Exploiter les failles upload PHP (Magic Byte, .htaccess...)
Summary
TLDRThis educational video demonstrates how attackers can exploit file upload vulnerabilities on PHP-based web servers, specifically focusing on a Symfony application running in Docker. It covers various methods of exploiting file upload flaws, such as bypassing content type checks, manipulating file extensions, and using techniques like magic bytes and .htaccess files to execute PHP code. The video also provides tips on securing file uploads, including using a whitelist for allowed extensions, limiting file sizes, and storing files in directories that aren't publicly accessible. It's a comprehensive guide to understanding and preventing file upload vulnerabilities.
Takeaways
- 😀 File upload vulnerabilities in PHP servers can be critical, allowing attackers to execute arbitrary code and potentially compromise the entire server.
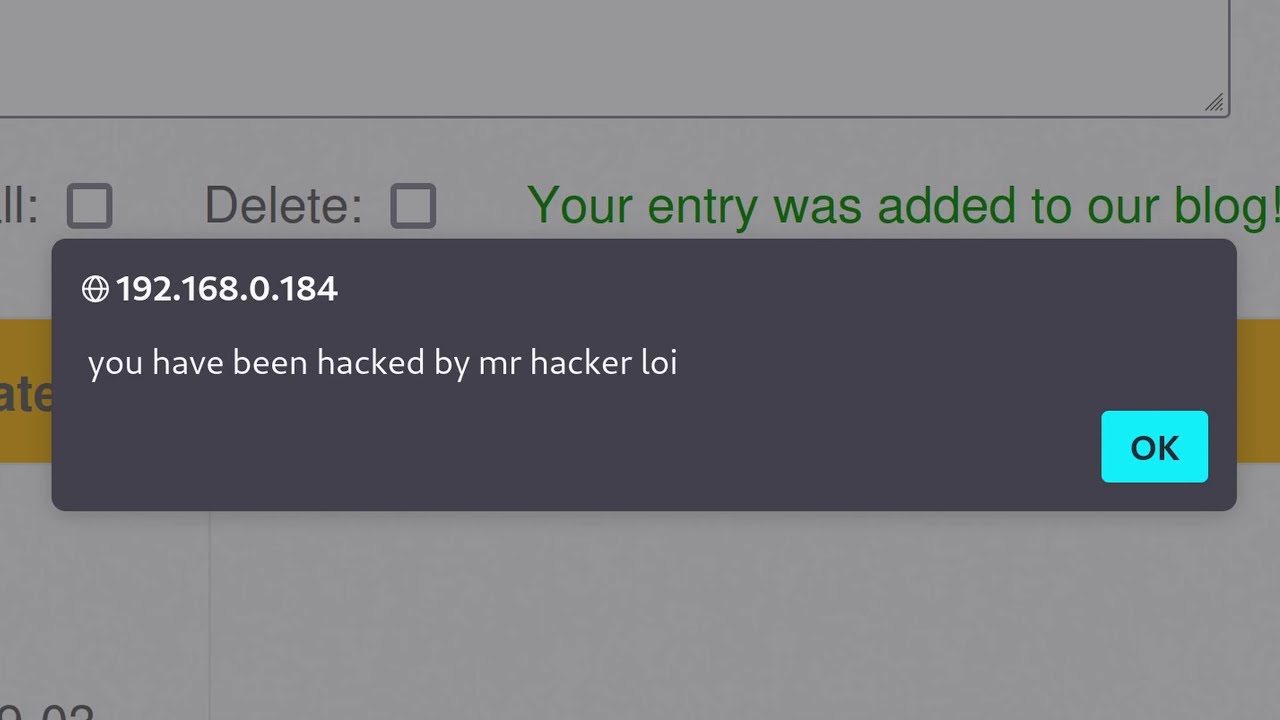
- 😀 Testing and exploiting file upload vulnerabilities involves uploading a PHP file and executing system commands via the server's file upload mechanism.
- 😀 Ensure that file upload directories are properly secured to prevent access to uploaded files, especially when using public directories.
- 😀 The simplest vulnerability occurs when there is no protection at all, allowing files like PHP scripts to be uploaded without restrictions.
- 😀 Tools like Burp Suite can be used to monitor HTTP requests and modify file upload attempts, helping to identify vulnerabilities.
- 😀 Verifying file content type (such as 'image/jpeg') is a basic method of protecting file uploads from malicious files, though attackers can bypass this by modifying the content type in their request.
- 😀 If the server doesn't verify the content type accurately, attackers can exploit this by changing the content type in the request headers to something acceptable (e.g., 'image/jpeg').
- 😀 Another common protection mechanism is verifying file extensions, but attackers can bypass this by renaming files or using techniques like null byte injection.
- 😀 Magic bytes, which are specific byte sequences at the beginning of a file, can be manipulated to make a file appear as an acceptable type (e.g., JPEG) while it contains malicious code.
- 😀 Advanced protections like using .htaccess files can allow attackers to bypass extension-based security checks, allowing PHP code to be executed despite the file extension being '.jpg'.
- 😀 To secure file uploads, it's essential to use a whitelist of allowed file extensions, verify file size, store files in non-public directories, and avoid relying solely on extension checks.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade Now5.0 / 5 (0 votes)