Understanding the OSI Model - N10-008 CompTIA Network+ : 1.1
Summary
TLDRThe script discusses the OSI model, a foundational framework in IT for understanding network communication. It covers the seven layers, from physical to application, and their roles in data transmission. Mnemonics and real-world applications are used to illustrate the model's practicality, emphasizing its importance in IT communication and troubleshooting.
Takeaways
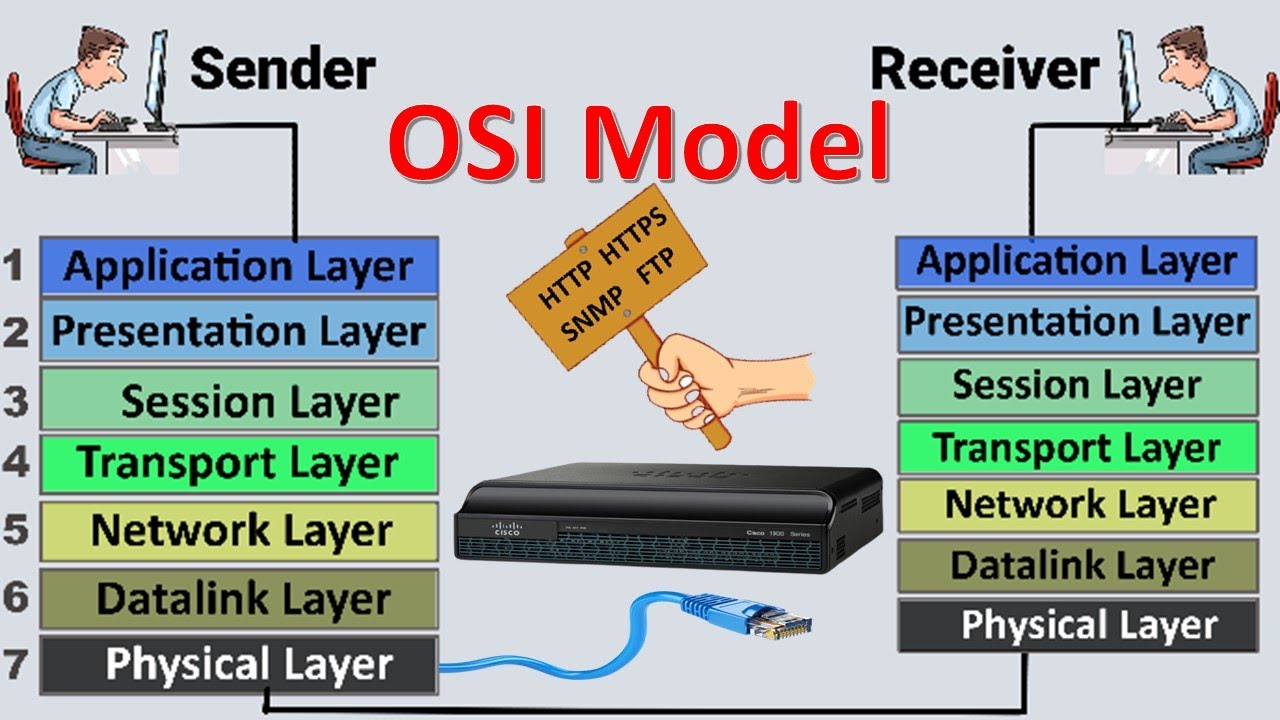
- 🌐 The OSI model stands for Open Systems Interconnection Reference Model and is a guideline to describe how data moves across a network.
- 📚 The OSI model is used as a common language among IT professionals to understand and communicate about network data flow.
- 🔍 Despite the OSI protocols not being widely adopted, the OSI model itself continues to be a reference in IT discussions.
- 🔑 The OSI model consists of seven layers, each with its own set of protocols that may vary depending on the network traffic.
- 🧠 A mnemonic to remember the OSI layers is 'All People Seem To Need Data Processing', corresponding to Application, Presentation, Session, Transport, Network, Data Link, and Physical layers.
- 🌟 The Physical layer (Layer 1) deals with the actual cables and physical connections, focusing on the signaling over network connections.
- 🔗 The Data Link layer (Layer 2) is foundational, using protocols like MAC addresses for communication and is often referred to as the 'switching' layer.
- 🌐 The Network layer (Layer 3) is associated with IP addresses and is crucial for routing decisions, also handling data fragmentation.
- 🚛 The Transport layer (Layer 4) is often called the 'post office' layer, managing data delivery using protocols like TCP and UDP.
- 🗣️ The Session layer (Layer 5) manages the start and stop of communication between endpoints, using control or tunneling protocols.
- 🔒 The Presentation layer (Layer 6) handles data formatting for user understanding, including character encoding and data encryption.
- 🖥️ The Application layer (Layer 7) is what users interact with, such as web browsers, and uses protocols like HTTP, HTTPS, FTP, and DNS.
Q & A
What is the OSI model and why is it important in IT?
-The OSI model stands for Open Systems Interconnection Reference Model. It's a guideline that describes how data moves across a network, allowing IT professionals to communicate effectively about network processes and issues.
Why did the OSI protocols not become widely adopted despite the OSI model's popularity?
-The OSI protocols themselves did not catch on, likely due to competition with other protocols like TCP/IP, which became the standard for network communication. However, the OSI model's framework remains valuable for understanding network communication layers.
How many layers does the OSI model consist of, and what is the purpose of each layer?
-The OSI model consists of 7 layers, each with a specific purpose: the physical layer (Layer 1) for signaling and cabling, the data link layer (Layer 2) for local network communication, the network layer (Layer 3) for routing based on IP addresses, the transport layer (Layer 4) for data delivery, the session layer (Layer 5) for establishing communication sessions, the presentation layer (Layer 6) for data representation, and the application layer (Layer 7) for user interactions with applications.
What is a mnemonic that can help memorize the OSI model layers?
