IAM authorization best practices
Summary
TLDRThis video emphasizes best practices for managing IAM (Identity and Access Management) roles and policies. It recommends grouping resources within projects, ensuring proper inheritance of policies, and following the principle of least privilege. It also highlights the importance of granting roles to groups rather than individuals, simplifying access management. Additionally, the video offers guidelines for service account management, such as cautious role granting, clear naming conventions, and implementing key rotation policies to enhance security and control.
Takeaways
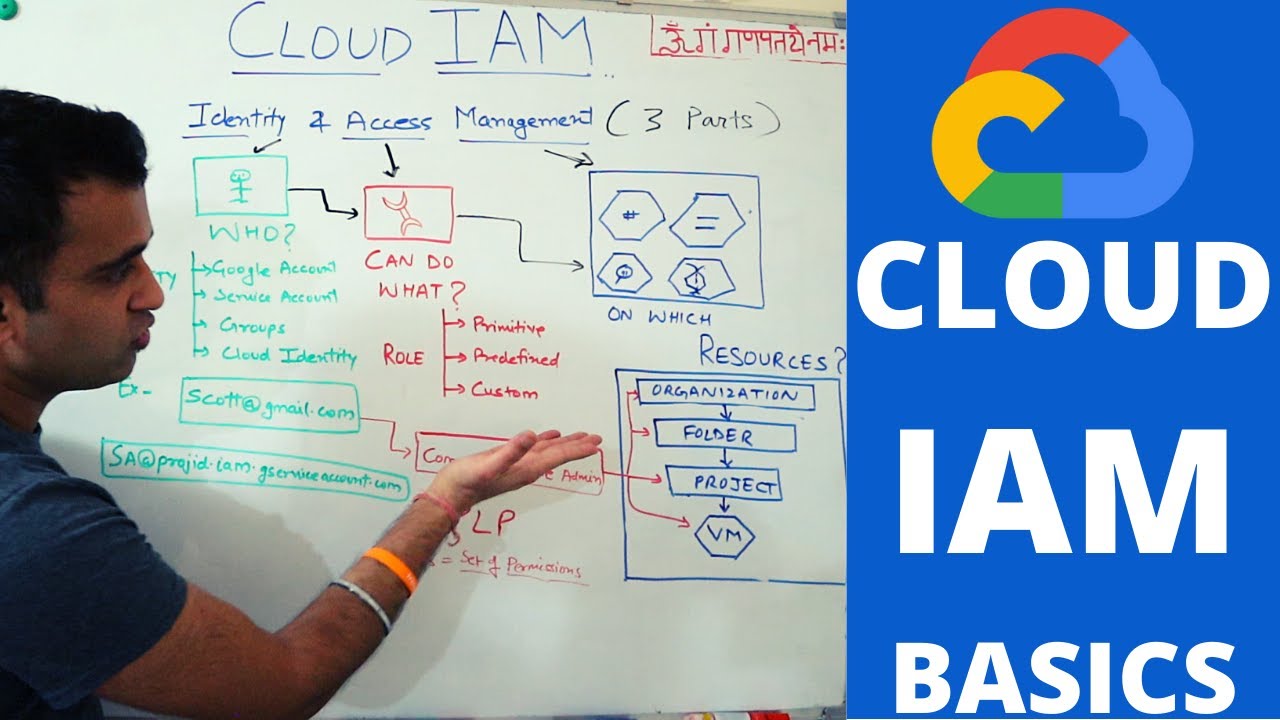
- 😀 Use projects to group resources with the same trust boundary to organize your resources effectively.
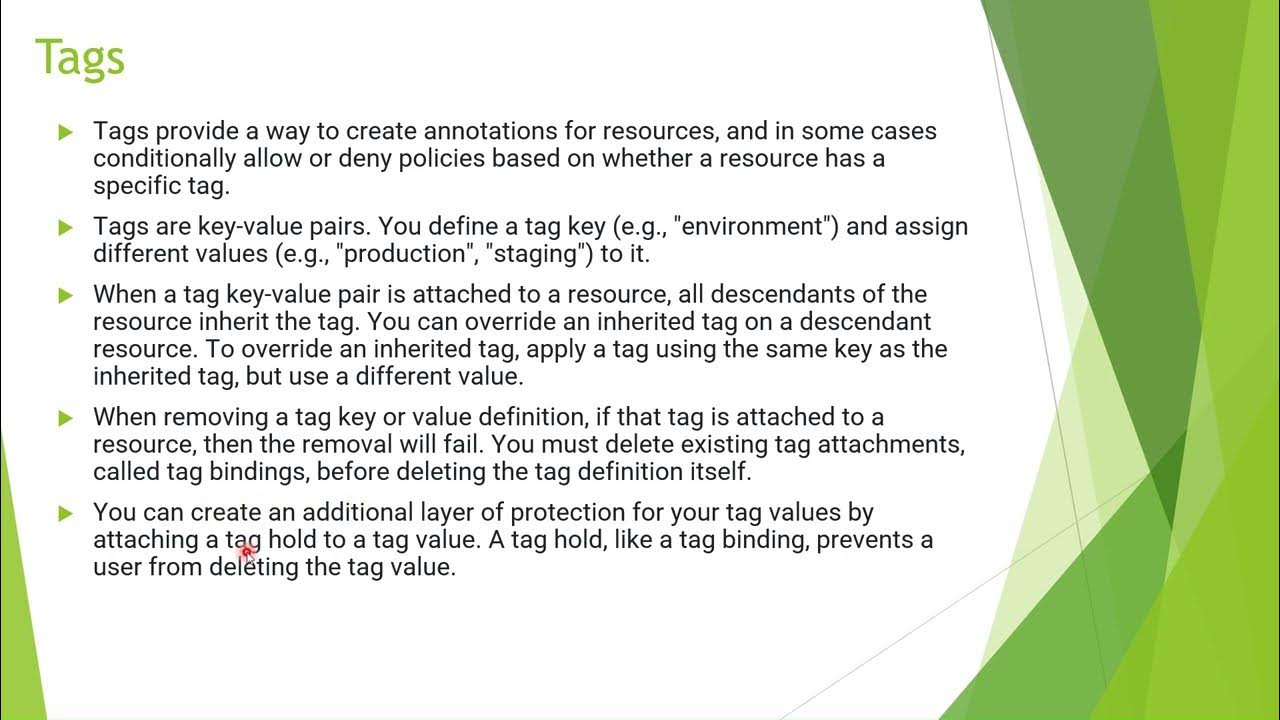
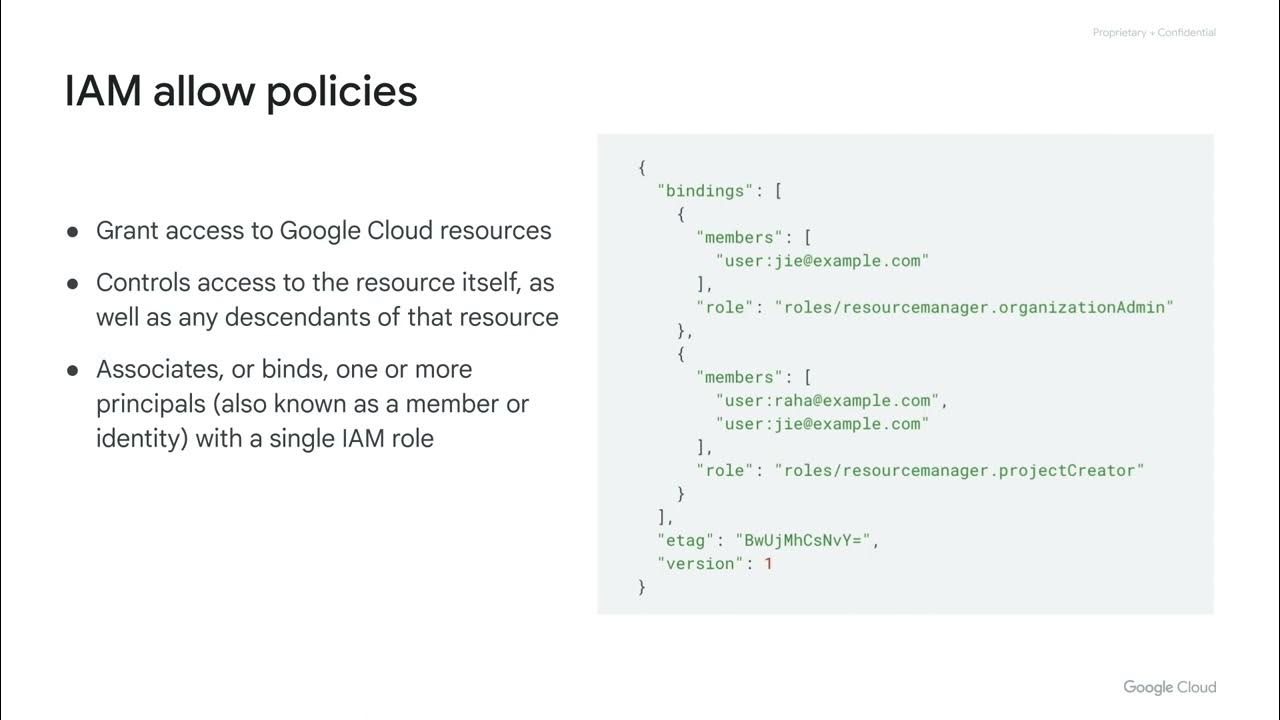
- 😀 Always check the policies granted on each resource and recognize inheritance to ensure consistency.
- 😀 Apply the principle of least privilege when granting roles to ensure minimal access.
- 😀 Audit policies regularly using Cloud Audit Logs to track changes and ensure proper access control.
- 😀 Grant roles to groups rather than individuals to simplify access management and updates.
- 😀 Regularly audit the memberships of groups used in IAM policies to ensure only the appropriate users have access.
- 😀 Control the ownership of Google groups used in IAM policies to avoid unauthorized changes.
- 😀 Utilize multiple groups for better access control and management of resources.
- 😀 Be cautious when granting the Service Account Users role, as it provides access to all the resources the service account can access.
- 😀 When creating a service account, give it a display name that clearly identifies its purpose, following an organization-wide naming convention.
