OSINT: How to Find Information about ANYONE!
Summary
TLDRThis video delves into Open Source Intelligence (OSINT), showcasing how to harness publicly available information for digital investigations. It covers using Google Dorks for advanced searches, exploring databases for breached data, and leveraging phone numbers and reverse image searches to uncover identities. The script also highlights social media intelligence and the importance of automating OSINT with tools like SpiderFoot, theHarvester, and Maltego to efficiently gather and analyze data.
Takeaways
- 🔎 Open Source Intelligence (OSINT) involves collecting and analyzing publicly available information.
- 🌐 OSINT tools can be used to discover a person's online presence, conduct digital investigations, and collect data for penetration testing.
- 🔍 A chart from IntelTechniques.com can guide the process of identifying someone by their real name using various data sources.
- 🏛 Governmental websites may provide public information such as voter registration, property records, court cases, or business licenses.
- 🔎 Google Dorks are special search queries that can reveal more information than typical Google searches, aiding in OSINT investigations.
- 🔗 Google Dorks can also be used on other search engines like Bing, Yandex, and DuckDuckGo for potentially different results.
- 🚨 Data breaches can expose personal information, and websites like haveibeenpwned.com and dehashed.com can help check for compromised data.
- 📞 Phone numbers can be a clue to finding a person online, with databases like whocalledme.com and tools like PhoneInfoga providing insights.
- 🖼️ Reverse image search tools like Google Images and TinEye can help discover the origin or usage of a photo on the internet.
- 📸 EXIF data in images can reveal camera model, location, date, and more, which can be useful in investigations if not removed.
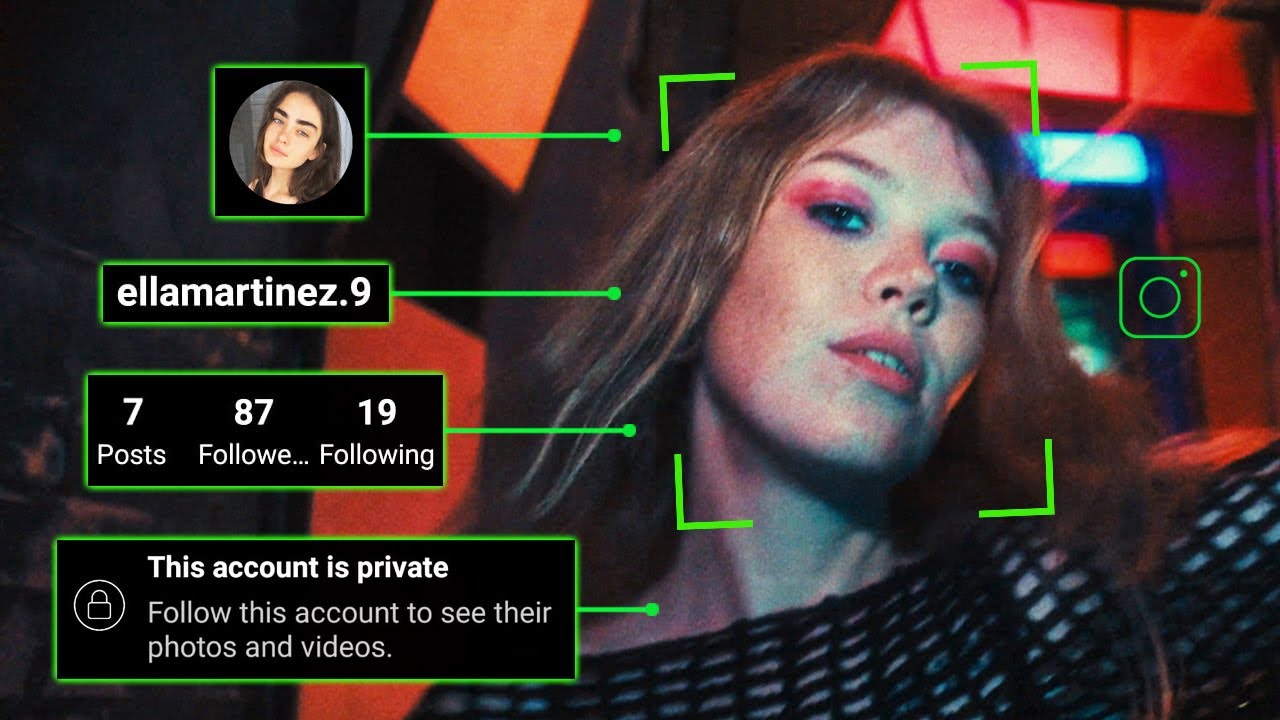
- 📈 SOCMINT, a specialized form of OSINT, focuses on extracting and analyzing data from social media platforms like Facebook.
Q & A
What is Open Source Intelligence (OSINT)?
-OSINT is the art and science of collecting and analyzing information from publicly available sources, which can be used to discover and investigate a person’s online presence, conduct digital investigations, and collect data for penetration testing.
What is the purpose of the chart from IntelTechniques.com mentioned in the script?
-The chart from IntelTechniques.com is designed to guide users through the process of identifying someone by their real name using various data sources such as governmental, commercial, and social media platforms.
What are Google Dorks and how were they discovered?
-Google Dorks are special search queries that can expose vulnerable systems or sensitive information. They were first discovered by Johnny Long in 2002 and are a powerful tool in OSINT for finding legally available information online.
How can Google Dorks be used to find someone's real name?
-Google Dorks can be used in various ways, such as searching for exact phrases on specific domains like Instagram, excluding results from the target's own account, or searching for PDF files containing certain keywords that may reveal the person's real name or personal details.
