MDE Tutorial -13 - Endpoint Detection and Response (EDR) in Microsoft Defender for Endpoints
Summary
TLDRThis video tutorial delves into Microsoft Defender for Endpoint's Endpoint Detection and Response (EDR) feature. It explains EDR's role in identifying and responding to threats on various devices, including laptops and servers. The tutorial covers creating an EDR policy in block mode, testing it on a device, and validating EDR and antivirus status. It also discusses the process of alerts converting to incidents and the importance of keeping antivirus software up to date. Viewers are guided through policy creation in the Microsoft Endpoint Manager and testing the policy's effectiveness.
Takeaways
- 😀 The video is a tutorial on Microsoft Defender for Endpoint, focusing on Endpoint Detection and Response (EDR).
- 🔍 EDR stands for Endpoint Detection and Response, a security solution that prioritizes alerts and provides visibility into malicious attacks on devices like laptops, desktops, and servers.
- 🛡️ EDR operates in block mode to provide additional protection when other antivirus solutions are active, even if Microsoft Defender Antivirus is not running.
- 📝 The tutorial covers creating a policy for EDR in block mode, testing the policy on a device, and validating EDR and antivirus status.
- 🚨 EDR can trigger alerts based on the severity of the threat, categorizing them as high, medium, or non-impactful, and providing full visibility into the attack process.
- 🔄 EDR automatically takes action to remediate threats detected by security analytics, creating incidents when similar alerts occur from multiple machines.
- 🔄 The video explains the process of how EDR works, moving from detection to response, prediction, and prevention of threats.
- 📋 EDR in block mode allows Microsoft Defender Antivirus to take action on breach behavior detections and respects existing exclusions set in the antivirus.
- 💻 The tutorial demonstrates creating an EDR policy in the Microsoft Endpoint Manager console, including settings for sample sharing and telemetry reporting.
- 🔄 The presenter shows how to validate the EDR and antivirus status using command prompts and PowerShell, including checking the running mode of EDR.
- 🔄 The video concludes with practical steps to sync the policy on a test machine and verify the EDR block mode settings in the Microsoft Security Center.
Q & A
What does EDR stand for and what is its primary focus?
-EDR stands for Endpoint Detection and Response. Its primary focus is on detecting and responding to threats on endpoint environments such as laptops, desktops, servers, and tablets.
How does EDR prioritize alerts when a malicious attack occurs?
-EDR prioritizes alerts based on the level of threat, categorizing them as high, medium, or low impact, and provides visibility into the full scope of the breach.
What actions does EDR take when a threat is detected?
-When a threat is detected, EDR triggers an alert and can take automatic actions to remediate the threat, providing complete visibility into how the attack happened and what processes were involved.
Can EDR work alongside other antivirus solutions?
-Yes, EDR can work with other antivirus solutions, including Microsoft Defender Antivirus, providing additional protection when the primary antivirus solution misses something or in case of post-breach detection.
What is the purpose of EDR block mode?
-EDR block mode provides additional protection against malware when the primary antivirus is running in passive mode or if another antivirus is active on the machine.
How can existing exclusions in antivirus software affect EDR?
-Existing exclusions in antivirus software will be respected during EDR scanning. If a file or application is excluded in the antivirus settings, EDR will not affect those exclusions.
What command can be used to check the status of Microsoft Defender Antivirus and EDR?
-The command 'sc query windefend' can be used in the command prompt to check if the Microsoft Defender Antivirus service is running. For EDR status, PowerShell command 'Get-MpComputerStatus | Select AVRunningMode' can be used.
How long does it take to disable EDR block mode once the decision is made?
-It takes 30 minutes to disable EDR block mode once the decision to disable it has been made.
What is the process for creating an EDR policy in Microsoft Endpoint Manager?
-To create an EDR policy, navigate to Endpoint Security in Microsoft Endpoint Manager, select Endpoint Detection and Response, and follow the steps to create a policy, including naming it, setting options, assigning it to a group, and validating the policy.
How can you test if EDR block mode is enabled on a device?
-You can test if EDR block mode is enabled on a device by using the PowerShell command mentioned earlier. If EDR is in block mode while another antivirus is running, the command will output 'EDR in block mode'.
What is the role of scope tags in EDR policy creation?
-Scope tags in EDR policy creation allow administrators to define specific groups or organizational units to which the policy should apply, ensuring that the policy is targeted to the correct devices or users.
Outlines

