AWS VPC Tutorial | Membuat VPC, Subnet, Route Table | AWS VPC | Central Data Technology
Summary
TLDRThis tutorial walks through the process of creating a Virtual Private Cloud (VPC) on AWS, highlighting key steps such as setting up VPCs, subnets (public and private), configuring routing tables, and ensuring internet access via Internet and NAT Gateways. It emphasizes creating a VPC manually, without using the wizard, and covers critical networking concepts to ensure secure and efficient connections within AWS services. By the end of the video, users will have a fully functional VPC setup ready for deploying AWS services.
Takeaways
- 😀 Set up a Virtual Private Cloud (VPC) on AWS to manage your network resources.
- 😀 Start by creating a VPC, which serves as the foundation for your AWS network infrastructure.
- 😀 Create subnets within the VPC, defining whether they will be public or private.
- 😀 Public subnets can be accessed from the internet, while private subnets are isolated within the VPC.
- 😀 Attach an internet gateway to the VPC to enable communication with the internet for public subnets.
- 😀 Configure route tables for both public and private subnets to control traffic flow within the VPC.
- 😀 A NAT gateway in the public subnet allows private subnet instances to access the internet for outbound traffic.
- 😀 Associate the appropriate route tables with each subnet to enable internet and private network access.
- 😀 Ensure that your VPC's routing is correctly set up to allow traffic from the private subnet to the internet via the NAT gateway.
- 😀 Test the configuration by launching instances in both public and private subnets to confirm connectivity.
Q & A
What is the first step in setting up a Virtual Private Cloud (VPC) in AWS?
-The first step is to create a VPC by going to the AWS Management Console, navigating to the 'VPC' section, and choosing 'Create VPC'. You will need to provide a name for the VPC and a CIDR block, such as 10.0.0.0/16.
How do you create subnets within your VPC?
-To create subnets, go to the 'Subnets' section under VPC, select 'Create Subnet', and choose the VPC you created. You will then define the subnet's name and CIDR block for both public and private subnets.
What is the difference between a public and a private subnet in a VPC?
-A public subnet can be accessed from the internet, typically used for web servers and other public-facing resources. A private subnet, on the other hand, is isolated from direct internet access, typically used for databases or backend systems.
Why is an Internet Gateway necessary for a VPC?
-An Internet Gateway is needed to provide internet connectivity for the public subnet. It allows instances in the public subnet to communicate with the internet, enabling inbound and outbound traffic.
How do you configure the route tables for the subnets?
-After creating the subnets, configure the route tables by going to the 'Route Tables' section in the VPC dashboard. For the public subnet, create a route directing outbound traffic (0.0.0.0/0) to the Internet Gateway. For the private subnet, create a route to direct traffic to the NAT Gateway.
What is the role of a NAT Gateway in this setup?
-The NAT Gateway allows instances in the private subnet to access the internet for outbound traffic (e.g., for updates or external API calls), while keeping the private subnet secure by not exposing it directly to the internet.
How do you create a NAT Gateway in AWS?
-To create a NAT Gateway, go to the 'NAT Gateways' section in the VPC dashboard, create the gateway in a public subnet, and then update the private subnet's route table to direct outbound traffic to the NAT Gateway.
What is the purpose of associating route tables with subnets?
-Associating route tables with subnets allows you to define how traffic should flow between subnets, the internet, and other resources. For example, associating a route table with the public subnet ensures it can communicate with the internet via the Internet Gateway.
How can you test the setup of a VPC with public and private subnets?
-You can test the setup by launching EC2 instances in both the public and private subnets. The instance in the public subnet should have direct internet access, while the instance in the private subnet should access the internet via the NAT Gateway.
Why do you need to create a route for outbound traffic to 0.0.0.0/0?
-The route 0.0.0.0/0 is a default route that directs all outbound traffic to the internet. It is necessary for instances in the public subnet to reach the internet, and for instances in the private subnet to use the NAT Gateway for internet access.
Outlines

