AP Computer Science Principles DAT-1 Faculty Lecture on Data Representation
Summary
TLDRProfessor Paul Tiemman from Rochester Institute of Technology explains how data is internally represented in computers, focusing on binary and decimal number systems. He covers converting binary to decimal and vice versa, emphasizing positional numbering systems and powers of two. The presentation also explores the RGB color model and delves into steganography, demonstrating how to hide messages within digital images by manipulating pixel bits. Tiemman shows that even with significant bit reduction, images can still convey their original content, highlighting the power of digital manipulation and the importance of skepticism when interpreting digital media.
Takeaways
- 😀 Professor Paul Tiemman from Rochester Institute of Technology introduces the concept of data representation in computers, focusing on binary and decimal systems.
- 🔑 The positional numbering system is explained, emphasizing that each digit in a binary number represents a power of 2, which is key to converting binary to decimal.
- 📊 A methodical approach to converting binary to decimal is demonstrated using a chart to identify and sum the relevant powers of 2.
- 🔍 An important check is highlighted for binary to decimal conversion: if the binary number ends in 0, the decimal result must be even, ensuring conversion accuracy.
- 🔄 The reverse process of converting decimal to binary is explained, using a similar chart method but starting with powers of 2 greater than the decimal number.
- 💡 The significance of the least significant bit (LSB) in determining the parity (odd or even) of a decimal number when converting from binary is discussed.
- 🖼️ The concept of image representation in computers using pixels and the RGB color model is introduced, showing how colors are created by combining red, green, and blue intensities.
- 🎨 The potential for steganography in digital images is explored, demonstrating how messages can be hidden by manipulating pixel data without noticeably altering the image.
- 📚 A practical example of steganography is given, where the entire text of 'Alice in Wonderland' is encoded within the least significant bits of a digital image's pixels.
- 🤓 The presentation concludes with a binary joke, emphasizing the importance of understanding binary for computer scientists and highlighting the manipulability of digital data.
Q & A
What is the main topic of Paul Tiemman's presentation?
-The main topic of Paul Tiemman's presentation is how data, including numbers, images, and text, is represented internally in a computer using binary numbers.
How does positional numbering system work in the context of binary numbers?
-In a positional numbering system, each position in a number represents a particular power of the base of the number. In binary, each bit represents a different power of 2, starting from 2^0 on the right and increasing as you move left.
What is the process for converting a binary number to a decimal number?
-To convert a binary number to a decimal, you determine which powers of 2 are represented by the 1s in the binary number and sum those powers. For example, the binary number 1 1 0 0 1 0 1 0 1 0 is converted to decimal by summing 512 + 256 + 32 + 8 + 2, which equals 810.
How can you check if a binary number represents an even or odd decimal number?
-If a binary number represents an odd decimal number, the least significant bit (rightmost bit) must be 1. If it's 0, the number is even. This is because all powers of 2, except 2^0, are even.
What is the method for converting a decimal number to a binary number?
-To convert a decimal number to binary, you determine which powers of 2 can be subtracted from the number until you reach zero, marking a 1 for each power of 2 used. For example, to convert 453 to binary, you would start with the highest power of 2 less than 453 (which is 256), mark a 1, subtract 256 from 453, and continue this process for the remaining number.
How many unique values can be represented with an 8-bit number?
-With an 8-bit number, you can represent 256 unique values, calculated by raising 2 to the power of the number of bits (2^8).
What is the RGB color model and how is it used in computing?
-The RGB color model is an additive color model where red (R), green (G), and blue (B) intensities are combined to create various colors. In computing, images are represented by pixels, each with an RGB value, allowing for a wide range of colors to be displayed.
What is steganography and how can it be applied to digital images?
-Steganography is the practice of hiding a message within another message or object. In the context of digital images, it involves modifying some of the bits in an image's pixels to encode a hidden message without significantly altering the image's appearance.
How does the presenter demonstrate the encoding of a message in a digital image?
-The presenter demonstrates encoding a message by using the least significant bit of the red channel in each pixel to store bits of an ASCII character. The entire text of 'Alice in Wonderland' is encoded in the pixels of an image, with only about half of the pixels being changed, making the alteration nearly imperceptible.
What is the significance of the joke 'There are 10 types of people in the world' mentioned in the presentation?
-The joke 'There are 10 types of people in the world: those who understand binary, and those who don't' is a play on the fact that binary is a base-2 number system, which only has two digits, 0 and 1. It humorously implies that there are only two kinds of people: those who can think in binary and those who cannot.
Outlines

