Control Frameworks: COSO & COBIT | Fundamentals of Internal Auditing | Part 5 of 44
Summary
TLDRIn this episode, Henan Murdoch and expert Kathleen Crawford dive into the COSO and COBIT frameworks, explaining their significance in internal auditing and information security. They discuss the five components of the COSO framework: control environment, risk assessment, control activities, information and communication, and monitoring. Kathleen emphasizes the importance of tone at the top, accountability, and proactive risk assessment, especially concerning fraud. The conversation then shifts to COBIT, which focuses on managing IT security and risks, highlighting shared responsibility across the organization. Overall, the session offers valuable insights into maintaining strong governance and controls in modern organizations.
Takeaways
- 😀 COSO (Committee of Sponsoring Organizations) is a framework created by various organizations, including the IIA and the AICPA, to establish effective internal controls and mitigate organizational risks.
- 😀 COSO's original model from 1992 focused on creating a strong control environment to prevent financial breakdowns, with the updated version (2013) emphasizing the importance of principles and proactive risk management.
- 😀 The COSO framework consists of five components: control environment, risk assessment, control activities, information and communication, and monitoring activities.
- 😀 The 'tone at the top' is essential in COSO, as leadership sets the organizational tone and culture, influencing all levels of operations and internal audit processes.
- 😀 The control environment is the foundation of the framework and includes principles like integrity, accountability, and clear authority, which are vital for an effective internal control system.
- 😀 Risk assessment within COSO requires identifying risks and setting objectives to prevent potential issues that could disrupt an organization's goals, including assessing the risk of fraud proactively.
- 😀 Control activities are actions taken to manage identified risks, and they must be both preventive and detective, addressing specific organizational risks through well-designed controls.
- 😀 Information and communication in COSO ensure that relevant, accurate, and timely information flows across all levels of the organization, promoting transparency and alignment.
- 😀 Monitoring activities in COSO focus on continuous evaluation of internal controls to ensure they remain effective and adapt to changing risks over time, with shared responsibility across the organization.
- 😀 COBIT is a framework focused on IT governance and information security, emphasizing the importance of proper IT management and security at all levels, not just within the IT department.
- 😀 COBIT, like COSO, stresses shared responsibility across the organization in securing and managing information technology, ensuring everyone plays a role in maintaining its integrity and security.
Q & A
What is the COSO framework, and who developed it?
-The COSO framework is a model developed by a group of organizations known as the Committee of Sponsoring Organizations (COSO). It was created to guide organizations in implementing effective internal controls to mitigate risks. The group included the Institute of Internal Auditors (IIA), the AICPA, and other organizations.
What is the purpose of the COSO framework?
-The COSO framework provides guidelines for organizations to implement internal controls that safeguard against risks and ensure efficient operations. Its primary purpose is to help organizations maintain stability and protect themselves from various risks that could interfere with their operations.
What was the original reason for developing the COSO framework in the 1990s?
-The COSO framework was developed after a series of massive financial breakdowns in the 1980s. The committee, led by Treadway, aimed to investigate these breakdowns and create a framework to prevent similar failures by establishing better internal controls and practices.
How does the structure of the COSO framework differ from the original version?
-The updated COSO framework, which was restructured in 2013, added a focus on key principles for each component. These principles were introduced to address the concerns that arose from organizations overcompensating for risks in their Sarbanes-Oxley compliance, potentially neglecting the foundational principles of the framework.
What are the five components of the COSO framework?
-The five components of the COSO framework are: 1) Control Environment, 2) Risk Assessment, 3) Control Activities, 4) Information and Communication, and 5) Monitoring Activities.
What is the 'tone at the top' in the context of the COSO framework?
-The 'tone at the top' refers to the leadership and ethical values set by senior management and the board of directors. It is crucial because it influences the organization's culture, guiding behavior and decision-making across all levels of the organization.
How does the COSO framework address the issue of risk assessment?
-The COSO framework emphasizes identifying and assessing risks at both a broad and specific level. It includes setting objectives, analyzing risks, assessing fraud risk, and being alert to significant changes that could impact the achievement of organizational objectives.
What role does monitoring play in the COSO framework?
-Monitoring activities in the COSO framework involve ongoing and regular evaluations to assess the effectiveness of the internal control system. It ensures that adjustments are made where necessary and that the internal controls continue to function as intended.
What is COBIT, and how does it relate to the COSO framework?
-COBIT is a framework primarily focused on IT governance and information security. It complements the COSO framework by ensuring the integrity and security of information and systems within an organization, aligning with the same overall goals of risk management and control.
How does the COSO framework's concept of control activities apply to an organization?
-Control activities in COSO involve selecting and developing effective controls to mitigate identified risks. This includes preventive and detective controls and ensures that policies and procedures are in place, communicated, and followed to reduce the likelihood of control failures.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード関連動画をさらに表示

