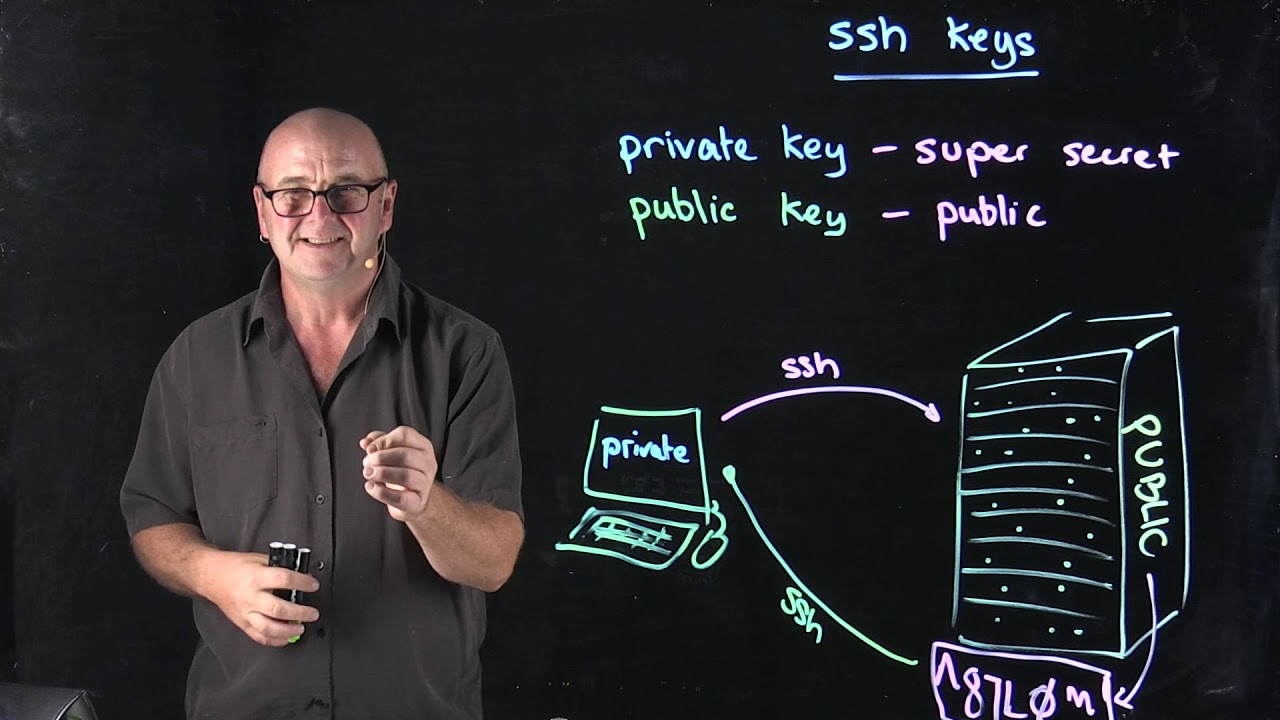
How Secure Shell Works (SSH) - Computerphile
Summary
TLDRThis video explores the Secure Shell (SSH) protocol, developed in the mid-90s by Tatu Ylonen to encrypt data transmission for secure remote connections. It discusses SSH's packet structure, encryption, and authentication process, highlighting its ability to multiplex multiple connections and tunnel TCP connections securely.
Takeaways
- 😀 SSH stands for 'Secure Shell' and was developed in the mid-90s as a secure replacement for protocols like Telnet, rlogin, and RSH.
- 🔒 SSH encrypts data transmission to prevent eavesdropping and protect sensitive information, such as passwords, from being intercepted over the network.
- 💻 The initial connection in SSH is a standard TCP connection, but it can also work over other reliable network connections like RS-232 or WebSockets.
- 📦 SSH breaks data into packets, including packet length, padding, payload, and a message authentication code to ensure data integrity and security.
- 🔑 Encryption and message authentication algorithms used by SSH are negotiated and agreed upon by both the client and the server at the beginning of the session.
- 🔄 SSH leaves the packet length unencrypted to allow the receiver to know the size of incoming data, while encrypting the padding length, payload, and padding.
- 🗜 SSH offers the option to compress the payload before encryption, using standard algorithms like zlib, to optimize data transfer.
- 🔄 The encryption process in SSH is continuous, using vectors from the previous packet to encrypt the next, ensuring a secure and seamless data stream.
- 🛠️ On top of the encrypted packet layer, SSH creates multiple channels for data transfer, allowing for multiplexing of connections and efficient resource use.
- 🔄 SSH supports tunneling TCP connections, enabling secure access to services behind a firewall and the forwarding of graphical user interface sessions.
- 🔄 SSH connections can be persistent, allowing for multiple sessions or forwarded connections to reuse the same underlying TCP connection.
Q & A
What does SSH stand for and what was its original purpose?
-SSH stands for 'Secure Shell'. It first appeared in the mid-90s as a secure replacement for protocols like Telnet, rlogin, and RSH, which transmitted data in clear text over the network.
Why was SSH developed?
-SSH was developed by Tatu Ylonen in 1995 to encrypt the data transmitted between two machines over the network, ensuring that sensitive information such as passwords could not be intercepted by anyone with access to the network.
What was the main vulnerability of the older protocols like Telnet and rlogin?
-The main vulnerability of older protocols was that they transmitted all data in clear text, making it easy for anyone with a packet sniffer to see everything being done on the remote machine, including passwords.
How does SSH encrypt the connection between two machines?
-SSH encrypts the connection by breaking the data down into packets, adding padding for security, and then encrypting the payload, padding, and any message authentication code. The encryption algorithms are selected by the server and client at the beginning of the connection.
What is the purpose of adding padding to SSH packets?
-Padding is added to SSH packets to make it harder for an attacker to detect patterns in the data being transmitted, as it includes random bytes that do not carry any meaningful information.
Can SSH only be used over TCP connections?
-No, SSH can use any reliable network connection. While it commonly uses TCP, it can theoretically be run over other types of connections like RS-232 or web sockets.
What is the purpose of the message authentication code in SSH packets?
-The message authentication code ensures the integrity and authenticity of the data within the packet, confirming that the data has not been tampered with during transmission.
Can compression be applied to SSH payload?
-Yes, compression can be applied to the payload of SSH packets using standard algorithms like zlib, which can help reduce the amount of data being transmitted.
What is the significance of the packet length being unencrypted in SSH?
-The packet length is left unencrypted so that the receiving end knows how much data to expect in the packet, which is necessary for correctly processing the incoming data stream.
What is the concept of 'channels' in SSH and why are they used?
-Channels in SSH are multiplexed connections that allow for multiple simultaneous connections over a single SSH session. They enable features like forwarding TCP connections and running multiple interactive sessions.
How does SSH handle multiple connections and sessions?
-SSH handles multiple connections and sessions by creating channels on top of the encrypted packet layer. This allows for the simultaneous management of multiple interactive sessions and forwarded connections.
What additional functionality does SSH provide beyond a simple shell connection?
-Beyond a simple shell connection, SSH provides functionality such as port forwarding, X11 forwarding for graphical user interfaces, and the ability to keep connections alive for reuse, enhancing its versatility in various network environments.
Outlines

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنMindmap

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنKeywords

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنHighlights

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنTranscripts

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآن5.0 / 5 (0 votes)