此内容仅限付费用户访问。 请升级后访问。
立即升级Mindmap

此内容仅限付费用户访问。 请升级后访问。
立即升级Keywords

此内容仅限付费用户访问。 请升级后访问。
立即升级Highlights

此内容仅限付费用户访问。 请升级后访问。
立即升级Transcripts

此内容仅限付费用户访问。 请升级后访问。
立即升级浏览更多相关视频

Create AWS VPC using Terraform: AWS EKS Kubernetes Tutorial - Part 1

Build HA VPN connections between GCP and AWS [Hybrid Cloud] Easy step-step, latest 2024 -Dreametive

How to Create an AWS VPC with Public and Private Subnets

Day 59/100 || Create Subnets in AWS VPC Part -2 || 100 Days Cloud Challenge || AWS in English ||

AWS Acad Lab Cloud Web Application Builder | Building a Highly Available, Scalable Web Application
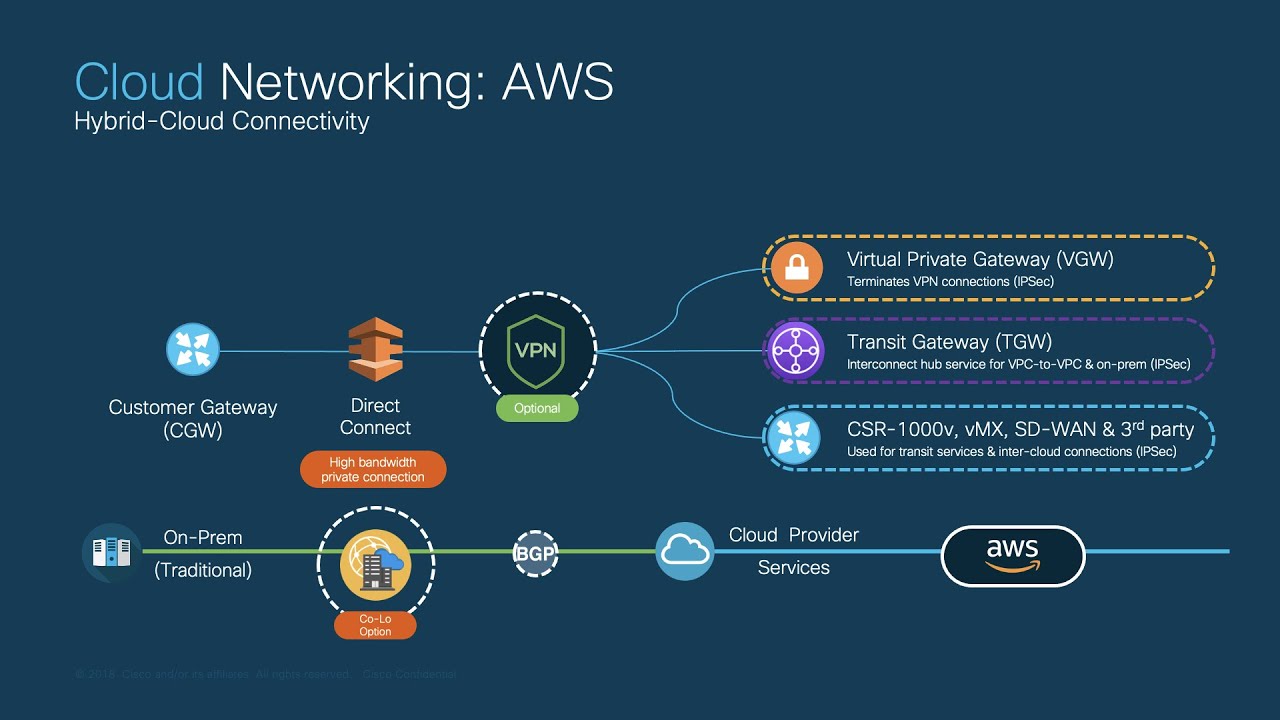
Cloud Networking Overview (Using AWS as reference)
5.0 / 5 (0 votes)
