Lesson 13: How Email Works
Summary
TLDRThis lesson introduces how email systems work, explaining the journey of an email from sender to recipient. Using illustrations, it details the roles of user agents, message transfer agents (MTAs), and protocols like SMTP in transmitting emails. The video also discusses private versus web-based email systems, the structure of email addresses, and the importance of email headers, including MIME headers that allow for multimedia content. It highlights how understanding these processes can help identify security threats in emails, offering insight into how headers can be used to detect phishing attempts.
Takeaways
- 😀 Jack uses a private email system with an email application like Microsoft Outlook or Thunderbird, while Jill uses a web-based email system like Gmail or Yahoo Mail.
- 😀 Private email systems like Jack's are often used by businesses and require dedicated email applications to access, whereas web-based email systems like Jill's are accessible from any computer with an internet connection.
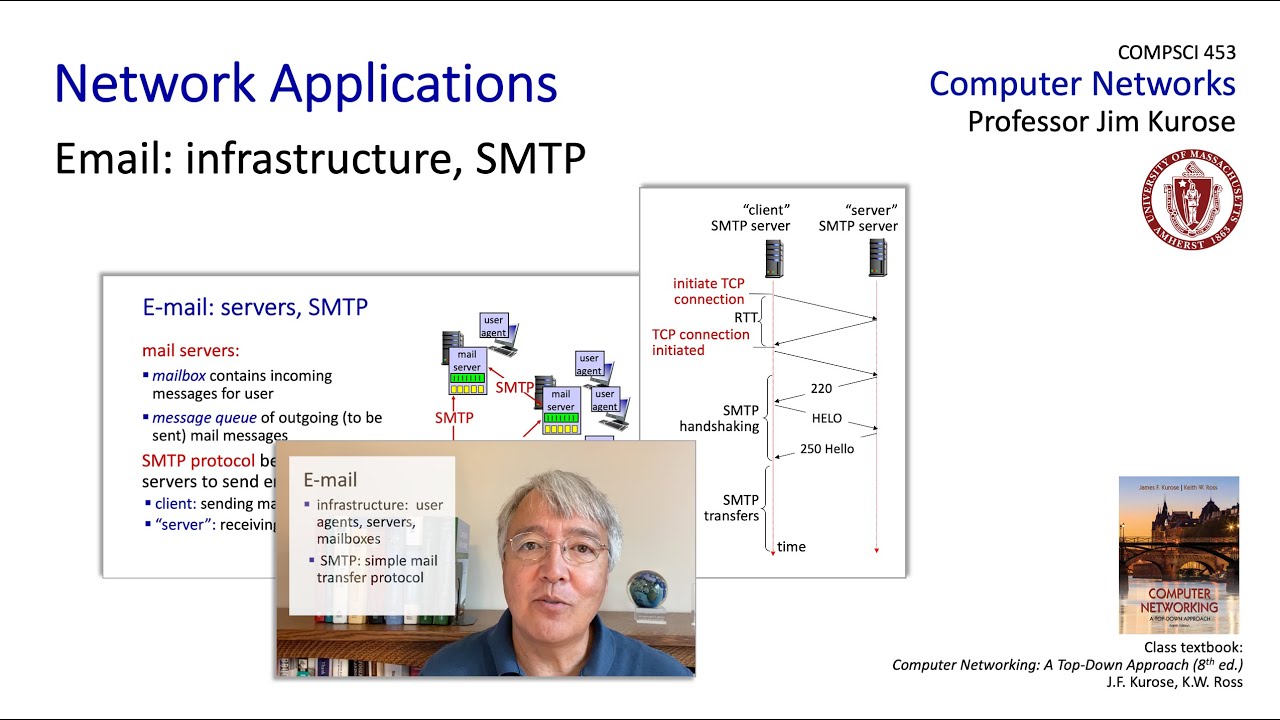
- 😀 Email messages travel through a series of servers, known as Message Transfer Agents (MTAs), to get from the sender to the recipient's email system.
- 😀 SMTP (Simple Mail Transfer Protocol) is the language or protocol used by MTAs to communicate with each other across the internet during email transmission.
- 😀 The process of sending an email from Jack to Jill involves his user agent sending the message to MTAs, which relay the message to Jill's email system for retrieval.
- 😀 Jill can only send emails back to Jack through the reverse process, with the message traveling through MTAs until it reaches Jack's system.
- 😀 Email addresses are structured with a user name and a domain name, where everything after the '@' symbol points to a specific MTA on the internet.
- 😀 MIME (Multipurpose Internet Mail Extensions) headers allow email systems to support content beyond plain text, such as images, special fonts, and file attachments.
- 😀 Email headers track the journey of an email across MTAs and help to verify the authenticity of the sender, as cyber criminals may attempt to fake return addresses but cannot easily manipulate MTA headers.
- 😀 In case of suspicious emails, viewing the full email header can help determine the authenticity of the message by showing where it originated from, even if the sender’s address is fake.
Q & A
What is the role of the user agent in the email system?
-The user agent is the application or software used by the sender to compose, send, and manage emails. For example, Microsoft Outlook or Mozilla Thunderbird are user agents in private email systems.
What is a private email system and how does it differ from web-based systems?
-A private email system is one that requires a user agent installed on a local computer to send and receive emails, often used by businesses or individuals who prefer more control. Web-based systems, like Gmail or Yahoo Mail, allow access via a browser and store emails on remote servers.
How does an email message travel from Jack to Jill in the first illustration?
-Jack writes an email using his user agent, which sends it through a series of message transfer agents (MTAs) across the internet until it reaches Jill’s email server. From there, Jill’s web-based user agent retrieves the email.
What does SMTP stand for and what is its role in email communication?
-SMTP stands for Simple Mail Transfer Protocol. It is the protocol used by message transfer agents (MTAs) to communicate and transfer email messages between servers across the internet.
What is the function of message transfer agents (MTAs) in the email system?
-MTAs are responsible for receiving, storing, and forwarding email messages to their destination. They act as the intermediaries that help emails travel across the internet from sender to recipient.
What is the significance of the MIME header in an email?
-MIME (Multipurpose Internet Mail Extensions) allows emails to include not just plain text but also multimedia elements such as images, special fonts, and attachments. The MIME header indicates the types of content an email contains.
How does an email address function in terms of routing the message?
-An email address specifies two key pieces of information: the user and the mail server. The part after the '@' symbol indicates the message transfer agent's domain (e.g., 'dg.j.net'), which helps route the email to the correct server.
What is the importance of email headers in tracking the origins of a message?
-Email headers track the journey of the email across different message transfer agents. These headers are important for verifying the legitimacy of an email, especially in identifying potential phishing attempts by checking where the email came from.
How can a user check the full email header and why might they do this?
-To view the full header, a user can open an email in their email client and look for an option like 'view full header.' This is useful for detecting suspicious emails or verifying their authenticity by checking the route the email took.
What are some security risks associated with email and how can they be minimized?
-Common security risks in email include phishing and malware. Users can minimize risks by being cautious with email attachments and links, using strong passwords, and using email services that offer security features like encryption.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Animasi OSI LAYER (Mekanisme Perjalanan Data Pada OSI Model)

SMTP Server Configuration & Mail Transfer in Bangla | CSE 312 Networking Lab Bangla Tutorial
07 01 b Forensik email Properties

Me dê 24 minutos que eu pouparei 5 anos da sua vida

What Is A Verified Mark Certificate (VMC)? - TheEmailToolbox.com
2.3 Email
5.0 / 5 (0 votes)