AWS Shared Responsibility Model
Summary
TLDRThe AWS Shared Responsibility Model outlines the division of security and compliance responsibilities between AWS and its customers. AWS handles the security of the cloud, including physical infrastructure, data centers, and networking equipment. Customers are responsible for securing their use of the cloud, such as managing data, encryption, and user access. The model clearly defines responsibilities at different layers, from hardware to applications, and highlights the need for customer involvement in areas like patch management, data encryption, and network configuration. Understanding this model is crucial for exam preparation and efficient use of AWS services.
Takeaways
- 😀 AWS Shared Responsibility Model (SRM) defines the division of responsibilities between AWS and the customer for security and compliance.
- 😀 AWS is responsible for 'security of the cloud', including physical infrastructure, data centers, and networking equipment.
- 😀 Customers are responsible for 'security in the cloud', including protecting their data, encrypting it, and managing access.
- 😀 The SRM divides responsibilities into clear layers: AWS manages physical infrastructure, while customers handle data and access management.
- 😀 Customer data security, including encryption, is fully the customer's responsibility, and AWS does not manage this aspect.
- 😀 AWS manages regions, availability zones, edge locations, and physical servers, while the customer manages their EC2 instances and data.
- 😀 Customers are responsible for managing networking, traffic protection, and configuring firewalls like security groups and network ACLs.
- 😀 AWS handles the underlying software for databases like DynamoDB, but customers are responsible for managing and populating their data tables.
- 😀 Customers are responsible for operating system updates and patches on EC2 instances, while AWS manages infrastructure-level patches.
- 😀 SRM includes inherited controls (physical security managed by AWS), shared controls (e.g., patch management), and customer-specific controls (e.g., application security).
Q & A
What is the AWS Shared Responsibility Model?
-The AWS Shared Responsibility Model defines the division of security responsibilities between AWS and the customer. AWS is responsible for the security *of* the cloud (infrastructure), and customers are responsible for the security *in* the cloud (applications, data, and configurations).
What does AWS handle under the Shared Responsibility Model?
-AWS is responsible for the physical infrastructure, including data centers, servers, hardware, networking equipment, storage systems, and the software that operates these components. Additionally, AWS manages physical security and disposal of hardware.
What is the customer's responsibility in the AWS Shared Responsibility Model?
-The customer is responsible for securing their data, operating systems, applications, and networks in the cloud. This includes managing encryption, user access management, patching of EC2 instances, and maintaining network security configurations like security groups and NACLs.
What is meant by 'security of the cloud' and 'security in the cloud' in the AWS context?
-'Security of the cloud' refers to AWS's responsibility for securing the infrastructure, such as hardware, physical facilities, and the global network. 'Security in the cloud' refers to the customer's responsibility to secure their data, applications, networks, and user access within AWS.
How does AWS ensure the security of its infrastructure?
-AWS ensures infrastructure security by managing physical data centers, securing networking hardware (like routers and switches), maintaining server hardware, and overseeing software layers that run these systems. AWS also ensures the safe disposal of physical storage devices.
What is a customer's responsibility regarding data encryption in AWS?
-Customers are responsible for encrypting data both at rest (stored data) and in transit (data being transferred). AWS provides tools to facilitate encryption, but the implementation of encryption practices is the customer's responsibility.
What is the role of Identity and Access Management (IAM) in AWS, and who is responsible for it?
-IAM is a key AWS service that manages user access and permissions. Customers are fully responsible for configuring IAM policies, roles, and user permissions to ensure secure access to AWS resources.
What does 'shared controls' mean in the AWS Shared Responsibility Model?
-Shared controls refer to security responsibilities that are jointly managed by AWS and the customer. For example, AWS handles patching and securing the underlying infrastructure, while the customer is responsible for patching their EC2 instances and applications.
What is the responsibility of a customer regarding security training in AWS?
-AWS ensures that its own employees are trained on security practices, but customers are responsible for training their own staff to use AWS services securely and properly.
Can you provide examples of inherited controls in AWS?
-Inherited controls are security features that customers automatically inherit from AWS, such as physical security at data centers and environmental controls. Customers do not need to manage these elements but benefit from AWS's inherent security measures.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantVoir Plus de Vidéos Connexes

