Network Enumeration The Ultimate Guide
Summary
TLDRNetwork enumeration is a crucial cybersecurity process that involves gathering information about devices, IP addresses, and user accounts within a network. This script explains the steps involved in the process, starting with scanning, port checking, and network mapping. It also discusses operating system detection and vulnerability assessments. Ethical hackers use these techniques to uncover potential weaknesses and secure networks, but the same tools can be misused by malicious actors. Ultimately, network enumeration helps strengthen defenses and provides critical insights into a network’s structure and security vulnerabilities.
Takeaways
- 🔍 Network enumeration is like a digital explorer charting the unknown terrains of a network, gathering crucial information.
- 🌐 It's a method that exposes a network's security weaknesses by gathering data about hosts, IP addresses, shared resources, and user accounts.
- 🏙️ Network enumeration is compared to a detailed tour of a digital city, allowing for a deeper understanding of a network's structure and vulnerabilities.
- 🕵️♂️ The process is essential in ethical hacking, similar to a detective gathering clues at a crime scene to solve a case.
- ⚠️ In ethical hands, network enumeration helps to strengthen defenses, but in malicious hands, it can exploit vulnerabilities.
- 📊 The process involves several key steps: scanning, port checking, network mapping, operating system detection, and vulnerability assessment.
- 🛡️ Scanning identifies devices connected to the network, while port checking reveals which services are running and which ports are open or closed.
- 🗺️ Network mapping provides a bird's-eye view of the network's architecture and how devices are interconnected.
- 💻 Operating system detection identifies what OS each device runs, helping to pinpoint potential vulnerabilities.
- 🚨 Vulnerability assessment tests for weaknesses, such as outdated software or weak passwords, aiming to identify risks and improve security.
Q & A
What is network enumeration?
-Network enumeration is the process of gathering detailed information about a network, including hosts, IP addresses, shared resources, and user accounts. It is a method used to map out a network's structure and identify potential vulnerabilities.
Why is network enumeration compared to charting a digital landscape?
-Network enumeration is compared to charting a digital landscape because it involves systematically exploring and mapping out a network's architecture, just like a city tour guide would gather and organize information about buildings and streets in a city.
What are the main steps involved in network enumeration?
-The main steps in network enumeration include scanning, port checking, network mapping, operating system detection, and vulnerability assessment. These steps help identify devices, services, and potential security risks within a network.
What is the purpose of scanning in network enumeration?
-Scanning is the initial stage where devices connected to the network are identified. The goal is to gain a comprehensive view of the network and potential targets, much like a reconnaissance mission.
How does port checking contribute to network enumeration?
-Port checking involves identifying which ports on a device are open or closed. Open ports indicate running services, which can reveal weak points in the network. This step is crucial for identifying potential entry points for attackers.
What is network mapping, and why is it important?
-Network mapping creates a schematic representation of how devices are connected within a network. It provides a bird's-eye view of the network's structure and helps in understanding how data flows, which is essential for identifying vulnerabilities.
Why is operating system detection important in network enumeration?
-Operating system detection helps identify the type of operating system running on each device. This information is crucial for understanding potential software vulnerabilities and structuring targeted security measures.
What happens during vulnerability assessment in network enumeration?
-During vulnerability assessment, the network is probed for potential security risks, such as outdated software or weak passwords. The goal is to identify vulnerabilities so they can be addressed before they are exploited by malicious attackers.
Why is network enumeration important in ethical hacking?
-Network enumeration is essential in ethical hacking because it helps identify vulnerabilities that need to be addressed. Without it, ethical hackers would not be able to fully understand the network’s weaknesses, which could leave systems exposed to attacks.
How can network enumeration be misused, and why should it be used responsibly?
-Network enumeration can be misused by malicious hackers to exploit vulnerabilities and compromise a network’s security. In the wrong hands, it can lead to privacy breaches and network damage. Therefore, it should be used responsibly, ensuring its use is limited to ethical purposes.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

