XDR Implementation And AI Use Cases
Summary
TLDRThe panel discussion explores the evolution and necessity of Extended Detection and Response (XDR) in cybersecurity, contrasting it with traditional antivirus solutions. Panelists emphasize the holistic approach of XDR, which integrates various security tools for comprehensive threat detection and response. They discuss challenges in implementing XDR, such as legacy system compatibility and cost, and highlight the role of AI and ML in enhancing XDR's effectiveness. The conversation also touches on the importance of adapting security strategies to protect against modern threats, including ransomware attacks on mobile devices.
Takeaways
- 🔒 The security landscape is evolving, necessitating the development of more advanced security tools such as XDR (Extended Detection and Response).
- 🛠️ Traditional antivirus solutions are no longer sufficient to address modern cybersecurity threats, leading to the adoption of EDR (Endpoint Detection and Response) and XDR.
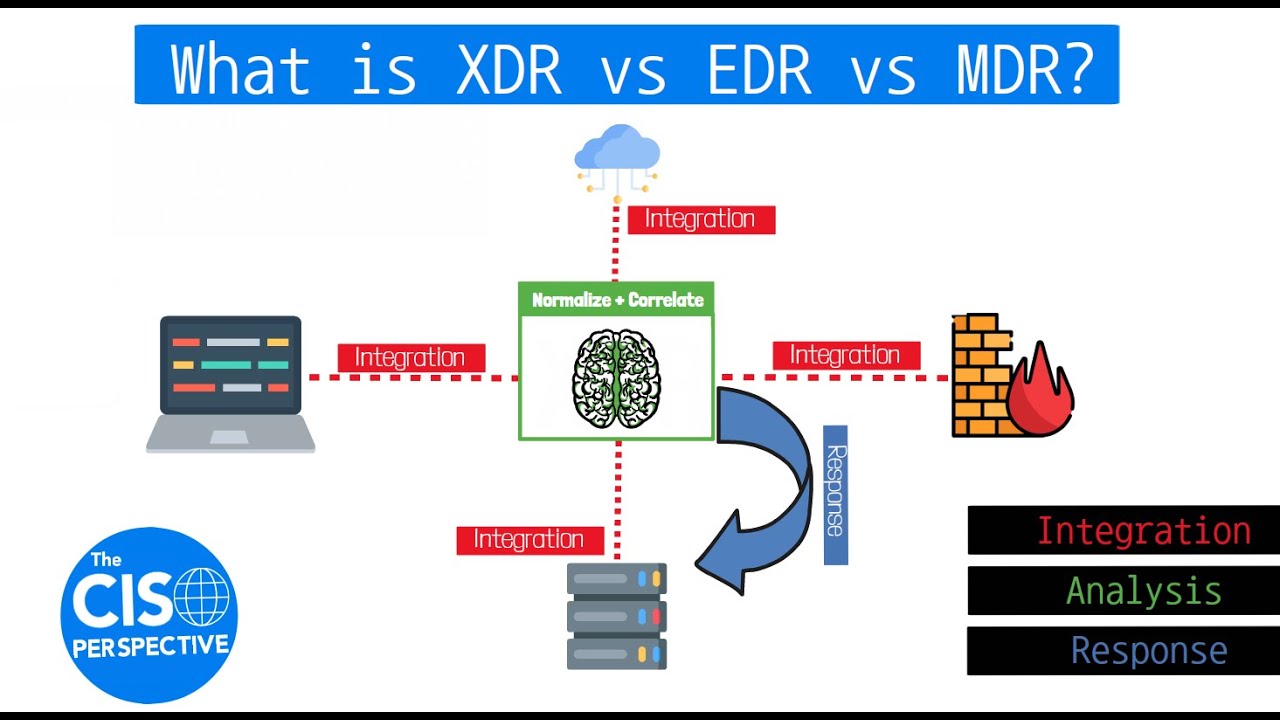
- 🌐 XDR provides a comprehensive view by integrating with various security tools, offering a single pane of glass for visibility across the IT ecosystem.
- 💡 The implementation of XDR is crucial for organizations with a large number of assets, as it aids in reducing the cost and effort of manual monitoring.
- 📈 The use of AI and ML in XDR solutions enhances their effectiveness by providing actionable insights and automating responses to security incidents.
- 🚀 Cloud-native XDR components are emerging, offering native capabilities and extending their reach to other platforms like IoT and OT.
- 💼 The transition to XDR requires a change in mindset, particularly among organizational boards, to recognize its value over traditional antivirus solutions.
- 🏗️ Legacy systems can pose a significant challenge to the implementation of XDR due to their limited capacity to support advanced security solutions.
- 🔍 XDR can help detect and respond to abnormal behaviors, such as unusual data transfers or access patterns, by correlating data from various sources.
- ⏰ Timely response to security incidents is critical, and XDR solutions can automate these responses, providing a proactive approach to cybersecurity.
Q & A
What is XDR and how has it evolved from traditional security solutions?
-XDR, or Extended Detection and Response, is a comprehensive security solution that evolved from traditional siloed security tools like antivirus, IDS, and IPS. It provides a holistic view of an organization's security posture by integrating data from various security tools, including endpoint, network, cloud, and email servers, to detect and respond to threats more effectively.
Why is XDR considered an improvement over EDR and NDR?
-XDR is considered an improvement over EDR (Endpoint Detection and Response) and NDR (Network Detection and Response) because it offers a unified platform that correlates data from multiple security layers, providing a single pane of glass for visibility. This allows for more effective detection of threats and faster response times, as opposed to the isolated approach of EDR and NDR.
What are the challenges in implementing XDR in an organization?
-Implementing XDR can be challenging due to several factors, including the integration with legacy systems, deciding on the deployment location, and the mindset change required from the board members. Legacy systems may not have the capacity to support XDR, and the board may be resistant to adopting a more advanced and costly solution compared to traditional antivirus software.