AWS re:Invent 2022 - A close look at AWS Fargate and AWS App Runner (CON406)

AWS Cloud Practitioner Exam Questions | CLF - C02 | Tutorial - 08 | Tech India |

AWS Control Tower Overview and Landing Zone Hands-On

AWS Security Audit I - IAM Root Account Configuration Review

Day-30 | THREE-TIER ARCHITECTURE IMPLEMENTATION ON AWS | #aws #abhishekveeramalla
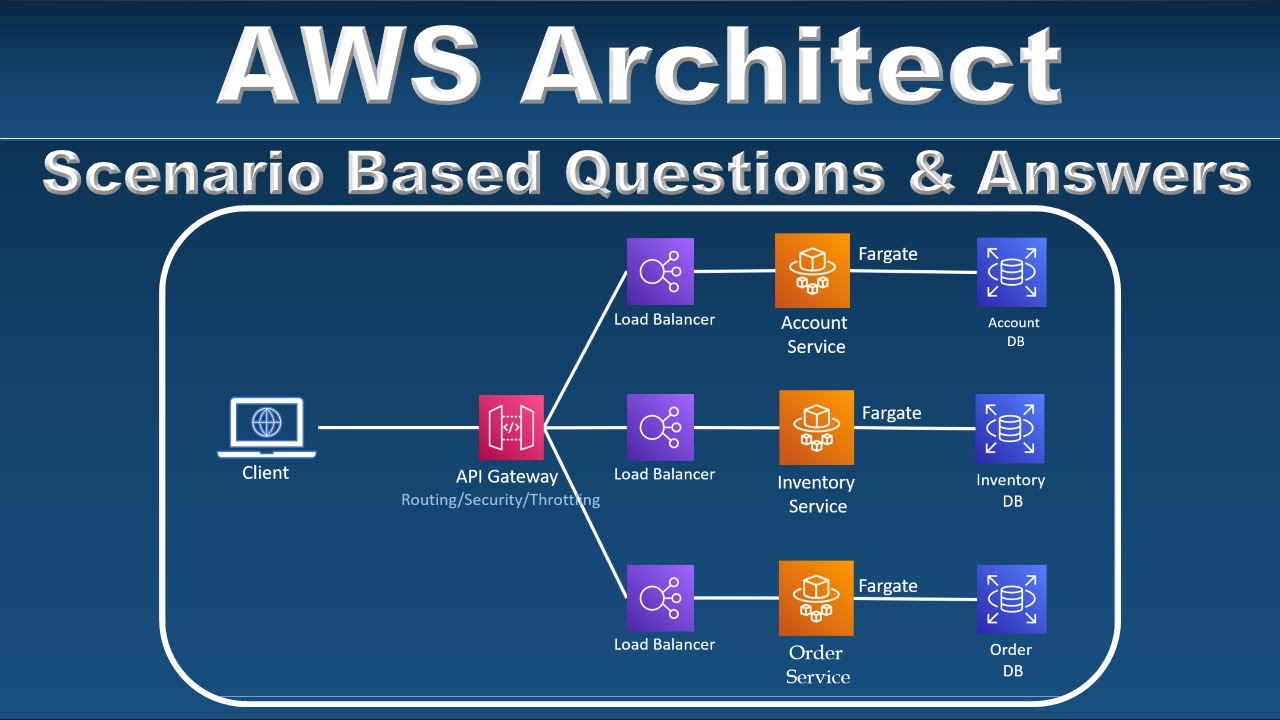
AWS Solution Architect Interview Questions and Answers - Part 2
5.0 / 5 (0 votes)
