Hashing and Digital Signatures - SY0-601 CompTIA Security+ : 2.8
Summary
TLDRThe video explains how hashing algorithms convert any input—like files or passwords—into a fixed-size, unique string called a hash, which acts like a digital fingerprint. Hashing is a one-way process, meaning the original data cannot be reconstructed from the hash. It's used for secure password storage, data integrity verification, and digital signatures. Collisions, where two different inputs generate the same hash, are rare but problematic. Salting, which adds randomization to passwords, makes them more secure. The video also covers how digital signatures verify message authenticity and integrity using hashing and encryption.
Takeaways
- 🔐 A hash is a unique string generated from any type of input (document, audio, video, etc.), acting like a fingerprint for the data.
- 🛑 A hash is a one-way function, meaning you cannot recreate the original file from the hash.
- 🔑 Hashing is commonly used for securely storing passwords by converting them into a hash, preventing access to the original password.
- 🔍 Hashing ensures data integrity by verifying that two copies of the same file have identical hashes.
- 🧾 Digital signatures use hashing in combination with encryption to authenticate data sources and confirm integrity.
- 🚫 Collisions, where different inputs create the same hash, are rare but occurred with the MD5 algorithm, making it less reliable.
- 🧂 Adding a 'salt' (a random value) to a hash prevents attackers from using precomputed 'rainbow tables' to crack passwords.
- ⚡ Even a small change in the input will result in a completely different hash, showcasing the sensitivity of hashing algorithms.
- 🗝️ Digital signatures involve encrypting a hash with a private key, and recipients verify the signature using the sender's public key.
- 🛠️ Hashing algorithms like SHA256 create fixed-length outputs, regardless of the input size, providing consistency for verification.
Q & A
What is a hash, and what is its primary purpose?
-A hash is a function that converts any input, such as a document, audio, video, or file of any size, into a unique string of text called a message digest. Its primary purpose is to create a fixed-size representation (or fingerprint) of the data, ensuring data integrity and secure storage of sensitive information like passwords.
Why is hashing considered a one-way process?
-Hashing is considered a one-way process because once data is converted into a hash, it's impossible to reverse-engineer the original data from the hash. This property makes hashing ideal for securely storing passwords and ensuring data integrity.
How is hashing used to store passwords securely?
-When a password is hashed, the original password is transformed into a fixed-size hash value. This hash is stored instead of the plain text password. When a user logs in, the system hashes the input password and compares it to the stored hash. If they match, access is granted. This prevents storing passwords in plain text and protects against unauthorized access.
What is the purpose of adding 'salt' to a hash, and how does it improve security?
-Adding 'salt' to a hash involves introducing a random value to each password before hashing it. This ensures that even if two users have the same password, their stored hash values will be different. This process prevents attackers from using precomputed hash values, known as rainbow tables, to crack passwords.
What is a hash collision, and why is it problematic?
-A hash collision occurs when two different inputs produce the same hash value. This is problematic because it undermines the uniqueness of the hash function, potentially allowing malicious data to be validated as authentic or causing confusion in data integrity checks.
Why is the MD5 hashing algorithm no longer recommended for use?
-The MD5 hashing algorithm is no longer recommended because it is vulnerable to hash collisions. In 1996, it was discovered that MD5 could generate the same hash for different inputs, which compromises its security and integrity.
How does hashing ensure the integrity of a file during transfer?
-To ensure file integrity during transfer, a hash of the original file is created before the transfer. After the file is received, the same hashing algorithm is applied to the transferred file. If the resulting hash matches the original hash, the file has not been altered during transfer.
What role does hashing play in digital signatures?
-In digital signatures, hashing is used to create a unique hash of a document. This hash is then encrypted with the sender's private key to create the digital signature. The recipient can decrypt the signature with the sender's public key and compare the resulting hash with the hash of the received document to verify the authenticity and integrity of the message.
What is the difference between a public key and a private key in digital signatures?
-A private key is used by the sender to sign a document, creating a digital signature, while a public key is used by the recipient to verify the signature. The private key is kept secret and known only to the sender, while the public key is shared openly.
How does a digital signature verify the sender's identity and message integrity?
-A digital signature verifies the sender's identity and message integrity by using the sender's private key to encrypt a hash of the message. The recipient decrypts the signature using the sender's public key and compares the hash with a newly generated hash of the message. If they match, it confirms the sender's identity and that the message has not been altered.
Outlines

