Lecture 27: Private-key cryptography (Part I)
Summary
TLDRIn this lecture, the instructor delves into the principles of private key cryptography, emphasizing its importance in secure communication. The concepts of encryption and decryption using symmetric key algorithms are introduced, highlighting the roles of plaintext, ciphertext, and the shared secret key. The lecture covers classical techniques such as substitution and transposition ciphers, including the Caesar Cipher and monoalphabetic substitution. The challenges of key management in networks are discussed, alongside practical considerations for modern cryptographic systems. The lecture concludes by hinting at more advanced algorithms to be explored in future sessions.
Takeaways
- 😀 Private key cryptography is a critical technique for securing communication, using a shared secret key between sender and receiver.
- 😀 In symmetric key cryptography, the encryption and decryption processes use the same key to transform plaintext into ciphertext and vice versa.
- 😀 The security of symmetric key cryptography relies on the secrecy of the key, not the algorithm itself. Even if the algorithm is public, the key must be kept private for secure communication.
- 😀 Maintaining a large number of distinct keys for a communication network becomes challenging as the number of parties increases. For 'n' parties, there are n choose 2 keys.
- 😀 Classical symmetric key encryption algorithms include substitution ciphers, where letters are replaced, and transposition ciphers, where the order of letters is changed.
- 😀 Caesar Cipher, one of the oldest ciphers, shifts each letter by a fixed number of positions in the alphabet, but it can be easily broken through brute force attacks due to limited key possibilities.
- 😀 Monoalphabetic substitution ciphers use arbitrary letter mappings, offering more security than Caesar Cipher, but can still be broken using frequency analysis.
- 😀 Transposition Ciphers encrypt messages by permuting the order of letters, and the key defines the number of columns and the reading order of those columns.
- 😀 Practical cryptography for text messages and more complex data types (files, images, etc.) uses more advanced algorithms, often involving stream ciphers or block ciphers.
- 😀 Stream ciphers process data bit by bit, suitable for continuous streams like video, while block ciphers work with fixed-size blocks of data, requiring padding if necessary.
Q & A
What is the primary focus of the lecture on private key cryptography?
-The lecture focuses on the principles of private key (symmetric) cryptography, discussing its conceptual framework and classical algorithms.
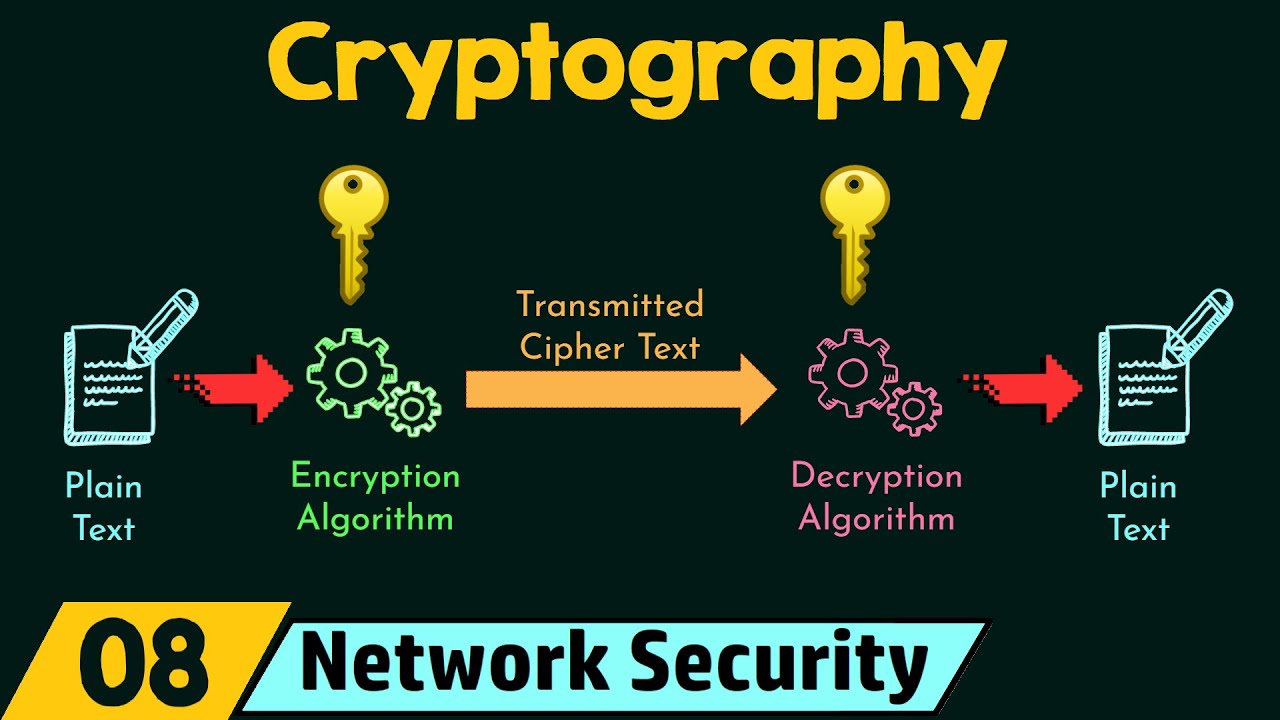
What is the difference between plaintext and ciphertext?
-Plaintext is the original message that is to be transmitted, while ciphertext is the encrypted version of that message, which appears garbled to unauthorized users.
What role does the key play in symmetric key cryptography?
-The key is a secret value shared between the sender and receiver, which is crucial for both the encryption and decryption processes. The security of the communication relies on the secrecy of this key.
Why is the method of encryption not supposed to be secret in symmetric key cryptography?
-The security of the encryption method should not depend on the secrecy of the algorithm but rather on the secrecy of the key. This allows for public scrutiny of the algorithm, which can help identify potential vulnerabilities.
What is the challenge of key management in symmetric key cryptography?
-As the number of communicating parties increases, the number of distinct keys required also grows significantly, creating challenges in securely managing and maintaining these keys.
Can you explain the Caesar Cipher?
-The Caesar Cipher is a substitution cipher that replaces each letter in the plaintext with another letter a fixed number of places down the alphabet. For example, with a shift of three, 'A' becomes 'D'.
What is the difference between a substitution cipher and a transposition cipher?
-In a substitution cipher, letters in the plaintext are replaced with other letters, whereas in a transposition cipher, the order of the letters is rearranged without changing the letters themselves.
What are the weaknesses of classical ciphers mentioned in the lecture?
-Classical ciphers, such as the Caesar Cipher, can be easily broken through brute-force attacks due to their limited keyspace, and they are also susceptible to frequency analysis, where patterns in letter frequency can reveal substitutions.
What are stream ciphers and block ciphers?
-Stream ciphers encrypt data bit by bit in a continuous flow, while block ciphers process fixed-size blocks of data at a time, which can require padding to ensure uniform block size.
What will be covered in the next lecture?
-The next lecture will discuss practical algorithms that are commonly used in real-world applications of cryptography, moving beyond the classical methods covered in this lecture.
Outlines

此内容仅限付费用户访问。 请升级后访问。
立即升级Mindmap

此内容仅限付费用户访问。 请升级后访问。
立即升级Keywords

此内容仅限付费用户访问。 请升级后访问。
立即升级Highlights

此内容仅限付费用户访问。 请升级后访问。
立即升级Transcripts

此内容仅限付费用户访问。 请升级后访问。
立即升级5.0 / 5 (0 votes)