure Active Directory?
-Microsoft Entra ID is the new name for Azure Active Directory. While there are a few updates, the transition is meant to be familiar for those who are already acquainted with Azure Active Directory.
How does Microsoft Entra ID support identity management for non-Microsoft services?
-Microsoft Entra ID can be configured as the identity provider for non-Microsoft services such as Google, Salesforce, and AWS. This allows for a unified system to manage identities across different platforms.
What is the role of the Microsoft Entra Admin Center in identity management?
-The Microsoft Entra Admin Center is the portal where identity admins can manage user accounts, groups, roles, authentication methods, and access to various applications and services. It also allows for the configuration of hybrid management with on-premises directory services like Active Directory.
What are the advantages of using groups in Microsoft Entra ID for identity management?
-Groups in Microsoft Entra ID allow for logical organization of users, devices, and managed identities. They can be static or dynamic, with dynamic groups automatically enrolling members based on set properties, simplifying management and access control.
How does Microsoft Entra ID support multi-factor authentication?
-Microsoft Entra ID supports multiple authentication methods for multi-factor authentication, including biometric sign-in with Windows Hello for Business, FIDO2 security keys, the Authenticator app on mobile phones, and other options beyond just password-based authentication.
What is Conditional Access in the context of Microsoft Entra ID?
-Conditional Access in Microsoft Entra ID is a feature that assesses risk in real-time and makes access decisions based on user risk level, IP location, device compliance, and the applications being accessed. It can allow, block, or require additional authentication strength based on predefined controls.
How does Microsoft Entra ID integrate with device management?
-Microsoft Entra ID integrates with device management by using device state to assess sign-in risk in real-time and enabling single sign-on through Microsoft Entra join. This allows seamless access to work resources after signing into a device, and it works with tools like Microsoft Intune for broader device management tasks.
What resources are available for further learning about Microsoft Entra ID?
-For more information on Microsoft Entra ID, one can visit aka.ms/EntraDocs, which is a resource provided for documentation and further learning about the service.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen