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraMindmap

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraKeywords

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraHighlights

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraTranscripts

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraVer Más Videos Relacionados

49. OCR A Level (H446) SLR9 - 1.3 Hashing

Blockchain Hashing Explained! (You NEED to understand this)
What is a Cryptographic Hashing Function? (Example + Purpose)

Database Security - SY0-601 CompTIA Security+ : 3.2

What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
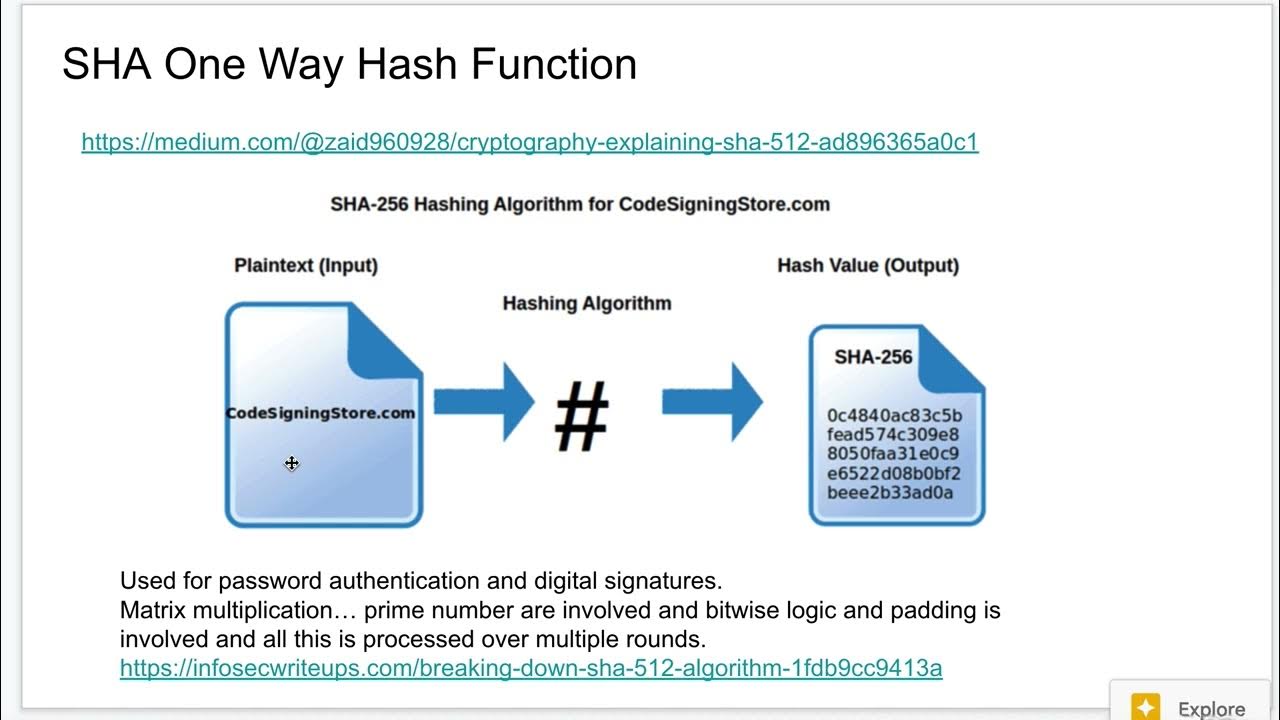
One Way Hash Explained
5.0 / 5 (0 votes)