How does XDR help in reducing security costs?
-XDR helps in reducing security costs by automating threat detection and response, thereby reducing the need for manual monitoring. It provides a centralized view of security incidents, making it easier to manage and respond to threats, which can lead to cost savings in the long run.
What role does AI and ML play in XDR solutions?
-AI and ML play a significant role in XDR solutions by enabling the system to learn and adapt to normal and abnormal behaviors within the organization. They can help in detecting anomalies, automating responses to security incidents, and improving the overall effectiveness of the XDR platform.
Can you provide an example of how XDR can detect abnormal behavior within an organization?
-An example of XDR detecting abnormal behavior could be a sudden large data transfer from the network to an external source that deviates from the normal behavior. XDR, by integrating with network and endpoint security, can identify such anomalies and provide actionable insights for security teams to respond accordingly.
What are some use cases where XDR can be beneficial for an organization?
-XDR can be beneficial in various scenarios, such as detecting and responding to sophisticated phishing attacks, identifying unauthorized access to sensitive information, and providing a comprehensive view of the security posture across different platforms, including IoT and OT networks.
How does XDR help in managing security incidents?
-XDR helps in managing security incidents by providing a centralized platform that correlates data from various security layers. This allows security teams to have a complete view of an incident, making it easier to investigate and respond to threats more effectively.
What is the importance of a single pane of glass in XDR solutions?
-The single pane of glass in XDR solutions is crucial as it provides a unified view of an organization's security posture, enabling security teams to monitor, detect, and respond to threats in real-time across all security layers, which improves the efficiency and effectiveness of security operations.
How does XDR integrate with cloud-native security tools?
-XDR integrates with cloud-native security tools by leveraging APIs and other integration methods to collect and correlate data from cloud platforms like GCP, AWS, and Azure. This allows for a comprehensive view of security incidents across both on-premises and cloud environments.
Outlines

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowMindmap

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowKeywords

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowHighlights

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowTranscripts

This section is available to paid users only. Please upgrade to access this part.
Upgrade NowBrowse More Related Video
What is XDR vs EDR vs MDR? Breaking down Extended Detection and Response

8 XDR Benefits You Need to Know About

Microsoft Defender for Business EDR to XDR Security Upgrade Using Microsoft 365 Business Premium

Microsoft 365 Defender for Endpoint? Good Enough for your Business?

Enterprise Grade Protection for Small & Medium Businesses | Microsoft Defender for Business

Naučte se přežít ransomware
5.0 / 5 (0 votes)