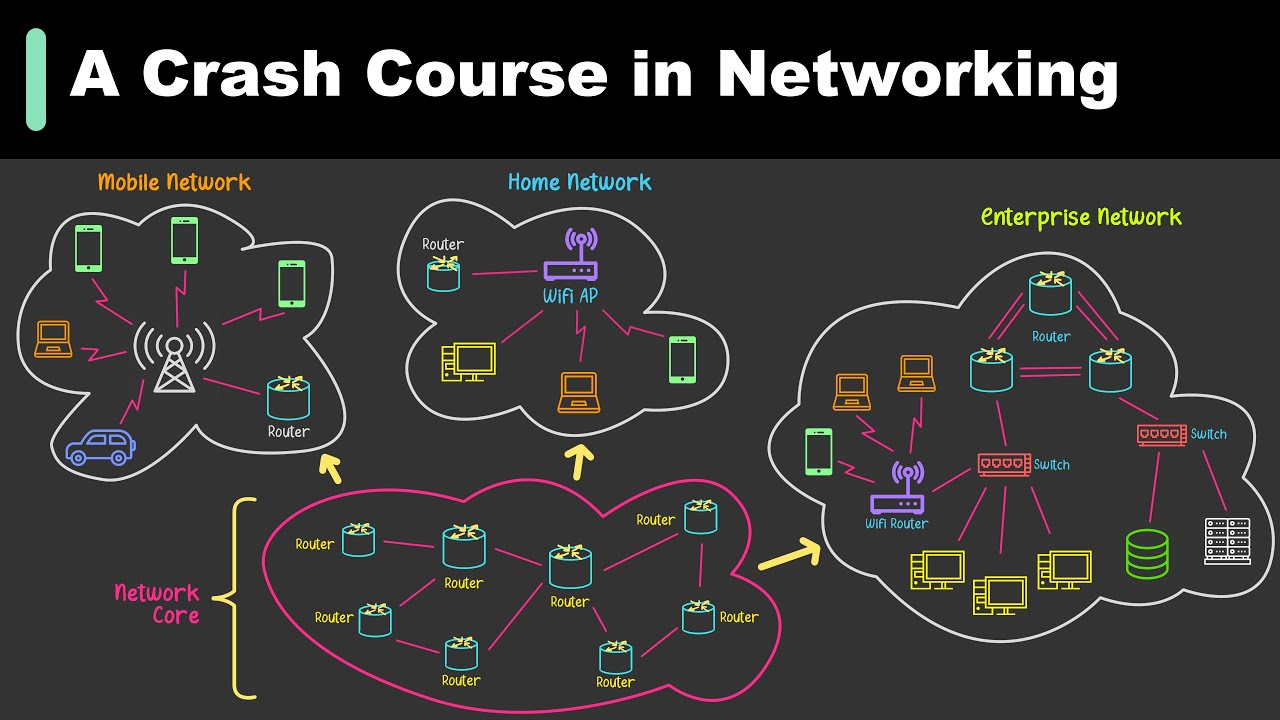
Network Services - CompTIA A+ 220-1101 - 2.4
Summary
TLDRThis video script explores the inner workings of a data center, detailing the crucial network services that support modern organizations. It covers DNS for domain-to-IP address translation, DHCP for IP address assignment, file servers for centralized storage, print servers for network printing, and mail servers for email management. The script also delves into security aspects like SIEM for log consolidation, authentication servers for secure access, and firewalls for network protection. Additionally, it touches on emerging technologies like IoT devices and the challenges of managing legacy systems.
Takeaways
- 🌐 Data centers typically consist of rows of 19-inch racks housing various computing systems.
- 🔄 DNS servers are essential for translating fully qualified domain names into IP addresses, facilitating web browsing and communication.
- 📡 DHCP servers automatically assign and configure IP addresses, ensuring seamless network connectivity for devices.
- 🗂 File servers provide centralized storage for files, accessible from any device on the network, using protocols like SMB or AFP.
- 🖨 Print servers allow network users to access and send print jobs to centralized printers, using protocols such as SMB, IPP, or LPD.
- 💌 Mail servers are critical for an organization's email communication, often managed with 24/7 support to ensure availability.
- 📝 Syslog is a protocol for consolidating logs from various services into a central database, aiding in administration and security.
- 🌐 Web servers respond to browser requests using protocols like HTTP/HTTPS and generate pages using HTML or HTML5.
- 🔒 Authentication servers centralize usernames and passwords, providing a single method for accessing multiple enterprise services.
- 📫 Spam management involves identifying and handling unsolicited messages, often using a separate mail gateway or spam filters.
- 🛡️ Security functions like firewalls, intrusion detection, and bandwidth shaping are often consolidated in devices like next-gen firewalls or UTMs.
- 🔄 Load balancers distribute network traffic across multiple servers to ensure continuous uptime and optimize resource utilization.
- 🛡️ Proxy servers add an extra layer of security to internet communications by acting as intermediaries that filter and control access.
- 🏭 SCADA or ICS systems are used for the control and management of industrial equipment, often isolated for security reasons.
- 📻 Legacy systems, though old, often run critical services and can be challenging to maintain due to outdated software and hardware.
- 🔩 Embedded systems are purpose-built devices with limited access, relying on manufacturers for support and maintenance.
- 🔗 IoT devices are increasingly connecting to enterprise networks, requiring careful security considerations and often network segmentation.
Q & A
What is the primary function of a DNS server in a data center?
-A DNS server, which stands for Domain Name System, is primarily responsible for converting fully qualified domain names into IP addresses, facilitating communication between clients and servers on the internet.
Why is DNS considered a critical service for communication processes?
-DNS is critical because it enables the translation of human-readable domain names into IP addresses that computers use to communicate with each other, which is essential for internet navigation and data exchange.
What does DHCP stand for, and what is its role in a network?
-DHCP stands for Dynamic Host Configuration Protocol, and its role is to automatically assign and configure IP address settings on local devices, ensuring that they can communicate on the network without manual configuration.
Why are multiple DHCP servers used in an enterprise environment?
-Multiple DHCP servers are used for redundancy, ensuring that IP address assignment and configuration services are always available even if one DHCP server becomes unavailable.
What is a file server and how does it benefit users in an organization?
-A file server is a centralized storage device with a set of folders for storing information. It benefits users by allowing them to access their personal files from any device connected to the network, enhancing collaboration and data accessibility.
How does a print server enable network printing in an organization?
-A print server, either hardware or software, connects a printer to the network, allowing users to send print jobs from any device on the network to the centralized printer, improving resource sharing and accessibility.