- 😀 Implement key rotation policies and methods for service account keys to maintain security and prevent key misuse.
Q & A
What is the importance of using projects to group resources in IAM?
-Using projects to group resources that share the same trust boundary helps in organizing and securing resources effectively. It allows for better control over policies and permissions, ensuring that resources are managed with appropriate access control.
Why is it crucial to understand resource hierarchy in IAM?
-Understanding the resource hierarchy ensures that policies are applied correctly through inheritance. This understanding helps in ensuring least privilege access and preventing overly broad permissions across resources.
What does the principle of least privilege mean in IAM?
-The principle of least privilege means granting users and resources only the minimum access needed to perform their tasks. This reduces the potential for unauthorized access and minimizes the impact of security breaches.
How does policy inheritance affect IAM?
-Policy inheritance allows permissions granted at higher levels in the hierarchy to be applied to resources below them. It is important to recognize this inheritance to ensure that the correct permissions are granted without inadvertently giving excessive access.
Why should roles be granted to groups instead of individuals?
-Granting roles to groups rather than individuals simplifies role management. It allows for easier updates to group memberships without needing to modify IAM policies, providing more control and reducing administrative overhead.
What should be audited when using groups in IAM policies?
-When using groups in IAM policies, it is important to audit the memberships of the groups to ensure they reflect the correct roles and responsibilities. This helps to maintain security and prevent unauthorized access.
How does using multiple groups improve IAM control?
-Using multiple groups allows for more granular control over access. Different groups can be assigned different roles or permissions, making it easier to manage access levels based on job responsibilities and minimizing unnecessary access.
What is the risk of granting the Service Account Users role?
-Granting the Service Account Users role gives access to all the resources that the service account can access. This broad access can lead to security risks if not properly managed, as it might inadvertently grant more access than necessary.
What naming convention should be used for service accounts?
-Service accounts should have clear and descriptive display names that identify their specific purpose. Adopting a standardized naming convention across the organization helps in managing and identifying service accounts more effectively.
Why is key rotation important for service accounts in IAM?
-Establishing key rotation policies for service account keys is critical to maintaining security. Regularly rotating keys ensures that old, potentially compromised keys are no longer valid, reducing the risk of unauthorized access.
Outlines

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenMindmap

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenKeywords

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenHighlights

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenTranscripts

Dieser Bereich ist nur für Premium-Benutzer verfügbar. Bitte führen Sie ein Upgrade durch, um auf diesen Abschnitt zuzugreifen.
Upgrade durchführenWeitere ähnliche Videos ansehen
5.0 / 5 (0 votes)