20 Identidade, acesso e segurança - Parte 1
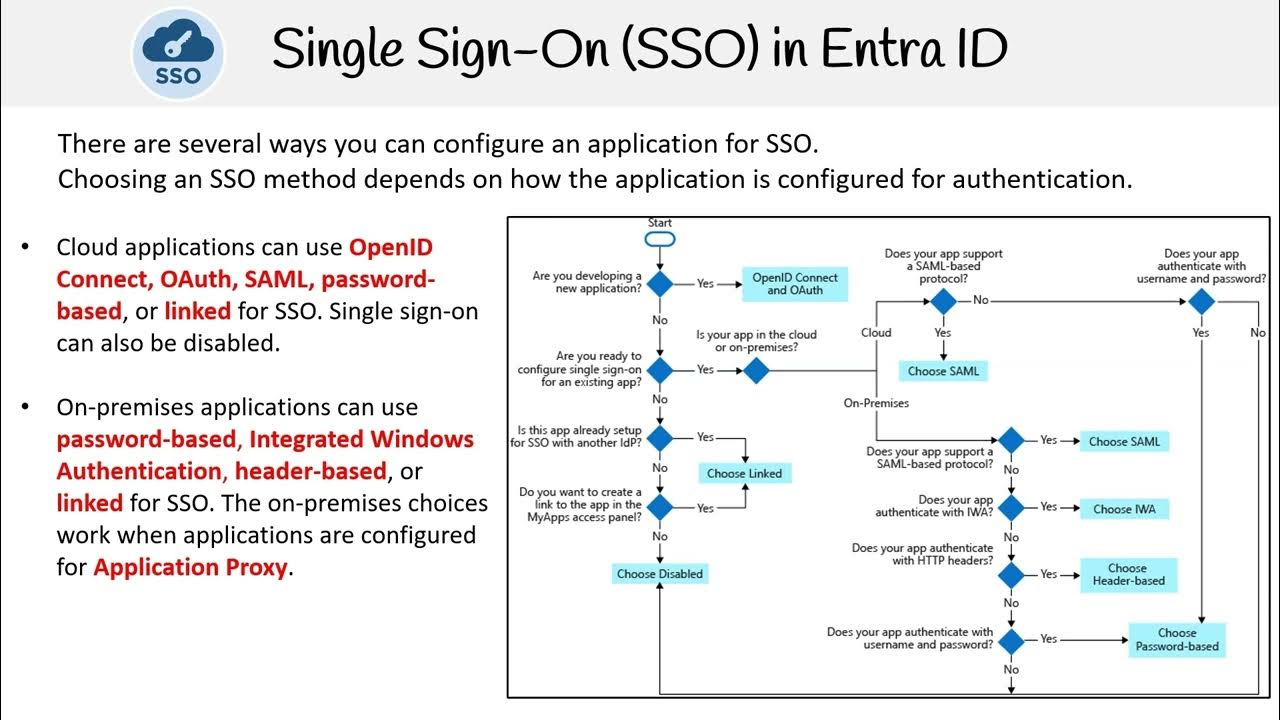
AZ 305 — Single Sign On SSO
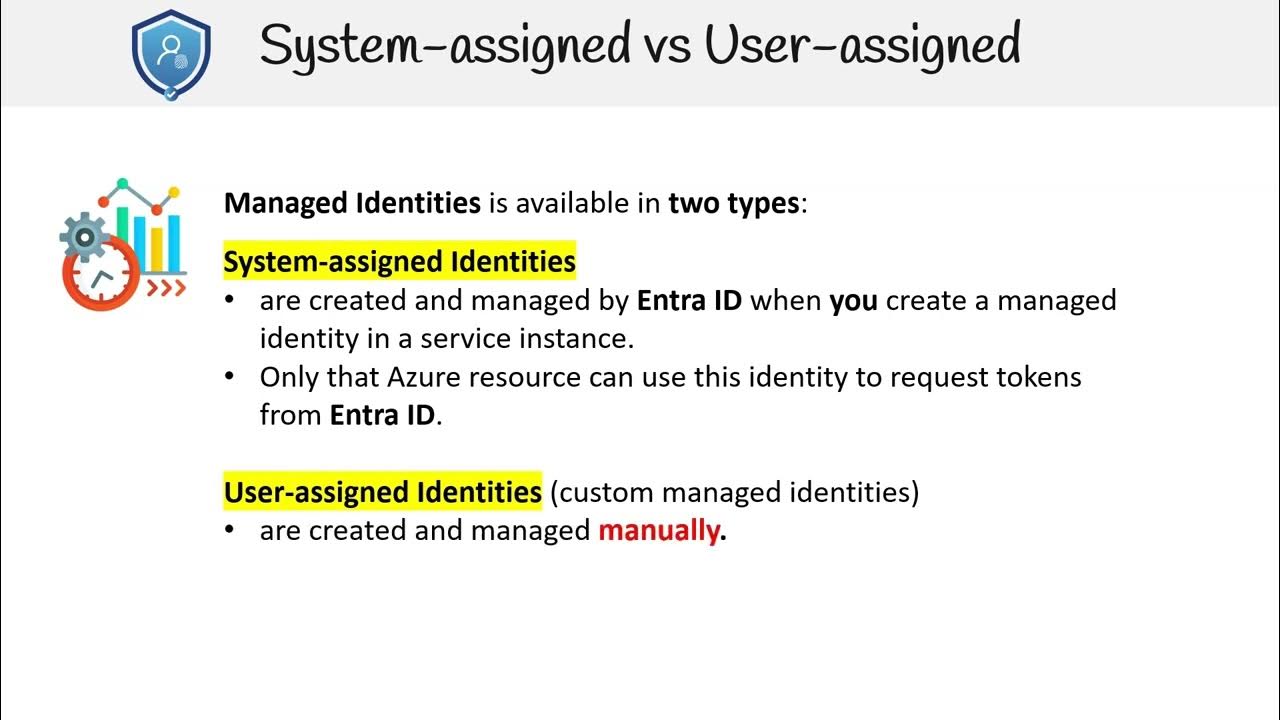
AZ 305 — Managed Identities

What Is Single Sign-on (SSO)? How It Works

CompTIA Security+ SY0-701 Course - 4.6 Implement and Maintain Identity & Access Management - PART A

Episode 30: Cloud Identity Services - Identity Authentication Service
5.0 / 5 (0 votes)
