Bitcoin Will NEVER Be Hacked - Here's Why!
Summary
TLDRIn this enlightening video, Eric Yakes discusses the discrete logarithm problem, a key component of modern cryptography that underpins Bitcoin's security. He explains how finite field math and elliptic curves create a robust framework for secure transactions, making it nearly impossible to reverse-engineer private keys from public ones. The video also delves into the mining process, illustrating how miners are incentivized through economic costs and energy use, ensuring the integrity of the blockchain. Ultimately, it highlights the intricate balance of mathematics and game theory that secures Bitcoin and shapes its revolutionary potential.
Takeaways
- 🔒 The discrete logarithm problem is fundamental to modern cryptography, providing security for public key systems like Bitcoin.
- 🧮 Bitcoin relies on finite field math, which differs from conventional arithmetic and is similar to the behavior of a clock.
- 📈 Elliptic curves, used in Bitcoin, enable secure key generation and allow for operations like point addition.
- 🔑 In Bitcoin wallets, the private key is a randomly generated integer multiplied by a generator point to produce the public key.
- 🔍 The security of Bitcoin's public key system is based on the difficulty of deriving the private key from the public key.
- ⚡ The mining process involves solving a proof-of-work computational puzzle to add blocks to the blockchain.
- 💻 Miners generate hashes from block headers, competing to find a valid hash that meets the network's difficulty target.
- 🌍 The economic cost of mining ensures that miners are incentivized to maintain network integrity and security.
- 🌀 Bitcoin's difficulty target adjusts based on the overall hash rate, ensuring blocks are mined at a consistent pace.
- ⚠️ Concerns about quantum computing potentially breaking current cryptographic methods highlight the importance of ongoing security advancements.
Q & A
What is the discrete log problem and why is it important in cryptography?
-The discrete log problem is a mathematical problem that remains unsolved and forms the foundation of public key cryptography. It allows secure communication over insecure channels by making it nearly impossible to reverse engineer the multiplication of a point and integer to retrieve the integer.
How does finite field math differ from normal arithmetic?
-Finite field math operates similarly to a clock, where calculations wrap around a maximum value. For example, in a finite field with a maximum of 12, 4 * 4 equals 4 instead of 16 because the result wraps around after reaching the maximum.
What role do elliptic curves play in Bitcoin's security?
-Elliptic curves allow for point addition and multiplication, enabling the generation of public keys from private keys. They provide a mathematical framework that enhances the security and efficiency of cryptographic processes in Bitcoin.
Why is the choice of a large prime number significant in cryptography?
-Choosing a large prime number in cryptographic systems increases security by making it exceedingly difficult for computers to guess the original number used in the calculations. The larger the prime number, the more secure the cryptographic process.
What is the mining process in Bitcoin, and how does it ensure network security?
-The mining process involves miners solving a computational puzzle known as proof of work. This requires generating a hash of the block header that falls below a certain difficulty target. It ensures network security by making it costly and energy-intensive to add new blocks, thus deterring malicious actions.
How does the proof of work algorithm impact the behavior of miners?
-The proof of work algorithm incentivizes miners to find cheaper electricity and optimize their operations. Since miners compete to solve the computational puzzle, their behavior is influenced by the economic cost of generating hashes, which shapes the overall efficiency of the network.
What happens when a miner successfully finds a valid hash?
-When a miner finds a hash that meets the difficulty target, they can broadcast the new block to the network. Other nodes then verify the block and its transactions before accepting it, rewarding the miner with newly minted bitcoins and transaction fees.
How does Bitcoin’s use of energy relate to its security?
-Bitcoin’s significant energy consumption is a fundamental aspect of its security. The high energy cost associated with mining creates a barrier against attacks, ensuring that adding new information to the blockchain is a costly and resource-intensive process.
What are the implications of quantum computing for Bitcoin’s cryptographic systems?
-If quantum computing advances sufficiently, it could potentially solve the discrete log problem, threatening the security of current cryptographic systems, including Bitcoin. However, the likelihood of this happening and the impact it would have on Bitcoin and other systems remain uncertain.
How can understanding the mathematics behind Bitcoin improve confidence in its security?
-By grasping the mathematical principles like the discrete log problem and finite field math, individuals can better appreciate the robustness of Bitcoin’s security framework, which helps dispel misconceptions about its vulnerability and reassures users about its reliability.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