Ano ba ang Static at Dynamic IP Adress

CCNA 200-301 en Français - Leçon 21 : LAB - Configuration de Telnet

DHCP Explained | Step by Step

Everything Switches do - Part 1 - Networking Fundamentals - Lesson 4
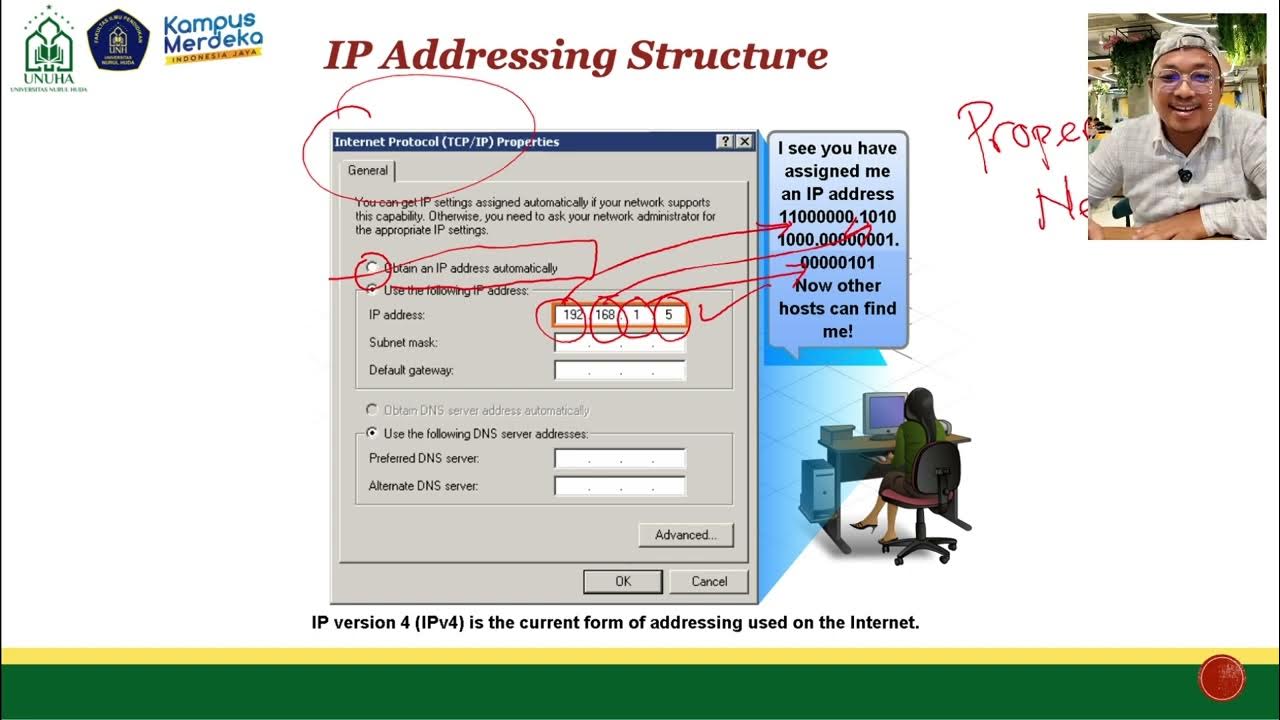
Pertemuan 5 - IP Address
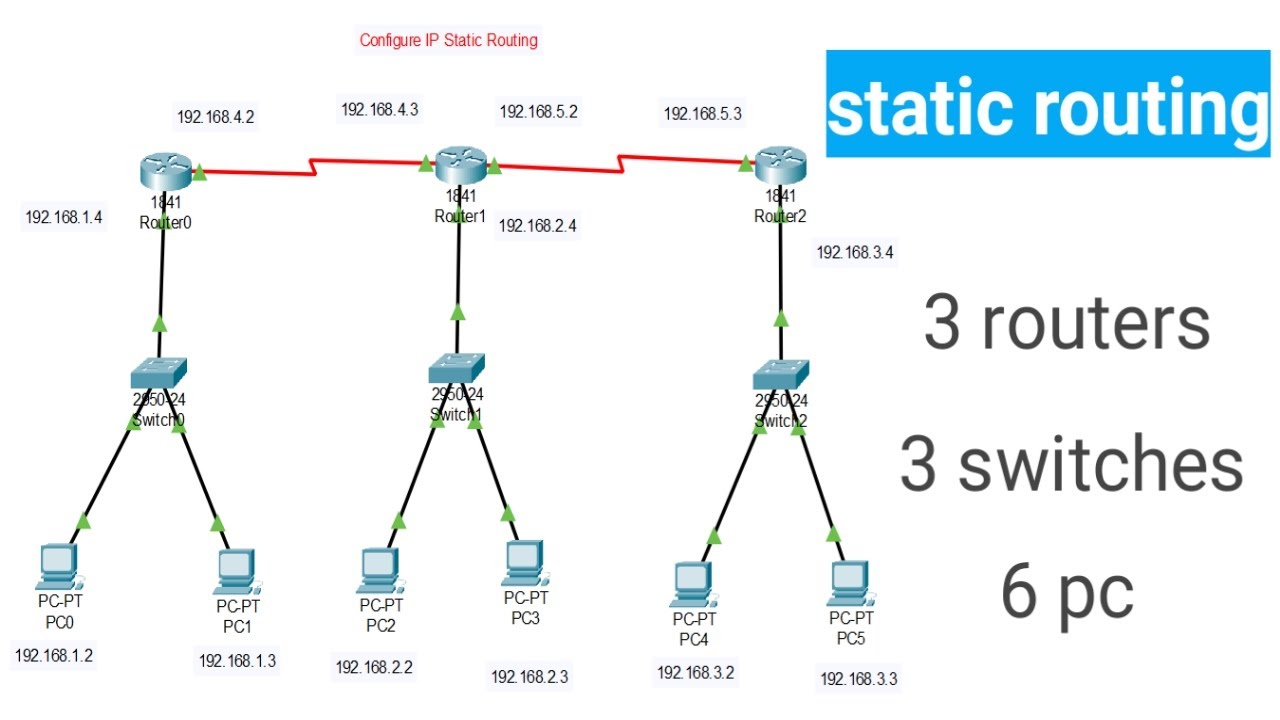
Configure IP static routing in Hindi | Static Routing using 3 routers, 3 Switches, 6 Pc
5.0 / 5 (0 votes)