Understand Azure Kubernetes Service Architecture and Components
Summary
TLDRIn this video series, the speaker introduces Azure Kubernetes Service (AKS), a powerful tool for managing containerized applications. The series covers the basics of AKS, comparing it with Google's Kubernetes, and delving into its features like RBAC, scaling, and monitoring. Over eight videos, viewers will learn to deploy, troubleshoot, and optimize AKS clusters, with a focus on making applications scalable and cloud-agnostic. The series aims to provide hands-on experience with AKS, including integration with tools like Prometheus and Grafana, and managing multi-tenant environments.
Takeaways
- 🚀 Introduction to a new series on Azure Kubernetes Service (AKS), focusing on building and understanding AKS from scratch.
- 🔄 Kubernetes (K8s) is highlighted as a crucial technology for deploying scalable, cloud-agnostic applications, overcoming challenges of bare-metal dependencies.
- 🌐 The series will cover 8 videos, focusing on key topics like understanding AKS, setting up clusters, troubleshooting, and using Azure CLI for deployment.
- 🔧 Explanation of non-Role-Based Access Control (RBAC) clusters and how to manually create AKS clusters with different configurations.
- ⚙️ Troubleshooting techniques are discussed, including diagnosing issues like pod crashes and using Azure Monitor, Log Analytics, and Application Insights.
- 💻 The series will delve into interacting with RBAC-enabled clusters using CLI, exploring concepts like nodes, pods, namespaces, and containers.
- 📊 Monitoring multi-tenant AKS clusters with tools like Prometheus and Grafana to ensure data isolation and provide customer-specific insights.
- 🔍 Integration of Grafana dashboards with Azure Active Directory and the importance of application-specific monitoring for troubleshooting.
- 💰 Discussion on cost management in multi-tenant AKS clusters, using tools like Kubecost to calculate and allocate costs based on cluster usage.
- 🔒 Emphasis on security best practices, including the use of ingress controllers and app gateways to securely route traffic within AKS clusters.
Q & A
What is the main focus of the video series mentioned in the script?
-The video series focuses on Azure Kubernetes Service (AKS), covering its features, differences from other Kubernetes services, and how to implement and troubleshoot AKS clusters.
Why did the speaker take a break before creating this new video series?
-The speaker took a break to develop content that is useful and addresses real-life challenges in executing tasks, specifically related to AKS and Kubernetes.
What is Kubernetes, and how is it beneficial for application deployment?
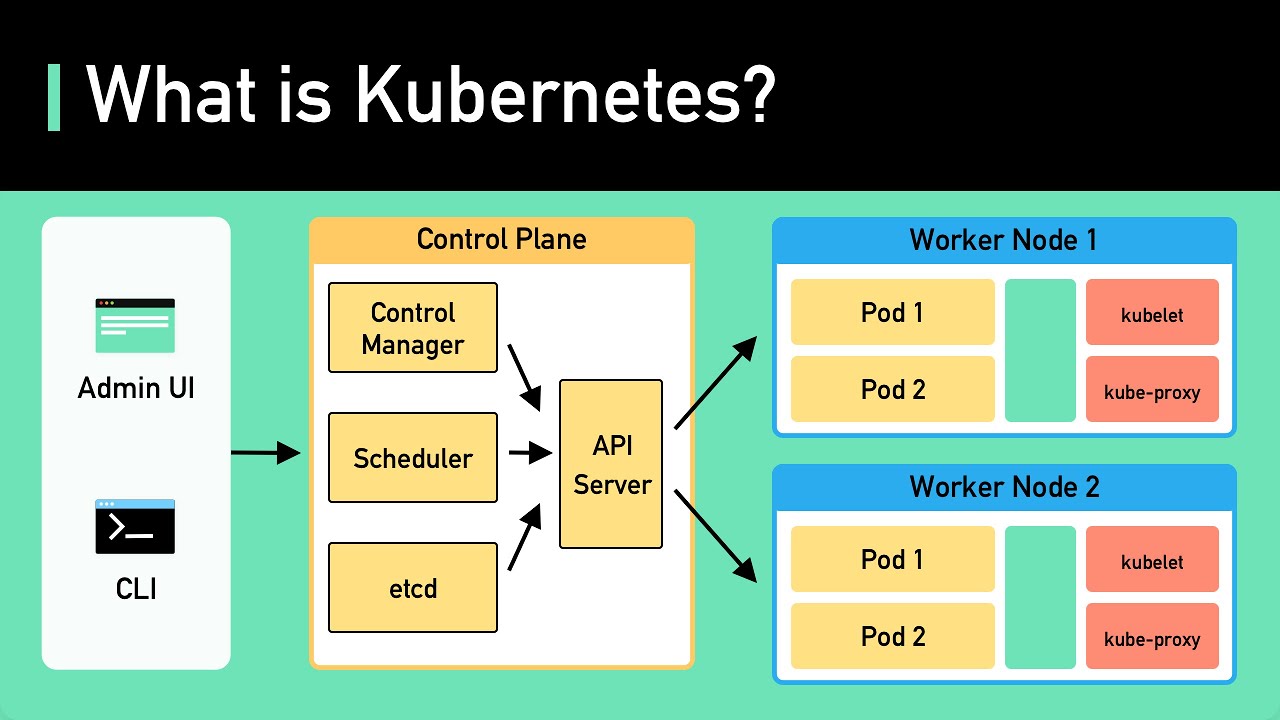
-Kubernetes is a platform for automating the deployment, scaling, and management of containerized applications. It allows for easy deployment, scaling, and management of applications, which can run on various environments like virtual machines, on-premises, or in the cloud.
How does Azure Kubernetes Service (AKS) differ from Google Kubernetes Engine (GKE)?
-AKS is managed by Azure and includes specific components like the control plane managed by Azure, while Google Kubernetes Engine (GKE) is managed by Google. The video series will explore these differences and the advantages and limitations of using AKS over GKE.
What is the purpose of creating an RBAC-enabled AKS cluster?
-An RBAC (Role-Based Access Control) enabled AKS cluster is created to manage permissions and access controls more effectively. It ensures that only authorized users can access and manage the Kubernetes resources within the cluster.
What is the significance of namespaces in Kubernetes?
-Namespaces in Kubernetes are used to logically group and isolate resources within a cluster. They help in managing and organizing the deployment of different applications and resources within a Kubernetes cluster.
What are some of the key topics covered in the video series?
-The series covers various topics, including understanding AKS, spinning up AKS clusters, troubleshooting issues, deploying clusters via the Azure portal and CLI, interacting with RBAC-enabled clusters, monitoring solutions, and cost management for multi-tenant AKS clusters.
What monitoring solutions are mentioned for AKS in the script?
-The script mentions using Azure Monitor, Log Analytics, Prometheus, and Grafana for monitoring AKS clusters. These tools help in tracking application-specific and customer-specific data, especially in multi-tenant environments.
Why is data isolation important in a multi-tenant AKS cluster?
-Data isolation is crucial in a multi-tenant AKS cluster to ensure that each tenant's data is kept separate and secure, preventing one tenant's data from being accessed by another tenant. This is important for maintaining data privacy and security.
How does the script describe handling ingress traffic in AKS?
-Ingress traffic in AKS is managed through an ingress controller, which maps DNS to the services running within the cluster. This setup ensures that external traffic is securely routed to the correct applications within the AKS cluster.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)