Workpapers: IIA Standards | Fundamentals of Internal Auditing | Part 32 of 44

Sistem Informasi Akuntansi_Romney_Pengendalian&Sistem Informasi Akuntansi.

Written Audit Reports Explained | Fundamentals of Internal Auditing | Part 38 of 44

Materi Mata Kuliah IT Audit 2 Mei 2025

Overview of Information System Auditing | Information System Auditing Kya Hai | Overview of Auditing
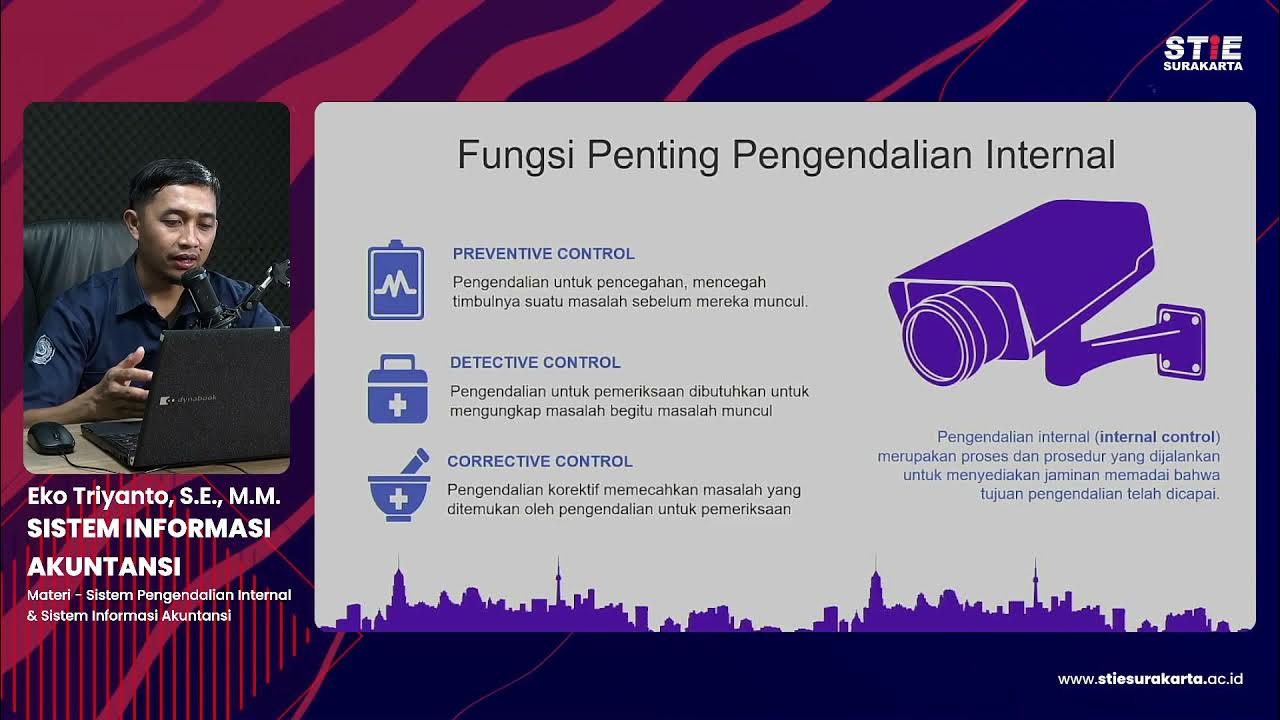
Sistem Informasi Akuntansi #8 Sistem pengendalian internal & Sistem Informasi Akuntansi-Eko Triyanto
5.0 / 5 (0 votes)