What is the purpose of a mail server in an organization?
-A mail server is responsible for sending and receiving email for an organization. It is a critical service that often requires 24/7 support to ensure continuous availability and functionality.
Why is consolidating logs to a central database beneficial for administrators?
-Consolidating logs to a central database simplifies the process of accessing and analyzing logs from various services, making it easier for administrators to monitor system activities, troubleshoot issues, and enhance security.
What is a SIEM, and how does it relate to log management?
-A SIEM, or Security Information and Event Manager, is a system that collects, analyzes, and stores log files from various sources. It helps in enhancing security by providing a centralized platform for monitoring and analyzing logs over an extended period.
What is the role of an authentication server in an enterprise network?
-An authentication server centralizes the management of usernames and passwords for various services in an enterprise network. It ensures secure access to resources and streamlines the authentication process across different servers and applications.
How do load balancers contribute to the uptime and availability of services in a data center?
-Load balancers distribute network traffic and requests across multiple servers, ensuring that no single server bears too much load. They also provide redundancy by rerouting traffic if a server becomes unresponsive, thus maintaining high availability of services.
What is the significance of managing spam messages in an organization's email system?
-Managing spam messages is important for security, productivity, and resource optimization. It prevents unwanted and potentially harmful content from reaching users, reduces the load on mail servers, and helps in maintaining the integrity of the email system.
What are the key features and functions of a next-generation firewall or UTM in an enterprise?
-A next-generation firewall or UTM provides a range of security functions, including URL filtering, content inspection, malware detection, spam filtering, and intrusion detection/prevention. They also offer networking features like routing, switching, and bandwidth shaping, enhancing the overall security and performance of the network.
What is the purpose of a proxy server in enhancing internet communication security?
-A proxy server acts as an intermediary in internet communications, filtering and inspecting requests and responses to ensure security. It can perform access control, caching, URL filtering, and other security functions, adding an extra layer of protection to the network.
What is the role of SCADA or ICS systems in industrial environments?
-SCADA, or Supervisory Control And Data Acquisition systems, are used for the control and management of industrial machines and processes. They allow operators to monitor and control equipment remotely, ensuring efficient operation and reducing the risk of downtime in critical systems.
Why are legacy systems often retained in data centers despite their age?
-Legacy systems are retained because they often run critical services that are essential to the organization's operations. Although they may be on older software or hardware, the importance of the service they provide justifies their continued use and the challenges associated with maintaining them.
What are embedded systems, and how do they differ from traditional computing systems in a data center?
-Embedded systems are purpose-built devices designed for specific tasks or services, with limited or no access to the underlying operating system. They differ from traditional computing systems by offering a focused functionality and often relying on the manufacturer for support and maintenance.
What is the significance of IoT devices in the context of enterprise networks, and how are they managed for security?
-IoT devices are increasingly connecting to enterprise networks, offering new capabilities and functionalities. However, due to their potential security risks, they are often segmented onto their own network with additional security measures to prevent unauthorized access and protect the main network.
Outlines

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraMindmap

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraKeywords

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraHighlights

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraTranscripts

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahora5.0 / 5 (0 votes)