Single Round of DES Algorithm
Summary
TLDRThe video script provides an in-depth look into the Data Encryption Standard (DES) algorithm, focusing on the single round function. It begins with an overview of the DES encryption process, which transforms a 64-bit plaintext into ciphertext through a series of permutations, substitutions, and key-based operations. The script explains the initial permutation, where the input text's bit positions are rearranged, and the inverse initial permutation, which reverses this process. The swap function is also discussed, highlighting its role in exchanging the left and right 32 bits of the text. The core of the presentation is the single round function, which takes a 64-bit input and a 48-bit round key, performing an expansion permutation, substitution through S-boxes, and transposition to produce a new 64-bit output. The round key is derived from the original 56-bit key through a left circular shift operation. The script concludes with a teaser for the next presentation, which will delve into the specifics of the function F within each round. Overall, the script offers a clear and engaging explanation of the DES algorithm's encryption process, piquing the interest of viewers in the intricacies of data security.
Takeaways
- 🗝️ The DES (Data Encryption Standard) algorithm is a symmetric-key encryption algorithm that converts a 64-bit plaintext into a 64-bit ciphertext.
- 🔄 The DES process involves an initial permutation, 16 rounds of processing with round keys, a swap function, and an inverse initial permutation.
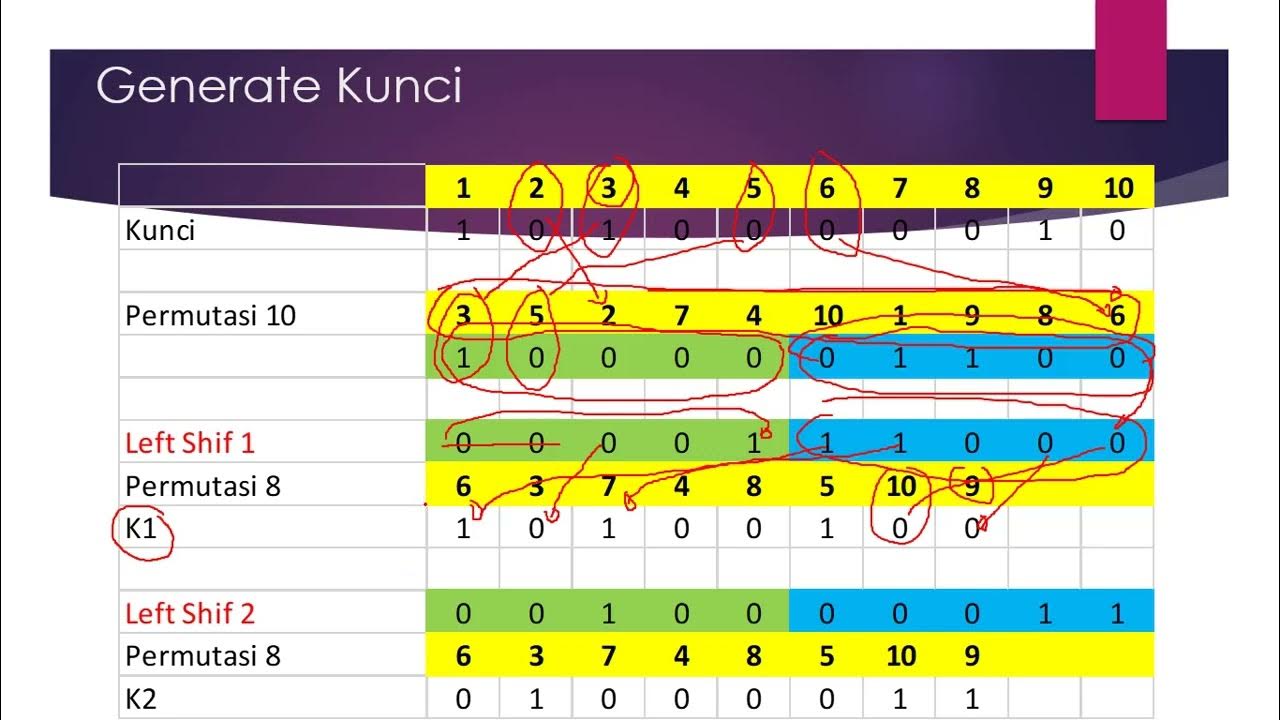
- 🔑 The original 64-bit key is reduced to a 56-bit key, which is then further processed to generate 48-bit round keys for each of the 16 rounds.
- 🔄 The initial permutation rearranges the 64-bit plaintext, and the inverse permutation does the same to the ciphertext before it is output.
- 🔄 The swap function exchanges the left and right 32-bit halves of the data after all 16 rounds of processing.
- 🔑 Each round of DES encryption uses a unique 48-bit round key derived from the original 56-bit key through a left circular shift operation.
- 🔍 In each round, the right 32 bits of the input are expanded to 48 bits to match the round key size, then processed through substitution and permutation boxes.
- 🔄 The output of each round is a new 32-bit left half and a new 32-bit right half, which become the input for the next round.
- 🔗 The left and right halves are XORed within each round to produce the output for that round.
- 🔍 The 'F function' or 'mangler function' is a key part of each round, which will be explained in more detail in a subsequent presentation.
- 🎓 The presentation aims to help learners understand the steps involved in a single round of the DES algorithm, including initial and inverse permutations and the swap function.
Q & A
What is the main topic of the presentation?
-The main topic of the presentation is the single round of the DES (Data Encryption Standard) algorithm.
What are the two key outcomes expected from the session?
-The two key outcomes are understanding the initial permutation, inverse initial permutation, and the swap function, and understanding the single round of the DES algorithm.
How does the initial permutation function work?
-The initial permutation function takes a 64-bit plaintext, changes the position of the bits, and outputs a 64-bit text.
What is the role of the round key in the round function?
-The round key, which is 48 bits, is used in conjunction with the right side of the 64-bit input to the round function. It is combined with the expanded 48 bits from the right side of the input through an XOR operation.
How many rounds are there in the DES algorithm?
-There are 16 rounds in the DES algorithm.
What happens to the right side of the 64-bit input in the round function?
-The right side of the 64-bit input, which is 32 bits, is expanded into 48 bits using an expansion function before being combined with the 48-bit round key.
What is the purpose of the expansion permutation?
-The expansion permutation is used to convert the 32 bits into 48 bits so that it can be combined with the 48-bit round key via an XOR operation.
What is the swap function's role in the DES algorithm?
-The swap function takes the 64-bit output from the last round and swaps the left 32 bits with the right 32 bits before it is passed to the inverse initial permutation function.
How does the DES algorithm produce its 56-bit key from the original 64-bit key?
-The original 64-bit key is reduced to 56 bits by a process that involves a left circular shift operation, and then the 56-bit key is used to derive the 48-bit round keys.
What is the final step after the 16 rounds of processing in the DES algorithm?
-The final step is to pass the 64-bit output from the swap function to the inverse initial permutation function, which changes the position of the bits to produce the final 64-bit ciphertext.
What is the F function or Mangler function in the context of the DES algorithm?
-The F function, also known as the Mangler function, is a part of the DES algorithm that takes the right side of the input and the round key as inputs and performs operations including expansion, XOR with the round key, substitution using S-boxes, and permutation using a P-box.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video
5.0 / 5 (0 votes)