此内容仅限付费用户访问。 请升级后访问。
立即升级Mindmap

此内容仅限付费用户访问。 请升级后访问。
立即升级Keywords

此内容仅限付费用户访问。 请升级后访问。
立即升级Highlights

此内容仅限付费用户访问。 请升级后访问。
立即升级Transcripts

此内容仅限付费用户访问。 请升级后访问。
立即升级浏览更多相关视频

Microsoft 365 Defender for Endpoint? Good Enough for your Business?

Microsoft Defender for Business EDR to XDR Security Upgrade Using Microsoft 365 Business Premium
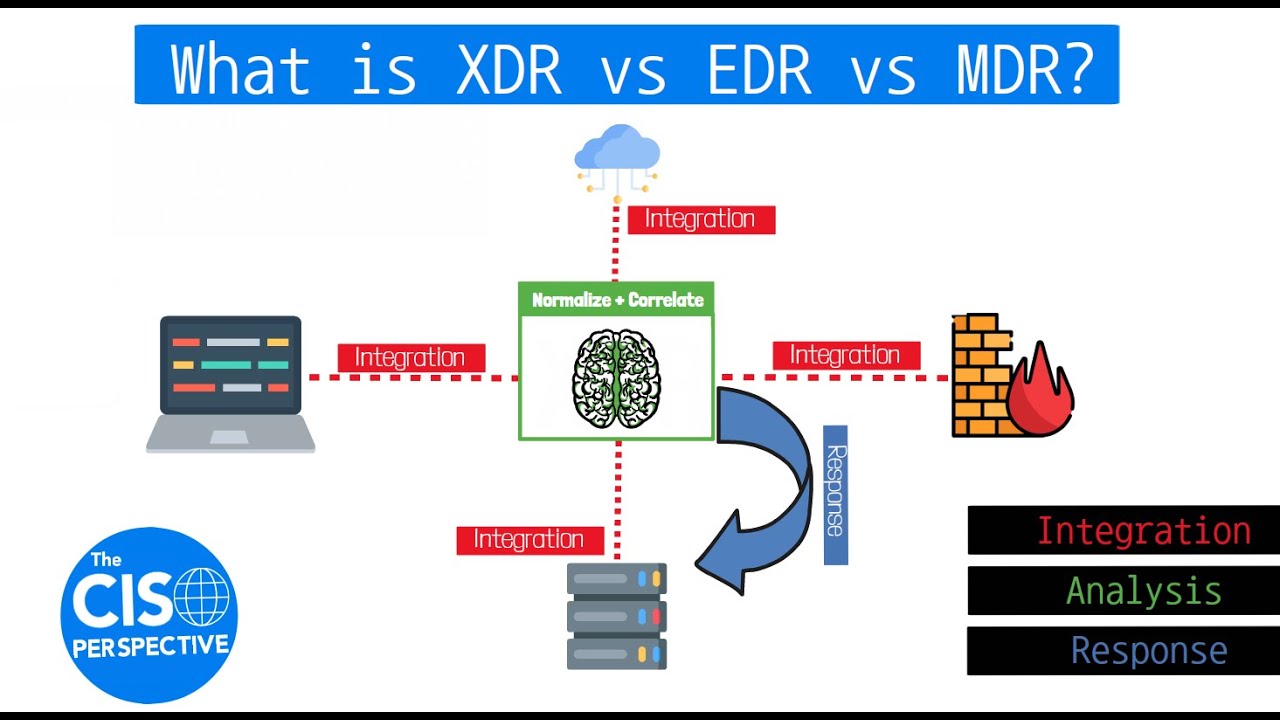
What is XDR vs EDR vs MDR? Breaking down Extended Detection and Response
Microsoft Defender for Endpoint Overview
FortiEDR - Advanced Endpoint Protection with Automated Detection and Response | Endpoint Security

Uncovering Cyber Threats: EDR vs SIEM Comparison #cybersecurity #cyber #risk #threats #detective
5.0 / 5 (0 votes)
