2. Basic Cyber Security
Summary
TLDRThis video introduces the fundamentals of C security, focusing on key concepts like data integrity and availability. It discusses the roles of the Red Team and Blue Team in cybersecurity, highlighting their offensive and defensive strategies. The video also covers the phases of penetration testing, including planning, reconnaissance, scanning, gaining access, maintaining access, and covering tracks. Each phase is explored with the tools and techniques used to ensure system security. The video sets the stage for a deeper dive into cybersecurity practices and tools in the upcoming episodes.
Takeaways
- 😀 Understand the importance of data integrity and availability in cybersecurity.
- 😀 Cybersecurity can be split into two primary teams: Red Team and Blue Team (Defender Team).
- 😀 Red Team simulates attacks (like APTs or hackers) to identify weaknesses in the system.
- 😀 Blue Team defends the system by creating rules and policies to maintain its security.
- 😀 Both Red and Blue Teams have the same goal: protecting the system, but they approach it differently.
- 😀 The first phase in cybersecurity testing is planning and scoping to define the target and scope.
- 😀 Reconnaissance follows, where information is gathered based on the defined scope.
- 😀 The scanning phase involves further enumeration and analysis of the collected data.
- 😀 Gaining access, maintaining access, and covering tracks are next steps after reconnaissance and scanning.
- 😀 The final phases include analysis and reporting, where the gathered data is reviewed and presented.
- 😀 Tools specific to each phase of testing will be used to achieve effective cybersecurity evaluation.
Q & A
What are the two main aspects of C security discussed in the video?
-The two main aspects of C security discussed are data **integrity** and **availability**. These are critical concepts for ensuring the security and reliability of systems.
What is the primary difference between the Red Team and the Blue Team in cybersecurity?
-The primary difference is that the **Red Team** focuses on offensive tactics, simulating attacks to identify vulnerabilities, while the **Blue Team** focuses on defensive tactics, working to prevent attacks and secure the system.
How does the Red Team help in improving system security?
-The Red Team helps by simulating cyberattacks and identifying vulnerabilities in a system. They then provide advice and recommendations on how to strengthen the security of the system.
What role does the Blue Team play in cybersecurity?
-The Blue Team plays a defensive role by setting up policies, rules, and defenses to protect the system. They work to prevent intrusions and respond to threats.
What is the significance of data integrity and availability in security?
-Data integrity ensures that the data is accurate, consistent, and trustworthy, while availability ensures that authorized users can access the system or data when needed. Both are vital to maintaining secure and reliable systems.
What are the phases involved in penetration testing?
-The phases of penetration testing include: **Planning & Scoping**, **Reconnaissance**, **Scanning & Enumeration**, **Gaining Access**, **Maintaining Access**, **Covering Tracks**, and **Analysis and Reporting**.
What is the first phase in penetration testing and what does it involve?
-The first phase is **Planning & Scoping**, where the objectives and scope of the penetration test are defined. It involves establishing what to test and the target of the assessment.
What happens during the **Reconnaissance** phase of penetration testing?
-In the **Reconnaissance** phase, the tester gathers information about the target system based on the defined scope, which helps in understanding potential vulnerabilities.
What is the goal of the **Scanning & Enumeration** phase?
-The goal of the **Scanning & Enumeration** phase is to conduct deeper analysis of the target system through scanning and enumeration to identify weaknesses or vulnerabilities.
Why is the **Covering Tracks** phase important in penetration testing?
-The **Covering Tracks** phase is important because it ensures that the tester leaves no trace of their activities, simulating how an attacker might attempt to hide their presence in the system.
How does **Analysis and Reporting** help after a penetration test?
-The **Analysis and Reporting** phase involves analyzing the findings from the test and creating a report that outlines vulnerabilities discovered, the risks they pose, and recommendations for improving security.
Outlines

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنMindmap

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنKeywords

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنHighlights

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنTranscripts

هذا القسم متوفر فقط للمشتركين. يرجى الترقية للوصول إلى هذه الميزة.
قم بالترقية الآنتصفح المزيد من مقاطع الفيديو ذات الصلة

O que é segurança da informação?

Fundamentals of Information Security

Os pilares da Segurança da Informação - @CursoemVideo Segurança da Informação - Módulo 0

CISSP Domain 1 | Security Risk and Governance | Introduction to CISSP | CISSP Training
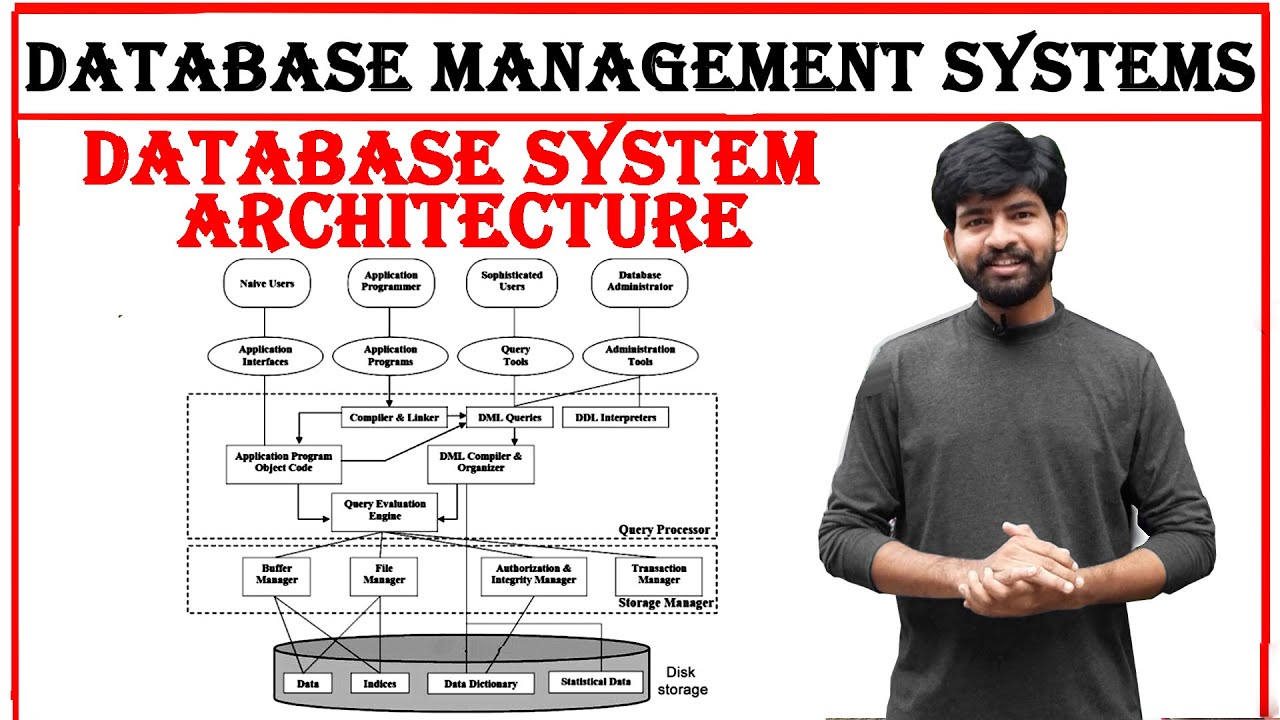
database system architecture in dbms | database management system | Architecture | DBMS | btech

Cyber Security Pada Cloud Platform. Part 01
5.0 / 5 (0 votes)
