SAML vs. OpenID (OIDC): What's the Difference?
Summary
TLDRForeign, OpenID Connect, and SAML are both Single Sign-On (SSO) protocols. SAML is a mature protocol that securely federates identity for authentication and authorization in web apps but can be complex to implement. OpenID Connect is simpler, high-performance, and focuses on authentication, making it popular for mobile apps. Both protocols can be used together with other standards depending on the use case. Jumpcloud offers both SAML and OpenID configurations for SSO implementation.
Takeaways
- 🔐 **SAML and OpenID Connect are both SSO protocols**: They facilitate single sign-on for users.
- 🤝 **SAML focuses on identity federation**: It securely federates identity for authentication and authorization into web apps.
- 🛠️ **SAML can be complex to implement**: It requires XML schemas and can be more challenging for service providers.
- 📑 **SAML uses XML for user information**: It transmits granular user data for access control and permissions.
- 📱 **OpenID is lightweight and high-performance**: It's simpler for service providers to implement, focusing solely on authentication.
- 📲 **OpenID is popular for mobile apps**: It manages sign-in flows and assertions efficiently for mobile applications.
- 🔒 **SAML secures credentials**: Passwords are neither sent over the wire nor stored with service providers.
- 🔗 **SAML authorizes resource access**: It signs users in with one set of credentials and authorizes access between IDP and SP.
- 🌐 **SAML is web-centric**: It uses XML documents and web browsers to transmit assertions about the user.
- 🔄 **OpenID is based on OAuth 2.0**: It uses REST and JSON for message flows, making it accessible via APIs.
- 🆔 **OpenID uses ID tokens**: It transmits user information as claims, which are OpenID's equivalent to SAML's assertions.
- 🤖 **Both protocols can coexist**: They can be used in combination with other standards depending on the use case.
- 🚀 **JumpCloud supports both**: Offers configurations for both SAML and OpenID, along with connectors for SSO implementation.
Q & A
What are the primary uses of Foreign, Open ID Connect, and SAML?
-Foreign, Open ID Connect, and SAML are primarily used for single sign-on (SSO) to facilitate the authentication process across different platforms and applications.
How does SAML contribute to SSO?
-SAML allows an identity provider (IDP) to securely federate identity for authentication and authorization into web applications.
What is the complexity level of implementing SAML for service providers?
-SAML can be more difficult for service providers (SPs) to implement, and some even charge for it due to its complexity.
What is the role of XML schemas in SAML?
-XML schemas are used in SAML to transmit user information, allowing for granular management of access control and permissions.
Why might OpenID be simpler for SPs to implement than SAML?
-OpenID is simpler for SPs to implement because it is lightweight and high performance, focusing solely on authentication.
What is the primary focus of OpenID Connect?
-OpenID Connect is primarily focused on authentication and is popular for managing sign-in flows and assertions for mobile applications.
How does SAML handle the transmission of passwords?
-SAML ensures that passwords are not sent over the wire or stored with service providers, enhancing security.
What is the role of XML documents in SAML?
-XML documents in SAML transmit assertions about the user, including who they are and how that information was issued.
How does OpenID Connect differ from SAML in terms of user information transmission?
-OpenID Connect uses ID tokens to transmit information or claims about the user, as opposed to SAML's XML documents.
What is the significance of claims in OpenID Connect?
-Claims in OpenID Connect are equivalent to SAML assertions and are used to transmit user identity information.
Can SAML and OpenID Connect be used together?
-Yes, SAML and OpenID Connect can be used in combination with other authentication standards depending on the use case.
What does Jumpcloud offer regarding SSO implementation?
-Jumpcloud offers both SAML and OpenID configurations for SSO implementation, as well as pre-built and custom connectors.
Outlines

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantMindmap

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantKeywords

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantHighlights

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantTranscripts

Cette section est réservée aux utilisateurs payants. Améliorez votre compte pour accéder à cette section.
Améliorer maintenantVoir Plus de Vidéos Connexes

What Is Single Sign-on (SSO)? How It Works
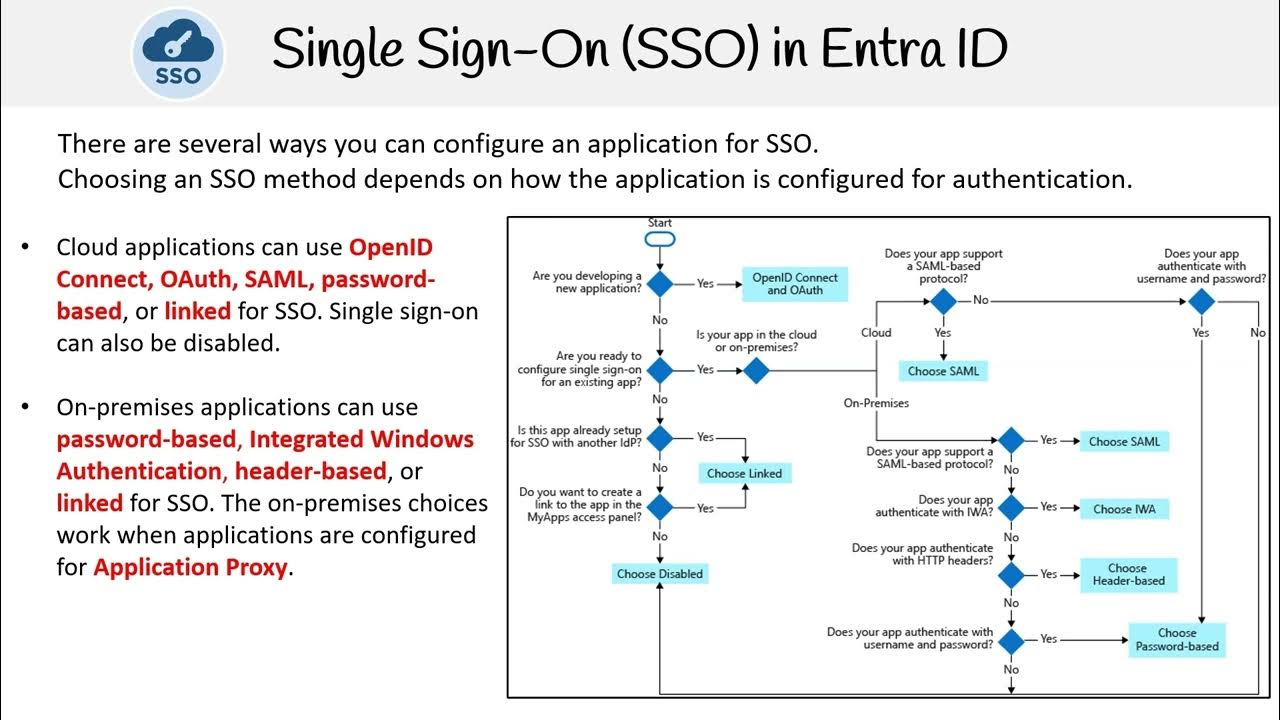
AZ 305 — Single Sign On SSO

Authentication fundamentals: Web applications | Microsoft Entra ID

Single Sign On Menggunakan OAuth

An Illustrated Guide to OAuth and OpenID Connect

CompTIA Security+ SY0-701 Course - 4.6 Implement and Maintain Identity & Access Management - PART A
5.0 / 5 (0 votes)