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraMindmap

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraKeywords

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraHighlights

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraTranscripts

Esta sección está disponible solo para usuarios con suscripción. Por favor, mejora tu plan para acceder a esta parte.
Mejorar ahoraVer Más Videos Relacionados

Teknologi Digital • Part 1: Pengertian Teknologi Digital, Sistem Bilangan, dan Kode Biner

Bilangan Biner | Materi Teknologi Digital Kelas 12 SMA

SISTEM BILANGAN | Berpikir Komputasional | Informatika Kelas 8 Kurikulum Merdeka | Fase D
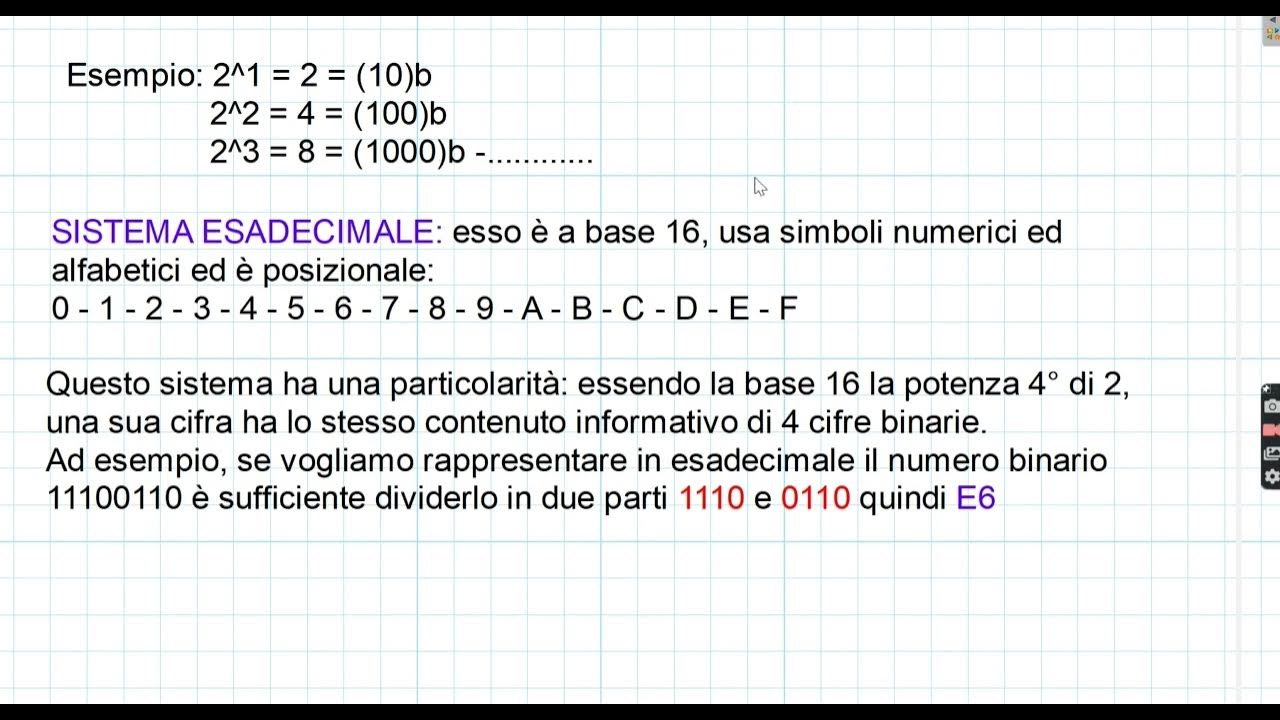
ED2. Sistemi di Numerazione

[Part 1] Unit 2.2 - Binary Addition

#3 Sistem Komputer - Pengenalan Bilangan Biner | Informatika 7 - Pelajar Hebat
5.0 / 5 (0 votes)