-The mnemonic 'All People Seem To Need Data Processing' can be used to remember the OSI model layers, with each word's initial corresponding to the layers from top to bottom: Application, Presentation, Session, Transport, Network, Data Link, and Physical.
What are some common issues that might be investigated at the physical layer of the OSI model?
-At the physical layer, issues might include problems with cabling, punch-down connections, and signal transmission. Troubleshooting might involve checking cables, running loopback tests, or swapping adapter cards.
How does the data link layer (Layer 2) contribute to network communication?
-The data link layer is foundational for network protocols and uses MAC addresses for local network communication. It's often referred to as the 'switching' layer because switches make forwarding decisions based on MAC addresses.
What is the role of the network layer (Layer 3) in routing and data transmission?
-The network layer is responsible for routing based on IP addresses and for fragmenting data into smaller pieces to move between different types of networks, such as between an Ethernet and a WAN network.
What protocols are commonly used at the transport layer (Layer 4), and what are their functions?
-TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are commonly used at Layer 4. TCP ensures reliable data delivery, while UDP is used for faster, less reliable delivery.
How does the session layer (Layer 5) facilitate communication between network endpoints?
-The session layer is responsible for establishing, managing, and terminating communication sessions between network endpoints. It uses control and tunneling protocols to initiate data transfer.
What types of data processing occur at the presentation layer (Layer 6)?
-The presentation layer is involved in character encoding, data formatting, and encryption of application data. It ensures that data is presented in a form that can be understood by the application layer.
Can you describe the application layer (Layer 7) and its significance in user interactions?
-The application layer is the topmost layer of the OSI model and is responsible for providing the interface between the user's application programs and the network. It includes protocols for email, file transfer, and web services, making it critical for user interactions with applications like web browsers and email clients.
How can the OSI model be practically applied using a packet capture tool like Wireshark?
-In a packet capture tool like Wireshark, the OSI model can be applied to analyze network traffic by breaking down each frame into its respective OSI layer components. This allows IT professionals to examine the details of network communication at each layer, from physical signaling to application data.
Outlines

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифMindmap

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифKeywords

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифHighlights

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифTranscripts

Этот раздел доступен только подписчикам платных тарифов. Пожалуйста, перейдите на платный тариф для доступа.
Перейти на платный тарифПосмотреть больше похожих видео

Understanding the OSI Model - CompTIA Network+ N10-009 - 1.1

Animasi Komunikasi Data Pada OSI Layer (2022) | Produk PBL - Team Illustry

Understanding the OSI Model - CompTIA Network+ N10-007 - 1.2
OSI Model | OSI Model Explained | OSI Animation | OSI Model in easiest Way | OSI 7 Layers

OSI and TCP IP Models - Best Explanation

OSI Model
5.0 / 5 (0 votes)