#54 S/MIME - Secure MIME protocol - Functions, Services |CNS|
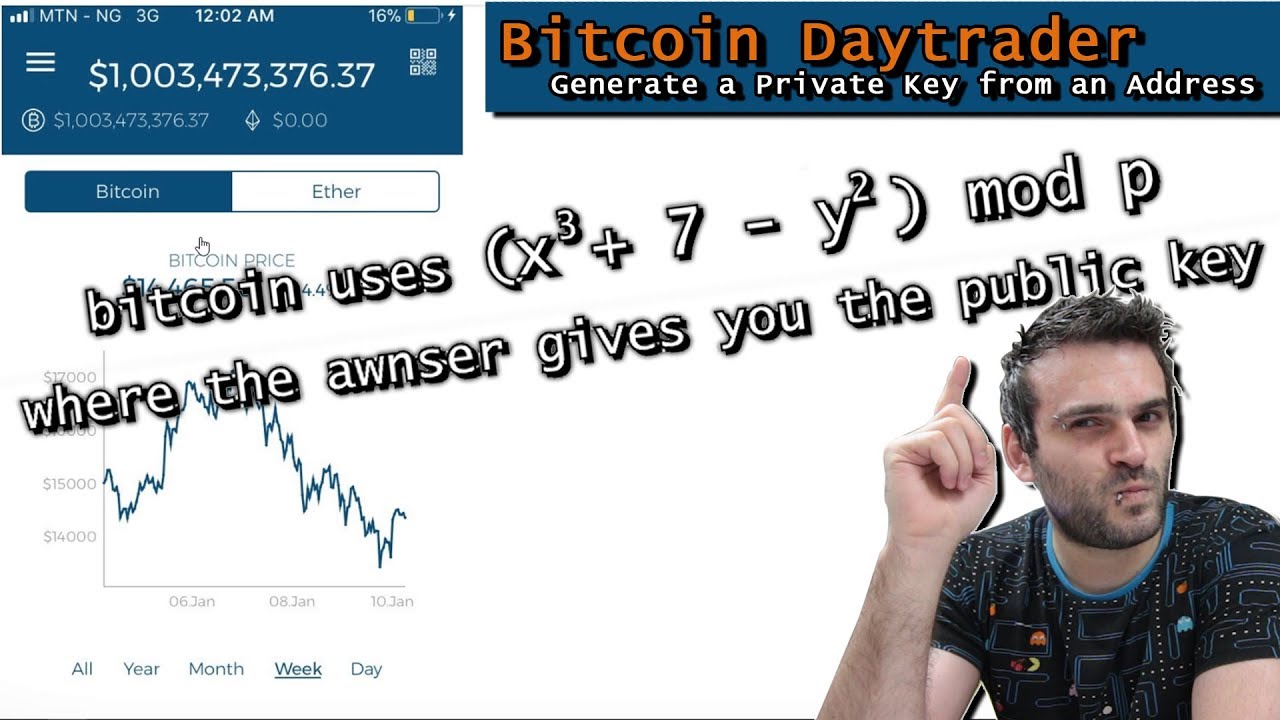
How to Generate a Private Key from a Bitcoin watch only address

3 FIPS Cryptography Compliance Properties That You Can't Check Statically

APA ITU CRYPTOGRAPHY?
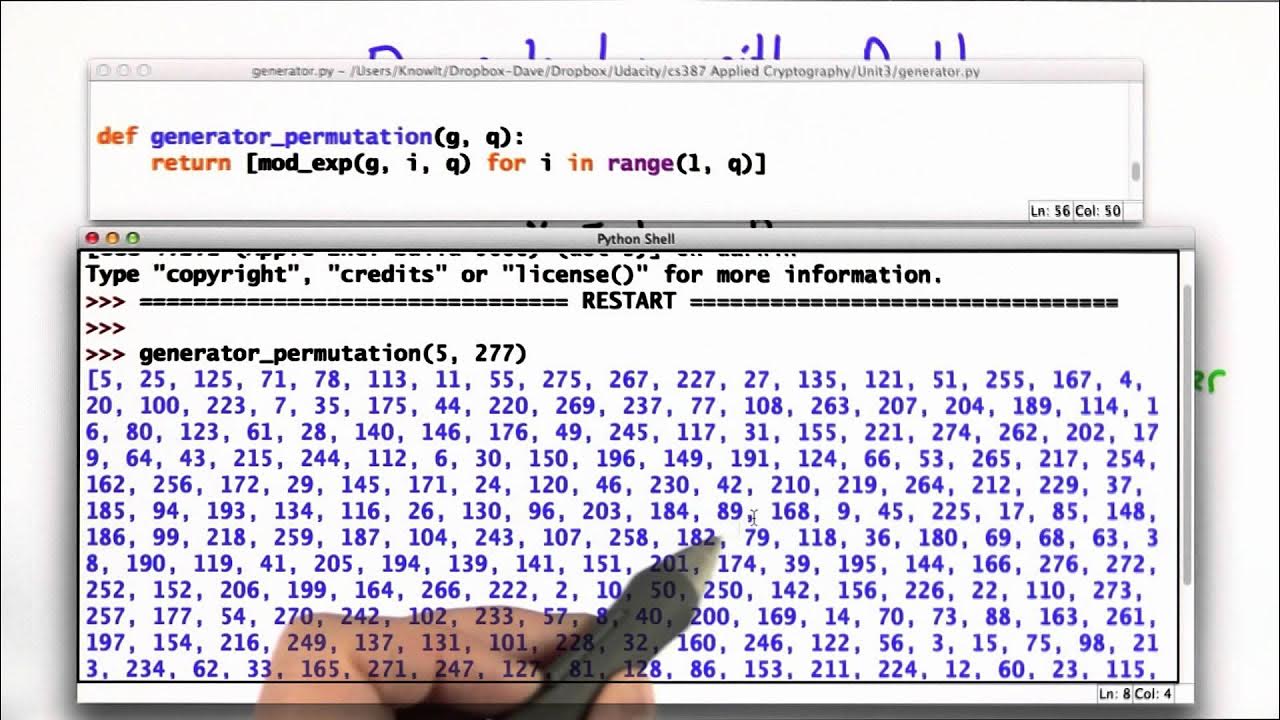
Discrete Log Problem - Applied Cryptography

The discrete logarithm problem | Journey into cryptography | Computer Science | Khan Academy
5.0 / 5 (0 votes)