91. OCR A Level (H446) SLR14 - 1.4 Data structures part 5 - Hash tables
Summary
TLDRIn this final video of the series on data structures, we delve into hash tables, which allow for efficient data retrieval without item comparisons. By using a hash function, items are assigned positions in the table, minimizing access time. However, collisions can occur when multiple items hash to the same index, necessitating strategies like open addressing and chaining to resolve them. The video emphasizes the importance of understanding basic operations—adding, deleting, and retrieving values—while also promoting a companion book that covers essential algorithms and data structures for aspiring computer scientists.
Takeaways
- 😀 A hash table allows for immediate item retrieval from a dataset without comparisons.
- 🔑 Hash tables implement dictionary-like structures in programming languages.
- ⚙️ A hashing function calculates the position of an item based on its hash value.
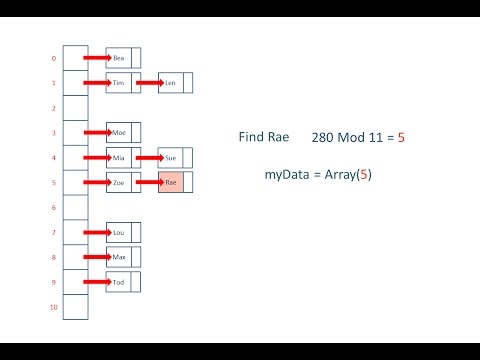
- 🧮 An example hashing function adds the ASCII values of string characters and uses modulus to determine the position.
- ⚠️ Collisions occur when different items yield the same hash value, necessitating resolution strategies.
- 🔍 Open addressing is a method where the next available space is checked to resolve collisions.
- 📏 Linear probing searches sequentially from the initial hash value to find an empty position.
- 🚫 Clustering can occur with linear probing, which affects the efficiency of the hash table.
- 📊 Alternative collision handling methods include chaining and overflow tables.
- 📖 The book 'Essential Algorithms for A-Level Computer Science' provides comprehensive coverage of data structures and algorithms.
Q & A
What is the primary purpose of a hash table?
-The primary purpose of a hash table is to quickly find an item in a dataset without needing to compare every other item.
How is a hash value calculated in a hash table?
-A hash value is calculated by applying a hashing function to an item, which often involves summing the ASCII values of its characters and taking the modulus of the hash table size.
What is a collision in the context of hash tables?
-A collision occurs when two different items hash to the same position in a hash table, meaning they cannot occupy the same space.
What is the effect of table size on collision frequency?
-The size of the hash table can significantly affect collision frequency; a larger table generally results in fewer collisions, while a smaller table may lead to more collisions.
What is open addressing?
-Open addressing is a collision resolution strategy where the algorithm checks the next available position in the hash table until it finds an empty space.
What is linear probing?
-Linear probing is a specific type of open addressing where the algorithm searches for the next available position sequentially after a collision occurs.
What are the potential downsides of linear probing?
-Linear probing can lead to clustering, where several consecutive positions become filled, hindering efficiency and leading to longer search times.
What is chaining in hash tables?
-Chaining is a method of collision resolution where multiple items can occupy the same position by storing them in a list or array at that position.
What are the three basic operations that can be performed on a hash table?
-The three basic operations are adding a value, deleting a value, and retrieving a value.
What resources does the book 'Essential Algorithms for A-Level Computer Science' provide?
-The book covers essential data structures and algorithms, offering structured English explanations, diagrams, pseudocode, and fully coded algorithms in Python and VB.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)