S3 Is A Security Nightmare (Common Exploit Showcase)
Summary
TLDRThe video script discusses common security flaws in Amazon S3 configurations, highlighting how pre-signed URLs can be misused for cross-site scripting attacks. It showcases real-world examples of vulnerabilities discovered by community member Eva, emphasizing the importance of proper authentication and file handling. The script also promotes 'UploadThing', a tool designed to simplify secure file uploads, and advises on best practices to avoid such security issues.
Takeaways
- 🔒 S3 (Amazon Simple Storage Service) security issues are common due to misconfigurations that can lead to serious vulnerabilities.
- 👀 A blog post highlighted by the speaker emphasizes the widespread problem of S3 mismanagement and the potential for exploitation.
- 📈 The speaker mentions a previous video about a massive data breach involving Firebase, which underscores the severity of such security issues.
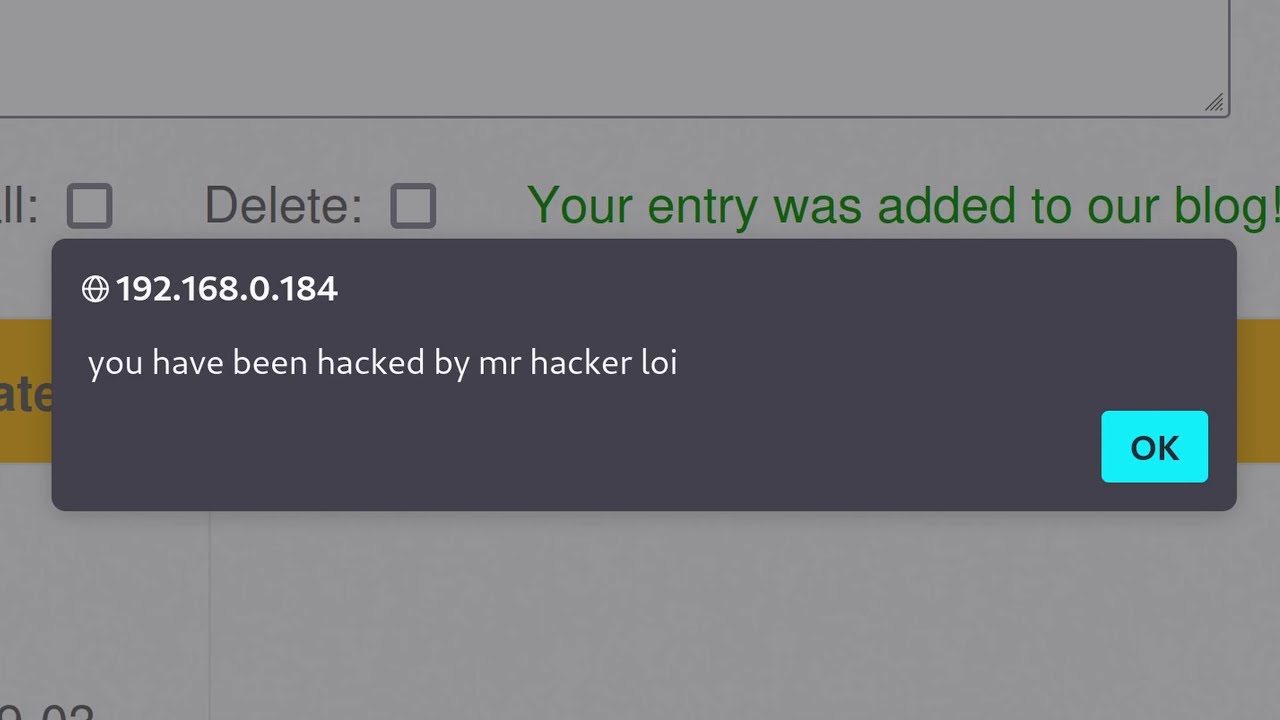
- 🛑 Pre-signed URLs in S3 can be abused if not properly secured, leading to cross-site scripting (XSS) and unauthorized file uploads.
- 🔑 Authentication checks are crucial at every step of the file upload process to prevent unauthorized access and uploads.
- 📦 The process of uploading files directly to S3 can bypass the server, which can reduce costs and improve latency but also introduces risks.
- 🚫 Allowing users to control the file path or key in S3 uploads can lead to overwriting other users' files and should be avoided.
- 🤖 Automated tools and services like UploadThing are designed to simplify secure file uploads and reduce the risk of misconfiguration.
- 🛠️ The importance of setting proper authentication and authorization for cookies and ensuring that file upload endpoints are secure against XSS.
- 💡 The script discusses specific examples of vulnerabilities found in services like Tally and P, where improper S3 configurations were exploited.
- 🔄 The video script serves as a cautionary tale, urging developers and companies to properly secure their S3 implementations to prevent data breaches and service abuse.
Q & A
What is the primary focus of the video script about S3?
-The video script focuses on the security issues with Amazon S3, discussing common configuration mistakes that can lead to security flaws, and the potential consequences of not setting up S3 correctly.
Why did the speaker decide to make a video about S3 security issues?
-The speaker decided to make a video about S3 security issues after finding a blog post that immediately caught their attention and added to their to-do list for video content.
What is the significance of the pre-signed post URL in S3 uploads?
-A pre-signed post URL is significant because it allows a user to upload a file directly to S3 within a specific time frame and with specific permissions, bypassing the need to send the file through a server, which can reduce costs and improve latency.
What are the potential security risks of allowing users to upload files directly to S3 without proper checks?
-The potential security risks include cross-site scripting (XSS) attacks, where malicious HTML or JavaScript files can be uploaded, and the possibility of overriding other users' files if the server does not check for file existence.
How can a poorly configured S3 bucket lead to account takeovers?
-A poorly configured S3 bucket can lead to account takeovers if HTML files are uploaded to a domain where cookies are not properly set, allowing an attacker to access and exploit the cookies for unauthorized access.
What is the role of authentication in the process of uploading files to S3?
-Authentication is crucial to ensure that the user uploading a file is the right user and has the necessary permissions to perform the upload, preventing unauthorized access and potential security breaches.
Why is it important to manage file uploads on your own server instead of allowing direct uploads to S3?
-Managing file uploads on your own server allows you to perform authentication checks and ensure that the files being uploaded are legitimate and do not pose a security risk, which is not possible with direct uploads to S3.
What is the purpose of using a service like UploadThing for S3 uploads?
-UploadThing is designed to simplify the process of securely uploading files to S3, enforcing authentication and proper file handling, making it difficult to set up incorrectly and reducing the risk of security vulnerabilities.
What are some best practices to avoid when securing S3 uploads?
-Best practices to avoid include allowing users to control the file path and key, not setting cookies properly, and not authenticating users on your own server before allowing file uploads.
How can third-party libraries contribute to S3 security issues?
-Third-party libraries can contribute to S3 security issues if they are not configured correctly or if they lack proper documentation, leading to common pitfalls and misconfigurations that can be exploited.
What alternatives are available for simplifying S3 uploads and management?
-Alternatives for simplifying S3 uploads and management include services like Backblaze B2, Filestack, and UploadThing, which offer APIs and tools to securely and efficiently manage file uploads to S3.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Module 5.5 Lab Cross Site Scripting

Every Hacking Technique Explained As FAST As Possible!

How The Self-Retweeting Tweet Worked: Cross-Site Scripting (XSS) and Twitter

Dalfox XSS Automation Scanner for Bug Bounty | Security Awareness
Cross Site Scripting (XSS) tutorial for Beginners

XSS - Cross Site Scripting Explained
5.0 / 5 (0 votes)