Why are data breaches significant in the context of OSINT?
-Data breaches are significant because they often result in leaked or stolen personal information being made available online. This data can include email addresses, passwords, and personal details, which can be used in OSINT to gather intelligence about individuals or organizations.
What is haveibeenpwned.com and how does it help in OSINT?
-Haveibeenpwned.com is a website created by security researcher Troy Hunt that allows users to check if their email address has been compromised in any data breaches, providing valuable information for OSINT investigations.
How can phone numbers be used as a clue to find a person online?
-Phone numbers can be searched on user-supplied databases like whocalledme.com to see if they have any comments or ratings from other users. Tools like PhoneInfoga can also scan phone numbers to gather basic information and attempt to identify the owner.
What is a reverse image search and how can it be utilized in OSINT?
-A reverse image search is a tool that allows users to upload an image or enter an image URL to find similar or identical images on the web. Tools like Google Images and TinEye can be used to discover the origin of a photo or where else it has been used, which is valuable in OSINT.
What is EXIF data and how can it be helpful in OSINT?
-EXIF data contains information such as the camera model, location, date, and more, which can be extracted from an image. This data can reveal useful insights about the image's origin and context, aiding in OSINT investigations.
What is SOCMINT and how does it differ from general OSINT?
-SOCMINT stands for social media intelligence and is a specialized form of OSINT focused on extracting and analyzing data from social media platforms. It helps in gaining insights, evidence, or leads by monitoring the interests, opinions, activities, locations, relationships, and behaviors of users.
What are some tools that can help extract useful information from Facebook for OSINT purposes?
-Tools like Exract Face can download all data from a Facebook profile or group, including posts, comments, likes, and metadata. Facebook Sleep Stats can estimate a user's sleeping patterns based on their online and offline status, providing insights into their habits and routines.
How can automation tools assist in OSINT processes?
-Automation tools like SpiderFoot, theHarvester, Recon-ng, and Maltego can help in searching, extracting, and correlating data from multiple sources. They can perform tasks such as scanning targets, gathering intelligence, and analyzing complex environments, making the OSINT process more efficient and comprehensive.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video

How to Gather Info on Someone through OSINT

Belajar Osint #1 : Investigasi Seseorang Lewat Jejak Digital with Sherlock

OSINT: how to find ALL information about ANYONE!!

Mencari Informasi Pengguna Instagram dengan OSINT | Penjelasan dan Praktek Menggunakan OSINTGRAM

Top OSINT Tools in 2024 | Are These Creepy?
SOCIAL MEDIA OSINT (private accounts)
5.0 / 5 (0 votes)