Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Summary
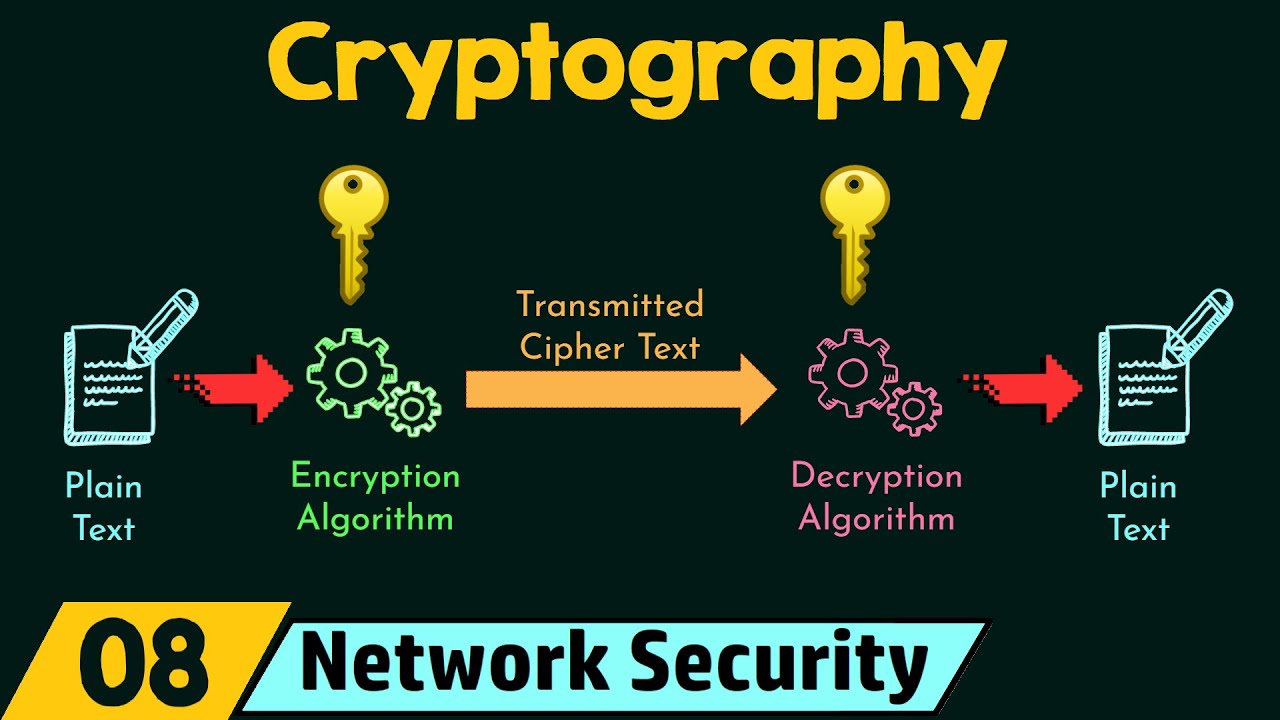
TLDRThe video script discusses Chandrashekhar Bose's cryptographic protocol, emphasizing its strength and security. It explains the process of network authentication, ticket generation, and the use of encryption to protect user details. The script also covers the integration of the protocol with company servers, ensuring secure access and data protection. The video promises a comprehensive explanation in 6-7 minutes, aiming to demystify the protocol's complexities and encourage viewers to like, subscribe, and follow for more informative content.
Takeaways
- 😀 The video script discusses Chandrabos, a network protocol, and assures a comprehensive explanation within 6-7 minutes.
- 🔒 It mentions the use of user ID and password for authentication to access and update server data securely.
- 📈 The script introduces a concept of a 'ticket' with a timestamp that is used to manage tasks and access permissions on a server.
- 🗓️ The 'ticket' is time-bound and becomes invalid after the time limit, ensuring that no unauthorized access remains on the server.
- 💼 The video explains the process of how a request is made, authenticated, and processed within a company's server environment.
- 🔐 It highlights the importance of encryption in securing the 'tickets' and the data exchanged between the client and the server.
- 🛡️ The script touches on the use of cryptographic techniques, mentioning group D and E cryptography, which are robust and support various operating systems.
- 📚 It briefly mentions the history of cryptography, including its use in Project Xanadu and its significance in network security.
- 👥 The video script implies a system where multiple entities like clients, servers, and databases interact through a secure and authenticated protocol.
- 🔄 The process described involves checking, granting permissions, and completing tasks within a specified time frame, emphasizing efficiency and security.
- 👍 The video encourages viewers to like and subscribe to the channel for more content on networking and computer science.
Q & A
What is the main topic of the video script?
-The main topic of the video script is about explaining a network protocol, possibly related to security and authentication, using Chandrbose's caret protocol as a reference.
What does the speaker promise to the audience regarding the explanation of the protocol?
-The speaker promises that they will explain the entire model of the protocol in 6 to 7 minutes without any difficulty.
What is the role of the 'Company' in the script?
-The 'Company' in the script is an entity that the speaker is employed by and works for, dealing with server storage and updates based on the company's communication.
What is the significance of 'User ID' and 'Password' in the context of the script?
-The 'User ID' and 'Password' are used for authentication and access control, allowing the user to interact with the company's servers and perform tasks.
What is the purpose of the 'Ticket' in the script?
-The 'Ticket' serves as a token that provides access to the server for a certain duration, ensuring that the user can perform tasks within the allocated time.
What happens when the 'Ticket' expires?
-When the 'Ticket' expires, it becomes invalid and any exchange on the server ceases, ensuring that the user's access is time-limited and secure.
What is the role of 'Encryption' in the script's context?
-Encryption is used to secure the 'Ticket' and the data exchanged between the user and the server, ensuring privacy and data integrity.
What is the significance of the 'Time Stamp' in the script?
-The 'Time Stamp' is used to track the duration and validity of the 'Ticket', ensuring that the user's access is time-bound and can be monitored.
What is the role of 'Group Cryptography' mentioned in the script?
-Group Cryptography, also known as 'G' Cryptography, is a strong and trendy method used for secure communication across different operating systems, supporting the protocol's security.
What is the historical context of 'Group Cryptography' mentioned in the script?
-The script mentions that 'Group Cryptography' was used in the Project Xena for secure communication and was later deprecated by Microsoft in 2000.
What does the speaker suggest at the end of the script for the audience to do if they found the video helpful?
-The speaker suggests that if the audience found the video helpful, they should like the video and subscribe to the channel for more content related to networking and computer science.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)