Memahami Enkripsi!
Summary
TLDRThis script delves into the world of encryption and decryption, explaining their necessity in daily life and internet communication. It illustrates how data travels securely through various networks, the importance of HTTPS, and the concept of symmetric vs. asymmetric encryption. The RSA algorithm is introduced, highlighting its use of prime numbers to generate public and private keys, enhancing security. The script also touches on the computational efficiency of symmetric encryption like AES, the use of session keys, and digital signature for message authentication, providing a comprehensive overview of secure data transmission.
Takeaways
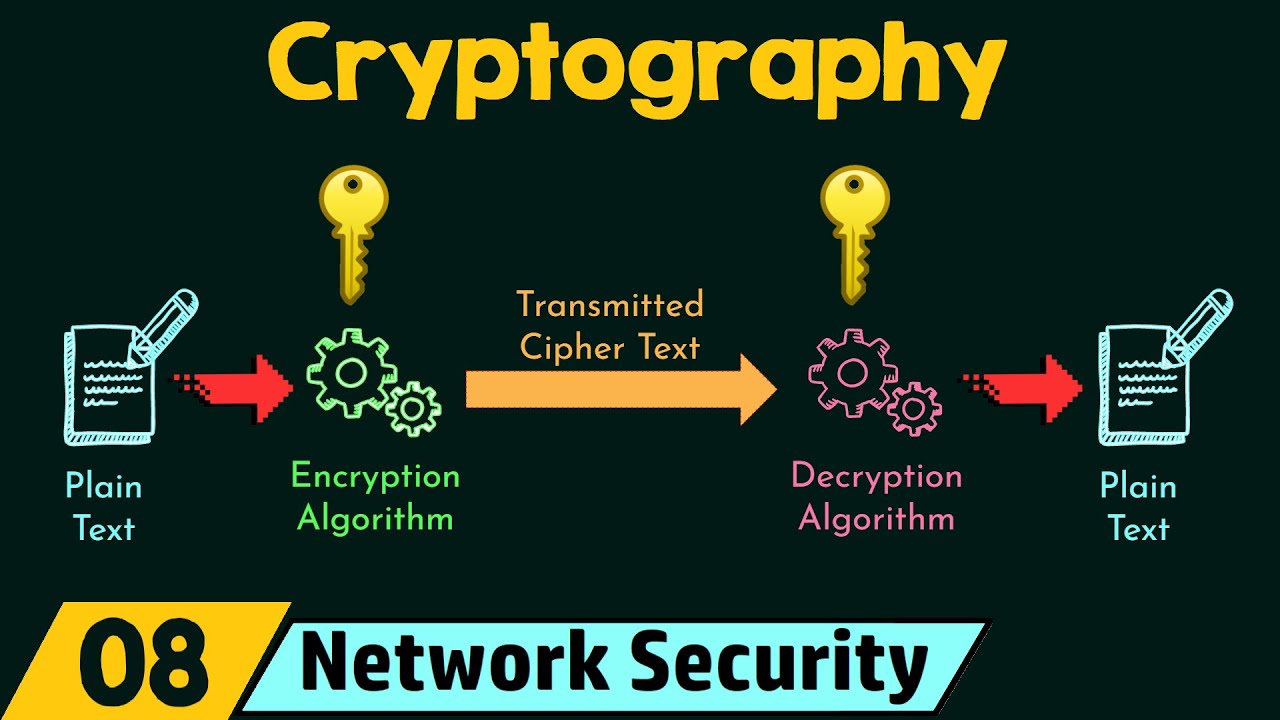
- 🔒 Encryption is the process of transforming plain text into coded text to protect information, ensuring only the intended recipient can decrypt it.
- 🌐 When data is sent over the internet, it travels in packets through various routers, and encryption is crucial to protect this data in transit.
- 🔒🔑 Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a public key for encryption and a private key for decryption.
- 🔑🔒 In asymmetric encryption, the public key can be used by anyone to encrypt a message, but only the corresponding private key can decrypt it.
- 🔑🔐 Each user in an asymmetric encryption system has two keys: a public key that can be shared openly and a private key that must be kept secret.
- 🔑🔄 The RSA algorithm is a popular method used in public-key cryptography, which involves the use of prime numbers to generate the keys.
- 🔢🔑 Prime numbers are essential in cryptography because they are difficult to factorize, making it challenging for an attacker to derive the private key through brute force.
- 🔒🔄 AES (Advanced Encryption Standard) is a symmetric encryption algorithm widely used for secure data exchange, as it is less computationally intensive than asymmetric encryption.
- 🔗🔑 In practice, a combination of symmetric and asymmetric encryption is often used: asymmetric encryption to securely exchange a symmetric session key, followed by symmetric encryption for the actual data transfer.
- 📦🔒 The concept of a 'session key' is used in secure communication protocols, which is a temporary symmetric key used for a specific communication session and then discarded.
- 📜🖋️ Digital signatures, created by encrypting a message with the sender's private key, provide a way to authenticate the origin of a message, ensuring its integrity and non-repudiation.
Q & A
What is encryption and why is it necessary?
-Encryption is the process of transforming readable text into coded text to protect data from unauthorized access. It is necessary to secure data transmission over the internet and to ensure privacy and data integrity.
How does data travel through the internet?
-Data travels in packets through various routers and internet service providers (ISPs) to reach its destination. It can take different paths, and the data is encrypted to maintain privacy and security during transit.
What does the 'S' in HTTPS stand for and why is it important?
-The 'S' in HTTPS stands for 'Secure,' indicating that the communication is encrypted. It is important because it ensures that the data being transmitted is protected from eavesdropping and tampering.
How does encryption work in the context of sending a message?
-Encryption works by adding a key to the original message, turning it into a coded text. Only the intended recipient, who has the correct key, can decrypt the message back to its original form.
What is the difference between symmetric and asymmetric encryption?
-Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys, one public and one private. The public key is used to encrypt data, and the private key is used to decrypt it.
How does the RSA algorithm use prime numbers to generate public and private keys?
-The RSA algorithm uses the product of two large prime numbers to generate a public key. The private key is derived from one of the prime factors of this product. The security of RSA relies on the difficulty of factoring the product of these prime numbers.
Why are prime numbers important in the context of encryption?
-Prime numbers are important because they are the building blocks of the RSA algorithm. The difficulty of factoring large prime numbers makes it computationally hard for an attacker to derive the private key from the public key.
What is a session key and how is it used in secure communication?
-A session key is a symmetric key used for encrypting messages during a specific communication session. It is often exchanged using public-key cryptography at the beginning of a session, allowing both parties to securely exchange data without further key exchange.
How does the size of the key affect the security and performance of encryption?
-Larger key sizes, such as 2048 bits for public-private key pairs, offer higher security but require more computational resources and time for encryption and decryption. Smaller symmetric keys, like 256 bits, are less computationally intensive and can provide a similar level of security.
What is digital signature and how does it ensure the authenticity of a message?
-A digital signature is a cryptographic mechanism that verifies the authenticity of a message. The sender encrypts the message with their private key, and the recipient can decrypt it using the sender's public key, confirming that the message came from the claimed sender.
Why are symmetric encryption algorithms like AES preferred for large data transfers?
-Symmetric encryption algorithms like AES are preferred for large data transfers because they are computationally efficient and fast. They use a single key for both encryption and decryption, which is less resource-intensive compared to asymmetric encryption.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード5.0 / 5 (0 votes)