Dalfox XSS Automation Scanner for Bug Bounty | Security Awareness
Summary
TLDRThis video guide focuses on using a tool called 'Dafox' for scanning and exploiting vulnerabilities on websites. The presenter walks viewers through the installation and configuration of Dafox, along with another tool called 'ParamSpider' to identify and inject potential security flaws like SQL injections and cross-site scripting (XSS). The video includes a step-by-step tutorial on scanning single and multiple URLs, analyzing parameters, and validating the results. The goal is to educate viewers on ethical hacking practices, helping them understand and mitigate potential security threats.
Takeaways
- 📽️ The video is a tutorial presented by Metaforce, focusing on web security testing tools.
- 🛠️ The main tool discussed is 'DavoSet,' an open-source tool used for scanning and identifying vulnerabilities in web applications.
- 🔍 The presenter demonstrates how to install DavoSet, emphasizing the need to have Go programming language installed first.
- 💡 The tutorial explains how to use DavoSet to scan for vulnerabilities like Cross-Site Scripting (XSS) and SQL injection.
- 🔗 The presenter shows how to scan a single URL and multiple URLs to detect vulnerabilities using DavoSet.
- 🧪 The video highlights the use of another tool called 'ParamSpider' to identify and analyze parameters in a web domain.
- 💻 The tutorial includes practical examples of scanning URLs for XSS vulnerabilities, showcasing both successful and unsuccessful attempts.
- 📂 The results of the scans are saved in specific output files for later review and analysis.
- 🌐 The presenter also demonstrates how to validate and confirm the findings manually to ensure accuracy.
- 🔒 The video encourages viewers to practice ethical hacking and emphasizes the importance of verifying tool-generated results.
Q & A
What is the main focus of the video discussed in the transcript?
-The video focuses on demonstrating a tool for scanning vulnerabilities, particularly XSS (Cross-Site Scripting) vulnerabilities, in websites.
Which tools are primarily discussed in the video?
-The video discusses two main tools: Gavox, which is used for scanning and detecting XSS vulnerabilities, and Paralon Spider, which helps find parameters within a domain or link for further testing.
What is Gavox, and how is it used?
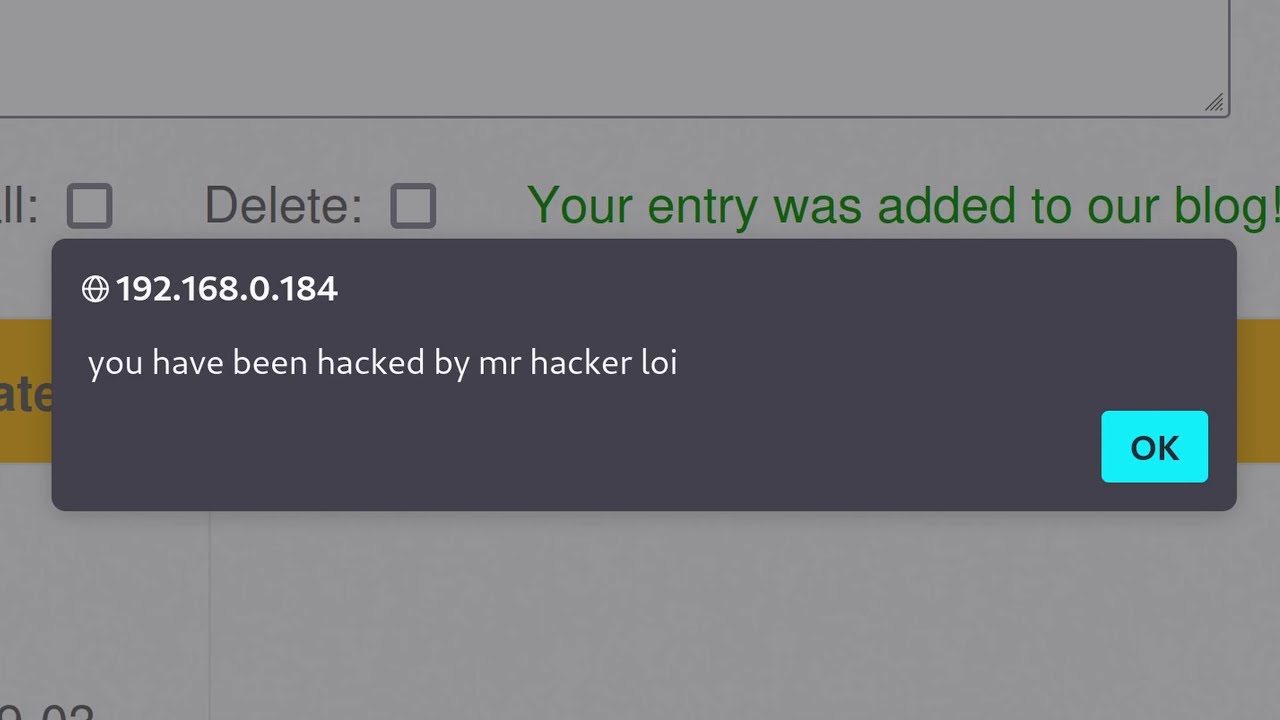
-Gavox is a powerful open-source tool used for analyzing parameters within a URL to check if they are vulnerable to XSS attacks. If a vulnerability is found, Gavox can identify it and suggest payloads to exploit it.
How does Paralon Spider complement Gavox in the scanning process?
-Paralon Spider is used to search for parameters in a given domain or link, which can then be tested using Gavox to identify potential vulnerabilities.
What is the purpose of the video creator using the website 'test.php' on 'hugwap.com'?
-The website 'test.php' on 'hugwap.com' is used as a practice platform for learning and testing XSS vulnerabilities. The video creator uses it to demonstrate how to scan and identify such vulnerabilities.
What is the significance of installing Go programming language as mentioned in the video?
-The Go programming language is required to run Gavox, as Gavox is developed using Go. The video explains how to install Go to ensure Gavox can be used effectively.
What does the video creator demonstrate with the parameter 'Academy' in the test?
-The video creator demonstrates how to scan a single target URL using the 'Academy' parameter to check for XSS vulnerabilities. The scanning results show whether the parameter is vulnerable.
What does the video creator mean by 'single target' and 'multiple targets' in the context of the scan?
-A 'single target' scan refers to testing one URL for vulnerabilities, while 'multiple targets' scan involves testing several URLs simultaneously to identify vulnerabilities across a range of links.
What does the video creator suggest about the results of the vulnerability scan?
-The video creator suggests that the results of the vulnerability scan should be validated, as there can be false positives. It's important to manually verify the findings to confirm if they are genuine vulnerabilities.
What additional tool does the video creator recommend for easier URL manipulation during vulnerability testing?
-The video creator recommends using a browser extension called 'Akbar' to make it easier to encode and manipulate URLs during vulnerability testing.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video
5.0 / 5 (0 votes)