Growth of Current in LR circuit (Time domain Analysis of 1st order LR circuit) BEE | in हिन्दी
Summary
TLDRThe video covers the analysis of a first-order alarm circuit, focusing on the role of inductors and resistors. It explains how energy is stored in the circuit and how inductors resist changes in current. Key concepts like potential difference, current direction, and voltage laws are discussed, along with equations related to inductive time constants. The instructor highlights the importance of understanding how current evolves over time, emphasizing the inductive time constant's significance in electrical circuits. The video concludes with a teaser for the next session, which will introduce alternating current concepts.
Takeaways
- 😀 The first-order alarm circuit consists of an inductor and a resistor connected to a battery.
- 😀 An inductor stores electrical energy and resists changes in current flow.
- 😀 A resistor dissipates energy, converting it to heat and limiting current flow.
- 😀 The circuit's behavior is governed by Kirchhoff's voltage law, ensuring voltage sums to zero in a closed loop.
- 😀 Inductors produce an induced current that opposes changes in the main current.
- 😀 The time constant (τ) of an inductor circuit is crucial for understanding current growth, calculated as τ = L/R.
- 😀 The induced current increases until it reaches approximately 63.2% of its maximum value, known as the time constant.
- 😀 A growing current indicates that the circuit is transitioning towards its maximum current level.
- 😀 The relationship between voltage and current can be expressed mathematically to analyze circuit behavior.
- 😀 Future lessons will cover concepts related to alternating current (AC) circuits, expanding on these foundational principles.
Q & A
What is the main focus of the discussion in the video?
-The video primarily discusses mobile security, bug bounty programs, and the vulnerability reporting processes in Android applications.
Who are the key speakers in the video?
-The key speakers in the video are Fabian, known as LiveOverflow, and Kristoffer from Google.
What is a bug bounty program?
-A bug bounty program is an initiative where organizations invite external security researchers to discover and report vulnerabilities in their software in exchange for rewards.
How do mobile security and vulnerability reporting intersect?
-Mobile security focuses on protecting mobile devices from threats, while vulnerability reporting is a critical component of ensuring security by allowing researchers to report identified weaknesses in mobile applications.
What are some common types of vulnerabilities in Android applications?
-Common vulnerabilities include improper data storage, insecure communication, and insufficient security measures in third-party libraries.
What role does community engagement play in improving mobile security?
-Community engagement helps organizations gather insights from a diverse group of security researchers, fostering collaboration and enhancing the overall security of mobile applications.
What are the benefits of participating in a bug bounty program for researchers?
-Researchers benefit from bug bounty programs by gaining financial rewards, recognition in the security community, and the opportunity to contribute to the security of widely used applications.
What challenges do organizations face when implementing bug bounty programs?
-Challenges include managing the influx of reports, ensuring timely responses, and integrating findings into the development process.
How can organizations encourage responsible disclosure of vulnerabilities?
-Organizations can encourage responsible disclosure by clearly outlining their policies, providing guidelines for reporting, and maintaining open communication with researchers.
What future trends in mobile security are anticipated?
-Future trends may include increased use of machine learning for threat detection, more robust security frameworks, and a greater emphasis on user privacy.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantVoir Plus de Vidéos Connexes

Electrical Engineering: Ch 8: RC & RL Circuits (1 of 43) RC & RL Circuits Introduction

#1783 Gyrator (part 3 of 4)
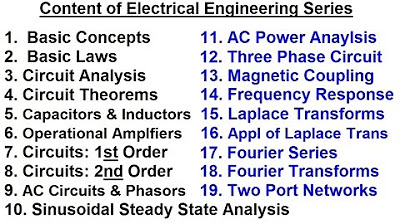
Electrical Engineering: Basic Concepts (1 of 7) Content
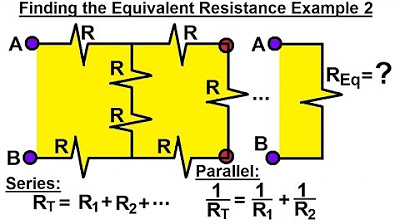
Electrical Engineering: Basic Laws (17 of 31) Finding the Equivalent Resistor Ex. 2

Simple Fire Alarm Circuit
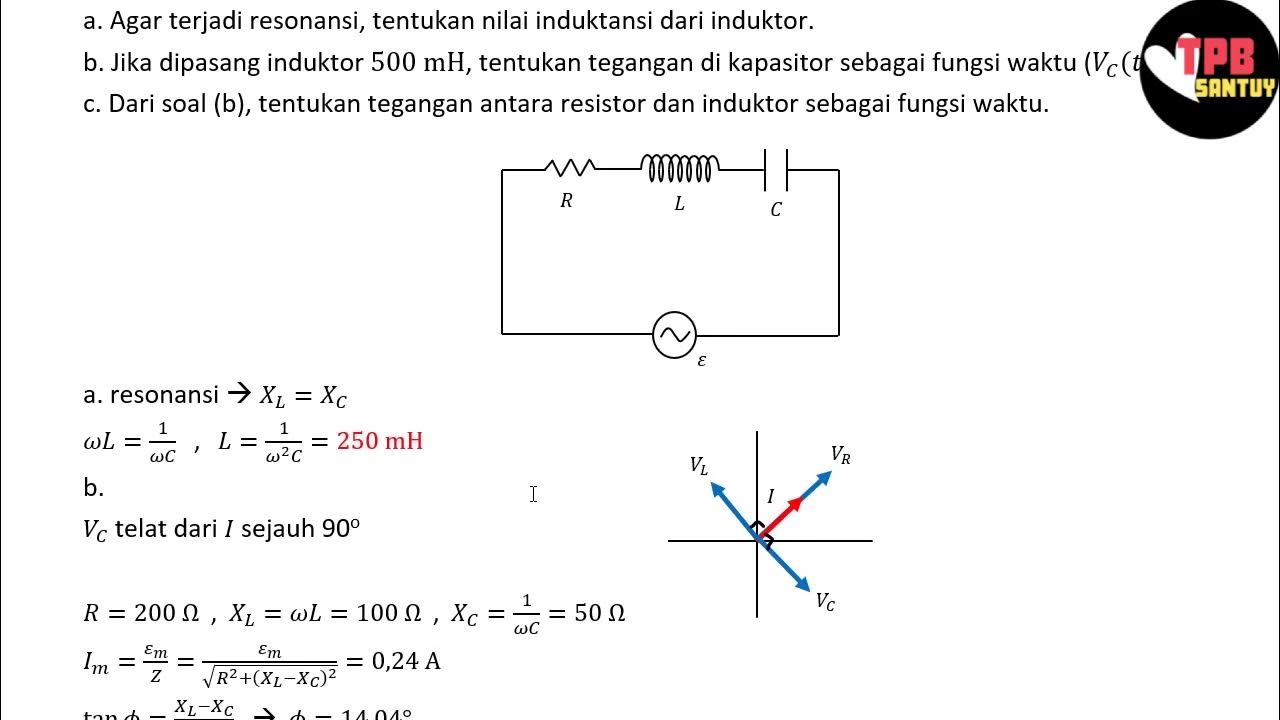
Analisis Rangkaian AC | Rangkaian AC | Part 3 | Fisika Dasar
5.0 / 5 (0 votes)
