Multifactor Authentication - CompTIA Security+ SY0-701 - 4.6
Summary
TLDRThe script discusses various authentication factors used for secure logins, including 'something you know' like passwords and PINs, 'something you have' such as smart cards and USB security keys, 'something you are' involving biometrics, and 'somewhere you are' using location data. It highlights the importance of combining these factors for robust security, noting the rise of software tokens and the potential pitfalls of relying solely on biometrics.
Takeaways
- 🔐 Username and password are common authentication factors for logging into websites.
- 📱 Mobile apps can provide pseudo-random codes or use GPS location as part of the login process.
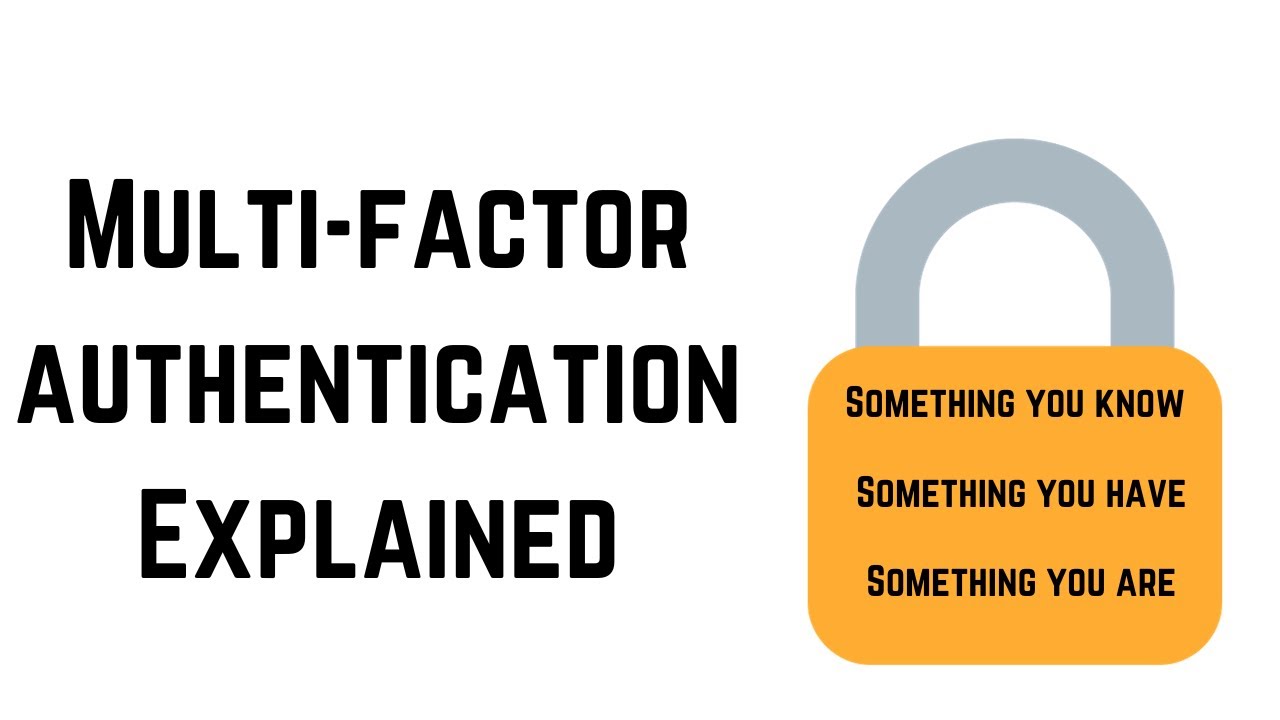
- 🔑 Authentication factors are categorized as something you know, have, are, or somewhere you are.
- 🤔 'Something you know' includes passwords, PINs, and patterns, which are memorized and known only to the user.
- 🏢 'Something you have' could be a smart card, USB security key, or hardware token that verifies your identity.
- 📲 Software tokens and SMS codes sent to your mobile phone can also serve as 'something you have' for authentication.
- 👤 'Something you are' refers to biometric authentication like fingerprints or voiceprints, which are unique to the individual.
- 📊 Biometric data is stored as a mathematical representation rather than the actual biometric sample.
- 🌐 'Somewhere you are' uses location data, such as GPS or IP addresses, to authenticate users based on their geographical location.
- 🔄 Multiple authentication factors are often used together to enhance security and prevent unauthorized access.
- 📍 Geolocation services can combine IP addresses and GPS coordinates to determine a user's physical location for authentication purposes.
Q & A
What are authentication factors?
-Authentication factors are different types of login parameters used to verify the identity of a user, such as something you know, something you have, something you are, or somewhere you are.
What is 'something you know' in the context of authentication factors?
-'Something you know' refers to information that only the user is aware of, such as a password, a personal identification number (PIN), or a pattern to unlock a device.
Can you provide an example of 'something you have' authentication factor?
-An example of 'something you have' is a USB security key that contains a certificate specific to the user, which must be plugged in to authenticate.
How does a hardware token work as an authentication factor?
-A hardware token generates a seemingly randomized set of numbers that are duplicated on the server, and the user must input this number during the login process along with their username and password.
What is the role of biometric authentication in the 'something you are' category?
-Biometric authentication uses unique personal traits like fingerprints or voiceprints as an authentication factor, storing a mathematical representation of the biometric for verification.
Why might 'something you are' be used in conjunction with other authentication factors?
-'Something you are' is often used with other factors because biometrics can potentially be circumvented, adding an extra layer of security.
What is the concept of 'somewhere you are' as an authentication factor?
-'Somewhere you are' uses location information, such as GPS coordinates or IP address, to determine if the login attempt is from a recognized location.
How can the location information from a mobile device be used for authentication?
-The location information from a mobile device can be used to verify if the login attempt is from a location consistent with the user's usual whereabouts, adding a layer of security.
What is the difference between storing a biometric image and its mathematical representation?
-Storing a biometric image involves saving the actual picture, while a mathematical representation involves saving a unique set of data derived from the biometric, which is used for comparison during authentication.
How does the use of SMS or text messages as an authentication factor work?
-SMS or text messages can be used to send a code to the user's phone, which they then enter during the login process as an additional verification step.
Why might the authentication process use multiple location services?
-Using multiple location services, such as IP address and GPS coordinates, can provide a more accurate and comprehensive understanding of a user's physical location, enhancing the security of the authentication process.
Outlines

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードMindmap

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードKeywords

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードHighlights

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレードTranscripts

このセクションは有料ユーザー限定です。 アクセスするには、アップグレードをお願いします。
今すぐアップグレード関連動画をさらに表示
Multi Factor Authentication Explained In Cyber Security

What is Two-Factor Authentication? (2FA)

How to configure Spring Security Authentication - Java Brains

Security / Keamanan - Distributed System / Sistem Terdistribusi

Cybersecurity: Crash Course Computer Science #31

Everyone Plays a Role in “If You See Something, Say Something®”
5.0 / 5 (0 votes)
